by Barbora Hrdá (Fraunhofer AISEC)
Quantum technologies are seen as a great opportunity for a wide variety of fields: from optimization problems to machine learning and encryption, many use cases are always cited to produce revolutionary things. In order to make quantum computing widely applicable, more and more quantum platforms are easily accessible for everyone via cloud interfaces. The data and algorithms running on these systems are important assets that need to be protected. But who ensures the confidentiality and integrity of data running on quantum computers?
Today’s quantum computers are room-filling machines requiring a lot of effort to keep qubits in a lowenergy state. Access to quantum computers is mainly gained via online platforms providing, for example, a programming environment for the corresponding hardware. Algorithms and data that are processed on these platforms are valuable assets. In order to make quantum computing widely applicable, foundations must be laid for not only an easy, but also trustworthy use. To achieve this, the project “Secure Quantum Computing Platforms” led by Fraunhofer AISEC is researching methods to ensure the confidentiality and integrity of users’ data processing on quantum hardware and quantum computing (QC) platforms. The project’s goal is to run confidential data and its processing securely on third-party quantum computing hardware without allowing an attacker, e.g., a malicious operator, to gain unauthorized access.
Imagine a pharma company developing a new drug. To that end a quantum algorithm is implemented for the simulation of a molecule representing the critical part of the drug. The structure of the molecule, which is the company´s intellectual property, might be transferred directly to the QC platform or encoded in the algorithm. The damage to the company if, during the processing, this intellectual property was stolen, would be immense.
The most common access method to a quantum computer is usually through a QC platform. Typically, a programming environment for the user’s input and quantum circuits is provided, sometimes an SDK can be downloaded, and the programming environment can be run locally. After submitting code to the platform, various pre-processing steps (e.g., compiling and optimisation) are carried out before the processed data and instructions are scheduled for the quantum hardware. They are forwarded to a control computer and finally, depending on the architecture, converted from bits to, for example, pulse instructions and sent to the actual quantum hardware. The results of the computation are then returned to the user via the QC platform. But how is data in this process protected from unauthorized access and falsification?
The transmission of data from a local machine to the QC platform is a first possible point of attack. Today, communication between the local machine and the QC platform takes place using common encrypted protocols. In addition, authentication codes can be used to detect manipulations in the transmission and ensure the integrity of the transmitted data. But what about the processing of data, the so-called data-in-use?
Since protecting data-in-use on quantum computers is an unsolved problem, we are investigating different approaches similar to security measures that are being researched and applied today in the area of cloud computing. In cloud computing, data is also transferred to an untrusted server for storage and processing, and the operator of cloud servers is not trusted. Instead, sensitive data is isolated as far as possible from the operator’s access during processing. To this end, attempts are being made to achieve security using protected enclaves that allow only authorized programming code to process and access the data to be processed. This is what we commonly call Confidential Computing.
On the road to Confidential Quantum Computing, we are investigating different security approaches, which isolate data from the operator’s access in a similar way to confidential computing, but also take quantum server specific properties in consideration.
One approach on this road is Blind Quantum Computing (BQC) [1]. BQC considers securely delegating quantum computation and data to one, or several, untrusted quantum servers, while maintaining the integrity and confidentiality of the data. The goal is to keep the client’s input, computation, circuits, and output hidden from the quantum server during processing. When using several untrusted quantum servers, the data is split in several subtasks and these subtasks are delegated to different servers. Thus, in the event of a confidentiality breach on one of the quantum servers, the attacker receives only a fraction of the information. Many protocols also integrate some form of verification, i.e., they ensure the correctness of the returned result.
Another approach is to use Homomorphic Encryption, in which specific calculations can be performed on an encrypted cipher text corresponding to mathematical operations on the decrypted plaintext. This allows encrypted data to be processed without having to decrypt it [2]. First applications of Homomorphic Encryption for quantum circuits have already been investigated [3].
These are only two approaches addressing the lack of confidentiality and integrity for computations on untrusted quantum servers and finding a solution to this problem is essential for the acceptance of quantum computing. Building on these approaches, we want to examine which existing protocols can be applied out of the box, as well as which combination possibilities arise from different approaches and where there is still a need for further development in order to address the security requirements for QC platforms in the best way possible.
The goal of the project “Secure Quantum Computing Platforms” is to create the basis for a trustworthy and secure use of quantum computers so users can take advantage of quantum computing without worrying about the security of their data and algorithms.
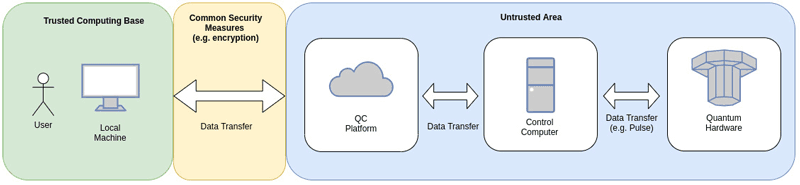
Figure 1: High-level Data Flow. This illustration shows an abstract view on data transmission from a local machine to the Quantum Computer and back. The areas are subdivided according to different levels of trust in the data flow. © Fraunhofer AISEC.
This project is part of the Bavarian Competence Center Quantum Security and Data Science (BayQS) [L1] and is only one of several addressing security in quantum computing. If you want to learn more about our work, feel free to get in touch with us.
Link:
[L1] Website BayQS (in German): https://www.aisec.fraunhofer.de/de/fields-of-expertise/projects/BayQS.html
References:
[1] J. F. Fitzsimons: “Private quantum computation: an introduction to blind quantum computing and related protocols”, npj Quantum Information, 3(1), 1-11, 2017. https://www.nature.com/articles/s41534-017-0025-3
[2] C. Fontaine, F. Galand: “A survey of homomorphic encryption for nonspecialists”, EURASIP Journal on Information Security, 2007, 1-10. https://link.springer.com/content/pdf/10.1155/2007/13801.pdf
[3] U. Mahadev: “Classical homomorphic encryption for quantum circuits”, IEEE 59th Annual Symposium on Foundations of Computer Science, 2018. http://ieee-focs.org/FOCS-2018-Papers/pdfs/59f332.pdf
Please contact:
Barbora Hrdá
Fraunhofer Institute for Applied and Integrated Security AISEC, Germany











