by Ramon Barakat, Sascha Hackel (Fraunhofer FOKUS) and Miltiadis Siavvas (CERTH)
The Design and Operation of Secure Supply Chain (DOSS) project’s Supply Trust Chain idea seeks to truly improve IoT security and trust from design to deployment. The project’s goal is to secure the IoT supply chain throughout its lifecycle, ensuring that stakeholders always have access to security-related information.
The DOSS project [L1], under the Horizon Europe initiative, is dedicated to securing the IoT supply chain throughout its entire lifecycle. This project aims to ensure IoT security by monitoring all stages from design to decommissioning, making security-relevant information accessible to stakeholders, and fostering robust communication among various actors.
The Device Security Passport, a machine-processable document that contains pertinent security data for IoT components, such as certificates, SBOM, HBOM, and MUD files, is one of the essential parts of the DOSS project. This document will be stored in a secure, accessible repository, ensuring that security data is both reliable and protected.
Figure 1 illustrates the preliminary architecture of the DOSS project, highlighting the integration of various modules and workflows. This architecture outlines how different components, such as the Component Tester and the Digital Security Twin, interact to ensure comprehensive security validation. By detailing these interactions, Figure 1 provides an overview of the system’s design and operational flow, emphasising the project’s holistic approach to IoT security.
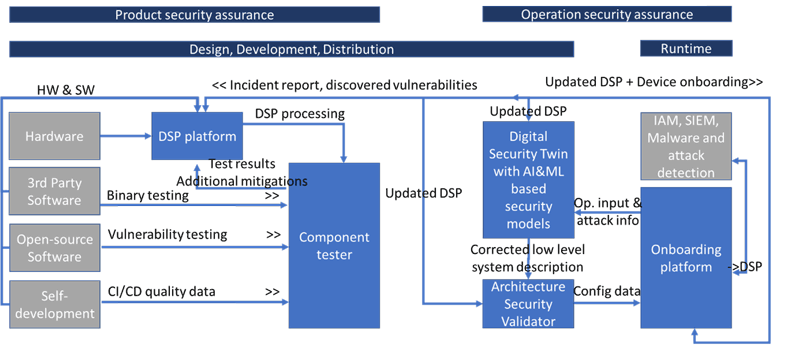
Figure 1: Overview of the supply chain integration (Supply Trust Chain).
Component Tester and Vulnerability Prediction
Adopting the Zero Trust principle of “never trust, always verify,” DOSS will validate all IoT architecture components at multiple stages. A unified Component Tester will verify the Device Security Passport’s content and ensure the security of the IoT components.
The Component Tester will ensure the security of the IoT components including third-party applications (closed- and open-source software) and proprietary developments. It utilises a comprehensive testing and validation methodology, analysing closed-source software using binary code validation techniques and verifying components according to their Device Security Passports. Software security verification methods will be used to evaluate open-source software and proprietary development.
The DOSS project emphasises the importance of Interactive Application Security Testing (IAST) to address the complexities of IoT security. IAST combines the strengths of Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST) to provide a more comprehensive security analysis.
In addition to the static analysis, a Vulnerability Prediction module using Large Language Models (LLMs) will be integrated. The vulnerability prediction focuses on identifying security hotspots in software components, enabling better allocation of testing resources [2]. DOSS will explore the use of popular pre-trained LLMs for vulnerability prediction, including Generative Pre-trained Transformer (GPT), Bidirectional Encoder Representations from Transformers (BERT), and Bidirectional Auto-Regressive Transformers (BART), which will be fine-tuned using curated vulnerability datasets and compared against traditional text-mining-based models. For enhancing their accuracy, additional modalities will be used as inputs to capture more context from the source code, focusing on text-rich graphs, such as Abstract Syntax Trees (ASTs), Control-flow Diagrams (CFDs), etc. Explainable AI (XAI) techniques will be also leveraged to facilitate vulnerability localisation [3].
An essential aspect of the DOSS CT is the patch validation process. Directed fuzzing techniques are used to ensure that security patches effectively fix vulnerabilities completely without introducing new ones. This technique generates a suite of tests that trigger the identified vulnerabilities in various ways during patch development, ensuring comprehensive coverage and validation.This integrated approach enhances the detection of vulnerabilities and streamlines the remediation process, ensuring that only secure components are integrated into the IoT architecture.
IoT Operation and Supply Trust Chain
DOSS extends its security concept to IoT operation. New devices will be integrated using an automated Onboarding Platform, leveraging the Device Security Passport for configuration.Furthermore, the CT of the DOSS project is designed to be versatile, allowing for use not only during the development phase but also on the operator side. This ensures ongoing security validation.
Infrastructure automation technologies will be used to model various service architectures by importing verified components into a Digital Cybersecurity Twin. High-level system descriptions will be extracted by AI-assisted models to detect threats and suggest defences. The Architecture Security Validator will perform automated architecture validation on these models ensuring also their compliance with industry standards. The tested, modelled, and validated IoT architectures will also be monitored during their operation by the IoTAC platform presented in [1]. The IoTAC platform [L2] will monitor and protect the operational environment, providing feedback to design-time modules and stakeholders through the Supply Trust Chain.
Conclusion
The DOSS project aims to significantly enhance the security and trust of IoT services and architectures. Through its comprehensive approach, DOSS strives to contribute to a more secure and trustworthy IoT ecosystem. The project’s findings will be validated in automotive, prosumer cell operation, and smart home domains, ensuring practical relevance and impact.
The DOSS project has received funding from the European Union’s Horizon Europe research and innovation programme under grant agreement No 101120270.
Links:
[L1] https://dossproject.eu
[L2] https://iotac.eu/
References:
[1] S. Hackel, M. Schneider, and R. Barakat, “Security-by-design IoT development and certification with IoTAC,” ERCIM News 134, Jun. 2023. https://ercim-news.ercim.eu/en134/r-i/security-by-design-iot-development-and-certification-with-iotac
[2] I. Kalouptsoglou, et al., “Software vulnerability prediction: A systematic mapping study,” Information and Software Technology, vol. 107303, 2023.
[3] M. Fu and C. Tantithamthavorn, “Linevul: A transformer-based line-level vulnerability prediction,” in Proc. of the 19th Int. Conf. on Mining Software Repositories, 2022, pp. 608–620.
Please contact:
Ramon Barakat, Fraunhofer FOKUS, Germany
Sascha Hackel, Fraunhofer FOKUS, Germany











