by Mehdi Akbari Gurabi, Lasse Nitz, Charukeshi Mayuresh Joglekar, and Avikarsha Mandal (Fraunhofer FIT)
As cyberattacks evolve and become more complex, defenders require advanced tools for effective incident response. In the H2020 projects, SAPPAN and CyberSEAS, we conducted research to develop a cybersecurity playbook management system that provides a robust framework for creating, maintaining, and sharing standardised incident response procedures. The pilot validation shows how the system can be streamlined into current cybersecurity operations, towards compliance with the latest security recommendations and directives.
In today’s continuously evolving digital landscape, enhancing cybersecurity practices is more critical than ever. This dynamic environment necessitates a robust and adaptive approach aligned with the cybersecurity recommendations and guidelines such as the National Institute of Standards and Technology (NIST) incident response life cycle. The relevance of standardised incident response procedures is amplified by the introduction of Collaborative Automated Course of Action Operations (CACAO), a new standard on how playbooks can be designed and shared. Additionally, the recent implementation of the Network and Information Security Directive (NIS2) aims to enhance cybersecurity measures across the European Union, broadening its scope to include more sectors and imposing stricter obligations. The NIS2 directive highlights the need for comprehensive and standardised incident response procedures to enhance the collaboration between stakeholders. The general nature of the directive requires specific tools that can effectively implement its guidelines.
Our playbook management tool SASP [1] aims to support the transition to NIS2 [2] by offering a structured and practical approach for collaborative incident response [3] and enabling standardised reporting. It provides a cooperative environment to enhance cybersecurity resilience through the cross-European exchange of expertise and experiences.
SASP research and development began with SAPPAN [L1], where we developed advanced cybersecurity solutions focused on privacy-preserving sharing of cybersecurity threats intelligence. SAPPAN focused on facilitating sharing and automation, utilising advanced data analysis and machine learning to enable efficient response and recovery. It supports both single and cross-organisational collaboration through privacy-preserving data processing and sharing, enriching situational awareness, facilitating intrusion detection, and enabling knowledge sharing while maintaining data confidentiality. Building on this groundwork, we continued the development of SASP in the CyberSEAS [L2], refining and expanding our tool’s capabilities, integrating it with other incident handling solutions, and validating it in a pilot within the energy sector. The CyberSEAS project aims to improve the resilience of Electrical Power and Energy Systems (EPES) by protecting them from disruptions caused by complex attack scenarios.
The SASP playbook management tool is designed for creating, maintaining, sharing, visualising, and exporting cybersecurity playbooks [1]. It features a user interface for creating playbooks, viewing them in Business Process Model and Notation (BPMN), exporting in JSON format, and sharing playbooks. By supporting the OASIS CACAO playbook format, we ensure playbooks are machine-readable and standardised. Figure 1 shows the interface of the tool for managing and execution of playbooks. Our tool offers a comprehensive suite of functionalities designed to manage machine-readable playbooks efficiently as listed here:
- Management: Adding, modification, deletion, import/export of playbooks.
- Sharing: Playbooks can be shared via the Malware Information Sharing Platform (MISP) using the already defined MISP object for playbook sharing in different formats. They further can be shared via Kafka between different instances of the SASP tool.
- Automated BPMN graph generation: Visualisation in BPMN format with interactive editing options for steps.
- Sanitisation: Ensures the removal of sensitive information from playbooks based on manually included tags using the Traffic Light Protocol (TLP).
- Versioning system: Facilitates continuous improvement of playbooks and getting access to the previous versions.
- Rich variety of supported workflow elements: Elements such as loops, and exclusive branching are supported by the vocabulary, which enhances the flexibility and functionality of playbooks.
- Integration: Integration with TheHive and Cortex for automated execution of incident response actions.
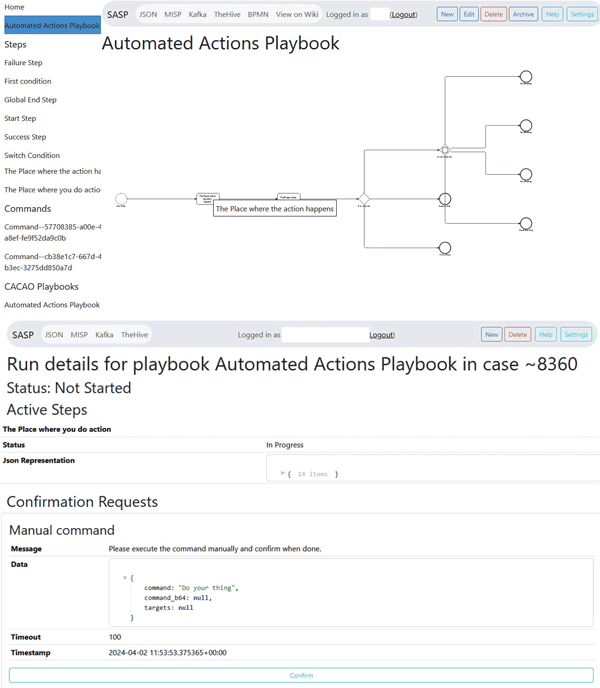
Figure 1: Exemplary tool features in the UI include (top) a visual representation of the playbook in BPMN with an interactive modification option by clicking on the steps, and (bottom) an overview of the running step of a playbook with a command prompt for automatic execution or manual confirmation of action success.
SASP has been tested and validated in real-world environments. This includes a system prototype demonstration by a Security Operations Centre (SOC) responsible for securing IT/OT systems, and a European national Computer Emergency Response Team (CERT). During the piloting phase, various methods for playbook management and sharing were utilised to establish standardised procedures for handling well-known attack scenarios, emphasising governance aligned with NIS2 requirements [2]. The tool integrates with MISP for incident reporting. This integration enables automated sharing of incident indicators, regulatory information, and playbook data. The playbook data suggests appropriate responses to incidents and adheres to the recommended national standard format for incident reporting.
As a demonstration scenario, the SOC shared a specific playbook via MISP (e.g. phishing, malware, or ransomware). This playbook was reviewed, generalised, and sanitised by the European national CERT before being disseminated to relevant stakeholders. Additionally, the SOC shared Indicators of Compromise (IoCs) via MISP, referencing the related playbook to enhance understanding and resolution of the incident. The created MISP event was subsequently shared with relevant recipients through the national CERT’s MISP instance.
Input for this validation has been collected through a structured self-assessment questionnaire, a semi-structured pilot partners interview session, and observations and comments from validation partners. The high quality of the feedback and interview answers emphasised the tool’s success in improving incident response knowledge management, enhancing collaborative incident response and facilitating information sharing among cybersecurity entities. This validation process confirms the tool’s readiness for Technology Readiness Level 7 (System prototype demonstration in an operational environment) and its potential to enhance cybersecurity practices significantly.
We are considering open-sourcing [L3] our tool to enhance community engagement and collaborative improvement. For future research directions, we focus on automation processes for incident response and enhance the tool’s capabilities by integrating the tool with de facto tools and services used in incident handling. Additionally, manually creating structured playbooks from legacy unstructured or semi-structured ones can be exhaustively time- and resource-intensive for security operators. Therefore, we aim to develop AI-assisted automation for translating legacy playbooks into standardised, machine-readable formats.
This project has received funding from the European Union’s Horizon 2020 research and innovation programme under grant agreements No 833418 (SAPPAN) and No 101020560 (CyberSEAS).
Links:
[L1] SAPPAN website: https://sappan-project.eu
[L2] CyberSEAS website: https://cyberseas.eu
[L3] SASP GitHub repository: https://github.com/Fraunhofer-FIT-DSAI/SASP
References:
[1] M. Akbari Gurabi et al., “SASP: a semantic web-based approach for management of sharable cybersecurity playbooks,” in ARES, 2022.
[2] M. Akbari Gurabi et al., “Requirements for playbook-assisted cyber incident response, reporting and automation,” Digital Threats: Research and Practice, 2024.
[3] L. Nitz et al., “From Collaboration to Automation: A Proof of Concept for Improved Incident Response,” ERCIM news 129, 2022.
Please contact:
Mehdi Akbari Gurabi, Fraunhofer Institute for Applied Information Technology (FIT), Germany











