by Robert Luh and Sebastian Eresheim (University of Vienna & St. Pölten University of Applied Sciences)
PenQuest is a digital multi-player game that allows users to recreate or emulate cyberattacks on a game board representing freely configurable IT infrastructures. The game’s model incorporates a multitude of security concepts and threat vocabularies translated into technical and organisational actions. PenQuest is intended to assist risk assessment, support the reconstruction of adversarial events, and gamify security education.
PenQuest [1,2] is an adversarial cyber-security game conceived and developed by St. Pölten University of Applied Sciences and the University of Vienna, with additional funding from DIH-OST. It combines a board game modelling freely configurable, hierarchical IT infrastructures with game actions representing technical, organisational, and social engineering attacks as well as appropriate defensive measures. PenQuest was originally built to support security education and awareness trainings but has long since branched out to encompass risk assessment and forensic event reconstruction.
Under the hood, the attacker’s potential actions are derived from the MITRE ATT&CK framework [L1], while defensive actions are based on MITRE D3FEND [L2] as well as the NIST SP 800-53 security standard [L3]. The effects of data theft (confidentiality attacks), system manipulation (integrity attacks), and attacks on availability are modelled in addition to the different kill chain phases of an attack, which typically range from reconnaissance, to propagation, and “detonation” activity. Simply put, actions deal a certain amount of “damage” and are limited to one or several attack stages in accordance with their technical specifics. For example, the action “Inter-Process Communication” that abuses data exchange mechanisms between processes to execute code can only be used once the attacker has gained access to the system in an earlier turn.
Attacking and defending actors of various levels can be defined using numeric attributes denoting skill, motivation, and financial means. These attributes in turn limit available actions and equipment (security appliances, attack tools, etc.) that can be utilised or procured. Furthermore, the game considers the inter-dependencies of systems, privilege levels, and models vulnerabilities that can be exploited through e.g., malicious software procurable in-game.
Another key part of the framework revolves around the mapping of mitigating controls to specific attacks in order to maximise realism and help design more effective prevention, detection, and response measures. To this end, various approaches ranging from abstracting attacks to their base components (e.g., account elevation, scanning, configuration changes, or social engineering) to natural language processing (NLP) were explored and evaluated with the help of security experts.
Put together, a multitude of real-world threat scenarios can be depicted within the context of PenQuest and combined to reconstruct the events leading up to a system compromise, to create awareness-raising measures, or even to conduct comprehensive risk analyses. Thanks to the unrestricted configuration of actors, actions, and systems, there are hardly any limitations – from modelling a ransomware attack on an isolated workstation performed by an opportunist individual, to recreating a large-scale data theft by a well-funded corporate competitor, anything is possible.
While the PenQuest server and client are already available for use to early adopters and testers (see figure), ongoing research conducted as part of the “INODES” project [L4] at University of Vienna focuses on optimising strategies through reinforcement learning and model checking. We specifically aim to determine which attacks are most likely to succeed given different financial, temporal, or skill constraints and how defensive measures can best protect against them. A tie-in of the model to existing intrusion detection systems (IDS) is in the works as well. This way, it will become possible to link current alerts or indicators of compromise identified during a forensic investigation to likely attacker motivations and objectives, enabling not only the interpretation of past cyber-threats, but also the timely response to ongoing attacks.
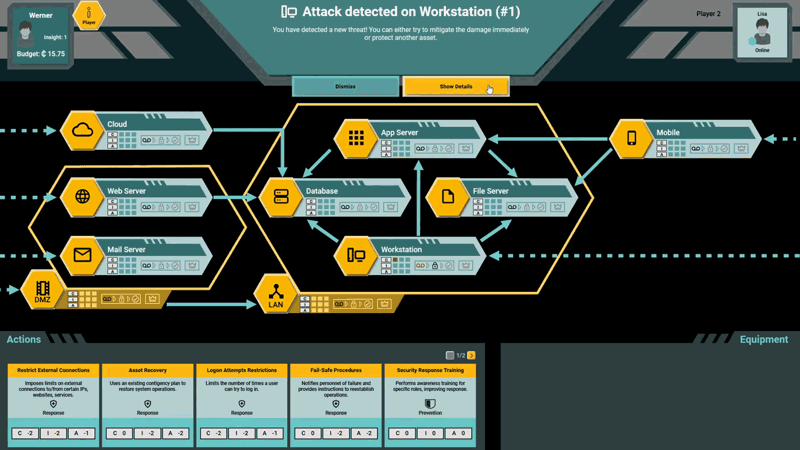
Figure 1: PenQuest game board depicting a common network infrastructure.
Visit [L5] for more information about PenQuest and contact the article authors for early access to the game.
Links:
[L1] https://attack.mitre.org
[L2] https://d3fend.mitre.org
[L3] https://csrc.nist.gov/publications/detail/sp/800-53/rev-5/final
[L4] https://informatik.univie.ac.at/en/research/projects/project/328/
[L5] https://www.pen.quest
References:
[1] R. Luh et al.: “PenQuest Reloaded: A Digital Cyber Defense Game for Technical Education”, in Proc. of EDUCON Conference, 2022.
[2] R. Luh et al.: “PenQuest: a gamified attacker/defender meta model for cyber security assessment and education”, Journal of Computer Virology and Hacking Techniques, 2019.
Please contact:
Robert Luh
University of Vienna and St. Pölten University of Applied Sciences, Austria
Sebastian Eresheim
University of Vienna and St. Pölten University of Applied Sciences, Austria











