by Robert Luh (University of Vienna and St. Pölten University of Applied Sciences) and Michael Galhuber (St. Pölten University of Applied Sciences)
Timestamps are among the most expressive artefacts in a digital forensic investigation. Our research shows that the distinct patterns caused by the interaction with individual files can yield more insight than previously documented and enables application fingerprinting within a Windows environment through timestamps alone. Furthermore, we classify timestamp forgery tools and present a means to detect their use.
Forensics practitioners heavily rely on timestamps in their investigation of criminal cases to create a meaningful timeline of events. Modern filesystems, such as Microsoft’s NTFS, track the creation, modification, access, and metadata changes down to near nanosecond resolution [1]. In addition to an exposed and easily accessible set of timestamps, NTFS maintains a second set that is typically altered only by the Windows kernel. These two sets (see figure), which are stored as attributes in the Master File Table (MFT) for each file created on the system, do not necessarily hold the same information but generally complement each other in terms of relevance. The inherent rules specifying when certain changes to these 8 timestamps are committed to the disk, result in unique patterns that potentially offer in-depth insight into a user’s or program’s activity that goes beyond other forensic data sources.
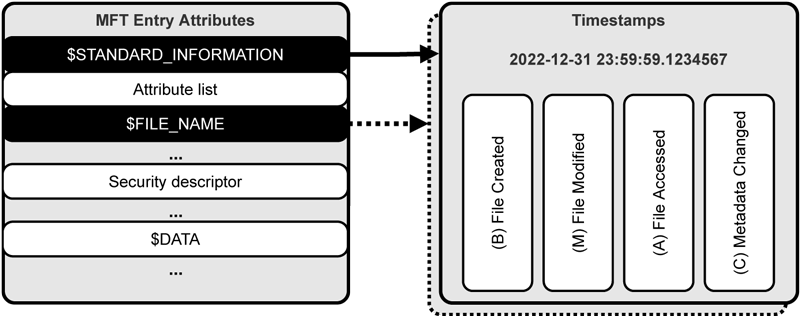
Figure 1: Excerpt from an MFT file record with the two highlighted attributes containing four timestamps each.
Experimental research [2] at St. Pölten University of Applied Sciences and the University of Vienna has shown that these patterns are even more expressive than previously documented [L1]. While it has been established that it is possible to identify generic file creation, access, modification, renaming, copying, moving, and deleting operations through NTFS timestamps, we have gone a step further and investigated the means by which these operations were conducted. We identified patterns that allow investigators to determine which specific application was used when interacting with a file, or how a user triggered a certain operation. For example, we were able to identify which specific PDF printer was used to create a document; if a file was opened in a certain text editor or on the command line; whether a file was copied or moved using a PowerShell command, keyboard shortcut or context menu (right click); or which format was used for a newly saved picture file, without assuming the validity of the extension.
In the second part of the project, we used that self-same approach to spot timestamp forgery, which constitutes one of the most disruptive anti-forensic techniques [3]. In all cases but one, we could determine that timestamps had been altered and were often able to identify the specific tool.
The practical implications in regard to these findings are manifold. Forensic investigators can use our timestamp patterns and updated time rules to correlate their findings by, e.g., linking an individual file to an application present on a suspect machine, even if additional app usage artefacts are missing or have been deleted. User profiling through shell interaction becomes possible, as does identifying the use of (shell) scripts for automated file modification performed by malicious software. Some file types may even be recognised through their timestamps after their extension and file signature (magic number) have been removed or falsified.
With the identification and classification of forgery tools by their impact and level of access (ranging from common API functions to direct disk access), we hope to make investigations more resilient to anti-forensics techniques, and help analysts quickly determine which artefacts can be trusted and which should be examined further.
In future research, we will endeavour to train machine learning models to automatically identify a wider range of applications, and develop a framework for forensic scientists to build their own models tailored to specific use cases and application sets. The goal going forward will be to make the investigative process more efficient and focus on combating anti-forensic techniques, which are often overlooked due to tool and time constraints.
Link:
[L1] https://www.sans.org/posters/windows-forensic-analysis/
References:
[1] B. Carrier: “File System Forensic Analysis”, Addison-Wesley Professional, 2010.
[2] M. Galhuber and R. Luh: “Time for Truth: Forensic Analysis of NTFS Timestamps” in ARES WSDF, 2021.
[3] W. Minnaard, et al.: “Timestomping NTFS”, MSc research project, University of Amsterdam, 2014.
Please contact:
Robert Luh
University of Vienna and St. Pölten University of Applied Sciences, Austria
Michael Galhuber
St. Pölten University of Applied Sciences, Austria











