by George Tsakalidis, (Financial and Economic Crime Unit - S.D.O.E. (Operational Directorate of Macedonia)) and Kostas Vergidis, (University of Macedonia)
A systematised investigation process for copyright-related cybercrime offences has been designed in the Business Process Model and Notation (BPMN) and implemented by financial crime investigators of a Law Enforcement Agency. The proposed approach has increased the efficiency of the performed investigations and the dissemination of knowledge to relevant agencies.
The advances in information systems and network technologies have created a novel conducive environment for criminal activity, broadly known as cybercrime. An emerging cybercrime type with high frequency of occurrence and severe consequences for the global economy, refers to offences related to infringements of copyright and related rights [1]. In the financial context, this critical cybercrime covers the illegitimate download, copy, distribution, and usage of intellectual property, also in the form of software, programs, and tools. In Greece, this cybercrime is extensively committed by individuals, companies, and organisations, recording an average of 61% of unlicensed software installations during the period 2011–2017 [2]. The presented project is an initiative for the standardisation of the investigation procedure of this widespread cybercrime and the subsequent improvement of the efficiency of a Law Enforcement Agency. The investigation process refers to the National Law N2121/1993 and the Intellectual Property (IP) infringements committed through the usage of illegitimate (pirate) software products by companies and organisations in Greece.
The institutions involved in the research project are: (a) the Financial and Economic Crime Unit - S.D.O.E. (Operational Directorate of Macedonia) of the Greek Ministry of Finance and (b) the Department of Applied Informatics of the University of Macedonia, Thessaloniki, Greece. The investigators of the Agency were involved in recording and specifying the investigation activities and the different scenarios that can emerge, interrelating the applying laws and checking process conformance. Researchers from the University of Macedonia were assigned with modelling the investigation process using a state-of-the-art standard, the Business Process Model and Notation (BPMNv2.0) [3].
The established BPMN notation was adopted to be readily understandable by all users, from the analysts that create the initial process drafts, to the developers that implement the technology, and finally, to the investigators that manage and execute these processes. The steps followed during the standardisation of the investigation procedure involved the cooperation of the two institutions, to translate fragmentary investigation steps into an executable BPMN diagram. The process (Figure 1) initiates with the arrival of the investigators to the company and the display of their IDs and investigation mandate. During the personal computer (PC) software investigation subprocess, the investigators search the company and set all PCs in operation. For unveiling the installed software, both portable auditing software and manual search methods are used. The installed software programs are documented, and the list is provided to the company for collecting both the evidence of legitimate acquisition and usage.
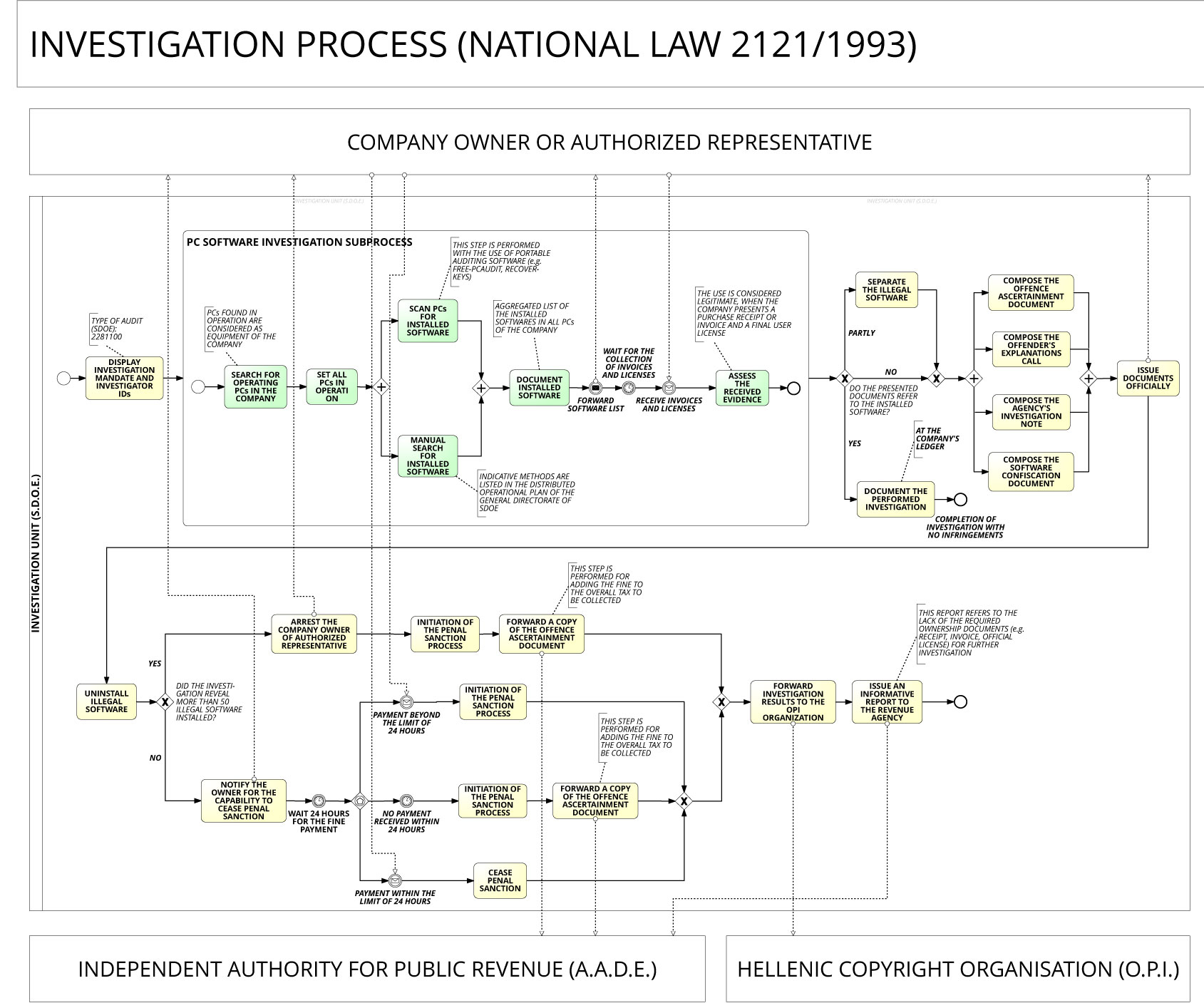
Figure 1: Investigation Process for IP infringements related to illegal software usage (National Law N.2121/1993).
Depending on whether the presented evidence refers to the installed software, the unit will either complete the investigation, or proceed with the enforcement of sanctions determined in N.2121/1993 (followed by composition of official documents and software uninstall). If the illegal software programs number more than 50, the investigators proceed to arrest the company owner or representative, initiate the penal sanction procedure and forward a copy of the offence ascertainment document to the local revenue office (AADE) for collecting the imposed fine. In the case of fewer than 50 programs, the unit notifies the owner or representative of the capability to cease penal sanction in case the fine is paid within the next 24 hours. For fewer than 50 software programs, the penal sanction is ceased in the case of punctual payment and initiated in the case of non or overdue payment. The final steps involve forwarding the investigation results to the Hellenic Copyright Organisation (OPI) for notifying the software manufacturers and to the AADE office for further investigation.
The use of the investigation process provides a multitude of benefits for both the agency and investigators. In particular, this is a typical example of digital transformation in the public sector since it fulfils: (a) the need for compliance with the Digital Transformation Strategy 2020-2025 of Greece, (b) the obligation of public agencies to index their administrative processes to the National Process Registry (Law N.4727/2020), and most importantly (c) the need to standardise the investigation processes of the agency and to enhance the efficiency and situational awareness of all the investigators that are tasked with this authority.
Regarding the latter, the investigators are accustomed to the different scenarios that can emerge, they know beforehand which official documents to complete, and they are aware of the applying laws and rules. By using the process, investigators examine more cases in the same time periods, a fact that has reduced the operating expenses of the agency, both monetary and in human resources. The orientation of the project is the application of the systematised investigation process by the rest of the investigators of the Directorate. The process has been distributed to the rest of the investigators to get accustomed to the methodology and apply the process in everyday cases. A principal advantage of the process is that it can be readily applied by investigators of the Operational Directorate S.D.O.E. of Attica and other Law Enforcement Agencies that have the same jurisdiction.
There is ongoing work for further extending the project, primarily in quantifying the efficiency of the investigation process. The authors are creating an inventory with statistical metadata regarding execution times and number of investigators involved, in an attempt to identify defective process parts and bottlenecks through simulation. In this manner, the authors intend to redesign the process and optimise critical performance criteria, like execution time and/or cost, process flexibility and overall external quality.
References:
[1] G. Tsakalidis and K. Vergidis: “A systematic approach toward description and classification of cybercrime incidents”, IEEE Trans. Syst. Man Cybern. Syst., vol. 49, no. 4, pp. 710–729, 2017.
[2] BSA, The Software Alliance: “BSA Global Software Survey,” Washington, DC, Annual, Jun. 2018. Accessed: Feb. 13, 2022. [Online]: https://kwz.me/hfF
[3] Object Management Group (OMG): “About the Business Process Model And Notation Specification Version 2.0,” Dec. 2013. Accessed: Jan. 23, 2022. [Online]. Available: https://www.omg.org/spec/BPMN/2.0/About-BPMN/
Please contact:
George Tsakalidis
Financial Crime Investigator
Financial and Economic Crime Unit - S.D.O.E. (Operational Directorate of Macedonia), Greece











