by Christophe Ponsard, Philippe Massonet, Valery Ramon (CETIC)
Coping with cybercrime in the scope of increasingly open and interconnected systems is a difficult challenge. DevSecOps provide an adequate framework to keep in control of this perpetual race. We show here how it can be efficiently supported by an internal model-based analysis and automation approach together with the external threat intelligence sharing.
An effective way to counter cyberattacks targeting a company’s assets is to organise several lines of defence based on a strong risk culture. Typical lines are to protect, detect/respond, and be able to recover, as documented in the NIST Cyber Security Framework [L1]. However, in order to be efficient, organisations need to be as reactive as the cybercriminals, who have structured themselves along a whole value chain including selling vulnerability exploits, providing attacks as a service, and making profit based on stolen or ransomed data.
The DevSecOps approach aims at creating and including modern security practices in the fast and agile world of DevOps [1]. It promotes collaboration between developers and operators by involving security experts, while relying on strong automation (e.g. bots) and continuous integration/delivery tools. To make it even more efficient, our recent research explored the use of modelling techniques in order to build consistent and integrated model chains [2] as depicted in Figure 1.
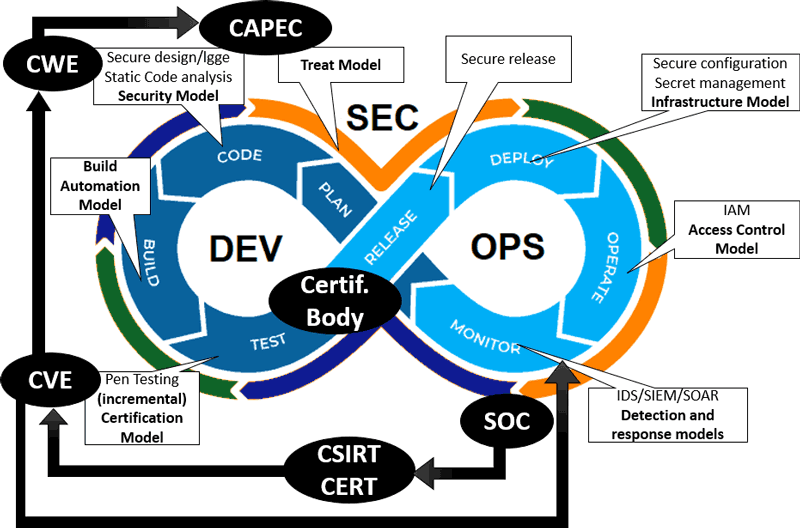
Figure 1: DevSecOps model-oriented activities in internal and external chains.
Key modelling activities start from threat modelling at the planning phase and are managed first throughout the development phase, including making sure the code is immune to common attack patterns (CAPEC) and common weaknesses (CWE), before going into the build and test phase using building automation and targeted pen testing. At this level, in the scope of the SPARTA project [L2], we are also developing models and tools to support incremental certification processes, which provide third-party assurance on the security of the deployed solution [3]. Then, in the operations phase, an infrastructure model, similar to the planning phase, is used as well as access control models for secure operations. Active monitoring is also used to detect known or unknown attack types, possibly through shared Common Vulnerability and Exposures (CVE), and to trigger automated responses to them.
The knowledge acquired through the monitoring, especially unknown attacks, can be reported by the local Secure Operation Centre (SOC) to a network of Computer Emergency Response Team, which can result in new CVE, which can lead to documenting new CWE and CAPEC. This learning part occurs outside the organisation and proceeds backwards through the development phases, enabling the coping with new security issues as early as possible.
The next steps of our research are based on grand challenges proposed by CyberWal platform, driven by industrial needs [L3]. They target problems such as the precise risk modelling of Cyber Physical Systems, automation of attack scenarios for driving penetration testing, and AI-based intrusion detection for industrial systems.
Links:
[L1] https://www.nist.gov/cyberframework
[L2] https://www.sparta.eu
[L3] https://cyberwal.be
References:
[1] H. Myrbakken, R. Colomo-Palacios: “DevSecOps: a multivocal literature review", SPICE, 2017.
[2] J. Hugues, J. Yankel: “From Model-Based Systems and Software Engineering to ModDevOps”, CMU, 2021.
[3] D. Sébastien, et al.: “Incremental Common Criteria Certification Processes using DevSecOps Practices”, EuroS&P Workshops 2021.
Please contact:
Christophe Ponsard
CETIC, Belgium
+32 472 56 90 99











