by Florian Skopik, Arndt Bonitz, Daniel Slamanig (Austrian Institute of Technology), Markus Kirschner (MUSE Electronics GmbH) and Wolfgang Hacker (Austrian Ministry of Defence)
Military field operations place high demands on information and communication technology (ICT) devices, both in terms of reliability and security. These requirements include robustness against environmental influences such as vibrations, water and humidity, as well as protection against physical attacks and cyberattacks [1]. Attempts to compromise a device must be detected immediately and, if necessary, trigger automated countermeasures such as alarms, partial deactivation or emergency wiping of all data.
Currently, there are robust end-devices from well-known non-European manufacturers in tablet form factor available on the international market. However, none of these devices support reliable monitoring of device integrity, nor do they combine all relevant international protection classes required for military use. In the interest of reusability, further measures must be taken to ensure that devices that were already used in one mission can be reliably and securely deployed in other security environments as new devices.
In contrast to other manufacturers, MUSE Electronics GmbH and its partners do not repurpose existing products, but develop an independent cyber-physical architecture for a robust computer tablet. A prototype has been created based on industrial design and reinforced plastics, which is also resistant to electromagnetic attacks. In addition, further hardware and software measures are implemented to harden the device, such as hardware security gateways that control the data flows between the components, and the use of cryptography to guarantee strong authentication between components and the integrity and authenticity of software running on the platform.
The SD4MSD project aims to combine an integral overall concept at physical, hardware and software level for highly robust end-user devices with individual configurability for specific (military) purposes. A comprehensive concept for hardening a mobile ICT device is developed in order to resist a sufficient range of physical, electromagnetic and cybersecurity-oriented attack vectors. Ensuring authenticity, integrity and confidentiality throughout the life cycle of the ICT device is crucial. A modular system architecture offers multiple purposes of use with simultaneous platform flexibility. Maintenance and service processes as well as best practices and standards are appropriately considered.
One Device for Multiple Security Domains
If the same devices are to be deployed at often short intervals one after the other in different mission-specific security domains, for example in command posts and mobile data centres, the security requirements increase significantly. Ensuring that highly sensitive and mission-critical data is only accessible in the currently relevant security domain is essential. International security and abuse incidents due to inadequate solutions based only on virtualisation and pure container solutions [2] underline the importance of a robust and reliable “single-device solution” that can be used in multiple application domains without security concerns. For security reasons, it is currently often necessary to purchase multiple physical devices to be able to change the device for each use, depending on the security domain for which it was ultimately certified. This is not only economically inefficient (such special devices, including expensive accessories, often incur high additional costs), but also poses a logistic challenge and causes additional work in the administration of devices. Hence, SD4MSD delivers a concept for a device that can be used in multiple security domains, isolating mission-specific data from each other without the risk of data spillover.
In the centre of Figure 1, the basic architectural elements of such a secure device are depicted. All mission data and the operating system (OS) is contained on an encrypted boot medium. A security gateway (SG) is built into the device, which takes over various security-critical tasks and plays a central role in the concept. It is responsible for the control (activation and deactivation) of external and internal interfaces based on configuration files, communication with external media (read/write), and the implementation of a secure boot process. Furthermore, it monitors the physical integrity via sensors built into the device, logs derived events and may perform actions such as blocking or wiping in the event of an integrity violation. The SG also has access to Trusted Platform Modules. A TPM is a secure element that can generate and store cryptographic key information and perform cryptographic operations. Moreover, a TPM is central for guaranteeing platform integrity, that is, it can be used to store and verify the status configuration of software.
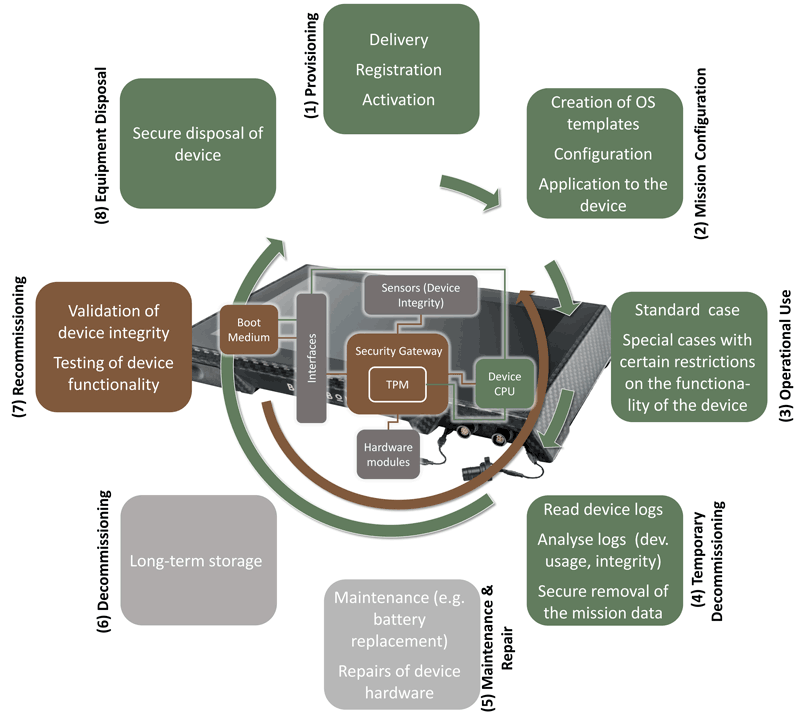
Figure 1: The SD4MSD life cycle model.
A Life Cycle Model for Reusable Handheld Devices
The project accounts for all phases in the life cycle of the secure tablet, as depicted in the outer elements in Figure 1, inspired by common IoT life cycle models [3]. This cycle starts with the provisioning of a device, including the initial delivery, the registration and activation of devices, and continues with mission configuration (i.e. the creation of mission-specific OS templates and deployment of applications), the actual operational use in the field and the following temporary de-commissioning once a mission has been completed. This last step takes care of reading out device logs, analysing them to detect any hardware or software issues, including compromise, and addresses the secure and permanent removal of mission-specific data. A device could then go either into maintenance and repair in case the log analysis revealed any pending issues or into long-term storage. The re-commissioning phase puts a device into operation again, that is, validates its integrity and tests the device functionality, before mission-specific configurations are applied again. At the end of each device’s life, the secure equipment disposal ensures that all data remnants are destroyed before a device is destroyed and recycled.
The Project SD4MSD and its Consortium
In order to attain these ambitious goals and finally ensure the wide applicability of the developed solutions and procedures, the project consortium consists of a vital mix of a strong academic partner with deep knowledge in secure system design (Austrian Institute of Technology), a vendor of physical tablets with rich experience in implementing these solutions (MUSE Electronics GmbH) and the Austrian Ministry of Defence as end-user partner. SD4MSD is a 30-month national research project running from 2021 to 2023 and is funded by the Austrian defence research programme FORTE of the Federal Ministry of Finance (BMF)
References:
[1] MIL-STD-810H: Environmental Engineering Considerations and Laboratory Tests. U.S. Department of Defense, 2019.
[2] S. Sultan, I. Ahmad, T. Dimitriou, “Container security: issues, challenges, and the road ahead,” IEEE access, vol. 7, 52976-52996, 2019.
[3] L. F. Rahman, T. Ozcelebi and J. Lukkien, “Understanding IoT systems: a life cycle approach,” Procedia Computer Science, vol. 130, 1057-1062, 2018
Please contact:
Florian Skopik, AIT Austrian Institute of Technology, Austria











