by Christos Alexakos (ISI/ATHENA RC), Kristina Livitckaia (ITI/CERTH), Mike Anastasiadis (ITI/CERTH), Dimitrios Serpanos (University of Patras)
The importance of cybersecurity for Internet of Vehicles (IoV) systems is indisputable as possible attacks can cause the loss of lives. In nIoVe project, a cybersecurity framework has been developed. This framework includes tools for accurate detection of the propagation trends and root cause analysis of the attacks, providing additional knowledge for cyberattacks against lookalike infrastructures.
Autonomous vehicles mainly operate inside a smart city infrastructure. Due to the plethora of Internet-connected entities inside and outside the vehicle, the cybersecurity issues emerging are of utmost importance. In cybersecurity, the knowledge of previous attacks strengthens the systems that are responsible for the detection and identification of a cyberattack as well as the systems orchestrating the mitigation actions. This article presents an approach that utilises attack data collected by honeypots installed inside the vehicle to define the root cause and the propagation trends of detected attacks. The scope is to define, through a harmless infrastructure, a honeyfarm, the possible root cause of a cyberattack on an autonomous vehicle and share this information with other detection tools for faster and more reliable intrusion detection. The presented tools are part of the security infrastructure of nIoVe: A Novel Adaptive Cybersecurity Framework for the Internet-of-Vehicles European project [L1] by researchers of Industrial Systems Institute of ATHENA RC and Information Technologies Institute of CERTH, Greece.
The approach that was followed is depicted in Figure 1. The approach follows the steps that define the Root Cause Analysis (RCA). According to Wangen et al. [1], RCA is considered a structured investigation that follows a well-defined procedure to identify the cause of the detected problem and define the actions to eliminate or prevent it in the future. Andersen and Fagerhaug [2] presented a simplified vision of the root cause problem where the identification of the root cause is a sequential process looking at the bottom reason that initiated the cause-and-effect chain that finally causes the problem.
The first phase is the installation of the honeypots’ infrastructure. A tool has been developed to allow administrators to create a honeyfarm dynamically. The honeyfarm will be a combination of different honeypots emulating the sensors inside the vehicle and generally the autonomous vehicle entity (Lidar, camera, CAB bus, IMU, OBU, etc.). The utility of the honeyfarm is to attract the attackers into attacking it while allowing the monitoring of the attack mechanisms used against it.
The most common way to detect propagation trends is to apply Markov Chain Models. A Markov Chain is a stochastic process that assumes the next step of the process depends only on its current state. In the context of detecting propagation trends, Markov Chains are applied to model attack sessions, with each node representing a honeypot being attacked and the transitions showing that another honeypot is attacked immediately after the last. The following process is adopted to build a Markov Chain Model based on the data collected by a honeypot framework: a) Single events detected in the framework are used to construct attack sessions. b) The attack sessions are used to construct the Markov Chain Model. Also, contextual models can be built by filtering the list of single events to only include events happening within a certain context. Once the Markov Chain Model graph has been constructed, graph analysis techniques based on clustering algorithms and centrality metrics are applied to gather insight into the system's propagation trends.
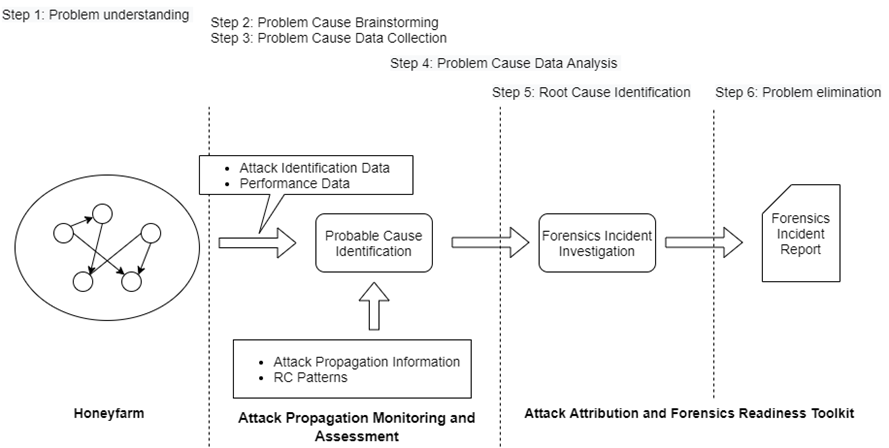
Figure 1: The Attack Propagation Monitoring and Root Cause Analysis Procedure of the nIoVe framework.
The procedure of RCA is semi-automated and based on six steps as depicted in Figure 1. The pipeline starts when an anomaly behaviour is detected on the honeyfarm. Based on the previous knowledge of the attack propagation and with the data about the performance of the systems in the network, the process will identify the probable honeypots and vulnerabilities that are the root cause of the attack. This approach uses a semantic graph that depicts the networked system of the honeyfarm. Each node in the graph is a system/device, each edge provides information about the relations between two nodes, each object’s properties define the functionalities of the nodes. For the first step in the RCA, the procedure is Problem Understanding. For this, a Performance vs. Importance matrix will be created. The matrix will be a 2-dimensional diagram. The x-axis will represent the values of each node’s functionality performance, and the y-axis the importance of the node’s functionalities. For the RCA, the number of the points in the quarter Bad Performance and High Importance defines the problem and identifies the probable nodes that cause it. The next phase of RCA is a data collection analysis process, including the collection of the attack data and its process in two steps. First, the use of the attack propagation knowledge to back trace the propagation pattern to the probable root cause. Second, the use of graph similarity methods to find information from previous attacks to similar systems. These algorithms aim to detect the node and the functionality (e.g., network, software services, etc.) that cause the problem to the overall system. Finally, the data collected and the identified causes will be forwarded to the Forensics Assessment tool where a security expert will investigate all the information and generate a report including the RCA and suggestions for mitigation actions, which are finally saved in a shared threat intelligent repository based on MISP platform [L2].
The presented approach can be used to model valuable information of possible attacks on a complex and sensitive system such an autonomous vehicle. The research on the collection of data from various attacks and the optimisation of the attack propagation trends and root cause is a continuous challenge for the authors, who anticipate automating the semi-automatic process of RCA.
Links:
[L1] https://www.niove.eu
[L2] https://www.misp-project.org/
References:
[1] G. Wangen, et al: “An empirical study of root-cause analysis in information security management”, SECURWARE, IARIA pp. 1-14, 2017.
[2] B. Andersen and T. Fagerhaug: “Root cause analysis: simplified tools and techniques”, Quality Press, 2006.
Please contact:
Christos Alexakos
Industrial Systems Institute/ATHENA RC, Greece











