by Jochen Hense, Simon Tjoa, Peter Kieseberg (St. Pölten University of Applied Sciences, Austria)
Traditional security education often focuses on teaching theoretical concepts but lacks hands-on experience. However, many aspects of modern security, especially in the incident management domain, cannot be taught in the abstract; they must be experienced. Our Cyber Defence Centre (CDC) allows us to train students in a simulated environment where they gain skills in detecting attacks, closing vulnerabilities, and responding to security breaches in a realistic but safe setting.
Modern society and economies are highly dependent on secure, reliable and available infrastructures. Cybercrime has evolved into a serious threat, ranging from primitive “spam & scam” to sophisticated targeted attacks that focus on a specific target or an entire industry. This is particularly facilitated by the global and autonomous nature of the Internet, which makes geographic distance meaningless in the event of an attack. Critical infrastructures therefore require additional protection, as downtime in these systems affect the lives of many citizens. Moreover, not only direct attacks on such an infrastructure need to be carefully considered, but the distributed infrastructure can also be used as a platform for further attacks on other industries. Thus, the European Union has established the EU NIS- directive [1], aiming at increasing the resilience of infrastructure deemed critical and facilitating the exchange of vital security-related information. This European dimension also means that infrastructure protection is becoming an interconnected problem, involving multiple players in a field as well as cross-sector supply chains.
Cyber Defence Centres (CDCs) [2] play a central role in the protection of information systems, as they integrate information from inside the enterprise as well as from external sources in order to establish situational awareness of the current risk situation. CDCs offer services for the structured collection, processing and provision of security-critical information to decision-makers and analysts. Using the integration of external information, machine learning and other AI techniques for pattern detection, it is often possible to detect attacks early (see Figure 1). Thus, especially large enterprises and government organisations consider cyber defence centres as the cornerstones of their coordinated defence activities.
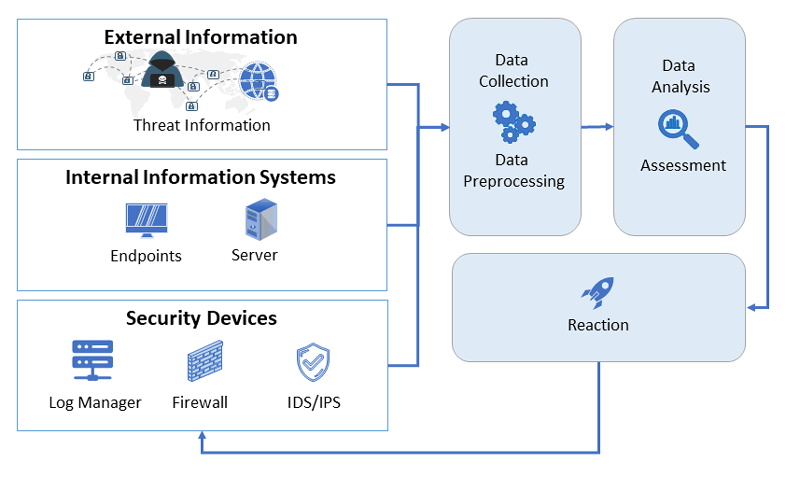
Figure 1: Integration of external information and AI into the CDC.
In particular, the so-called "war rooms" [3], the central points where decisions are made on the basis of visualised information aggregates, are familiar from many presentations by relevant providers. However, many important analysis steps take place separately by trained personnel: In this context, the use of AI for (semi-) automation of information analysis is becoming more and more important.
For this reason, there is high demand for experts that not only possess technical provenience, but are also familiar with cyber defence operations. The major problem is that many important aspects of real-life cyber security, especially related to stress and decision-making based on limited information, cannot be taught in the classroom, but need to be experienced in a setting that is as close to actual real-life situations as possible. Still, CDCs are currently hardly present in traditional tertiary education in the field of security. Setting up an educational CDC is far from trivial, as there are several challenges to be solved:
- The infrastructure required to simulate real life requires a dedicated infrastructure.
- For the simulation of incident response, a so-called “war room”, a dedicated room for information visualisation and decision-making, has to be established.
- In addition, dedicated workplaces for analysts need to be set up that allow for the analysis of complex attack scenarios in the midst of a sea of information and sensor data.
- Since in an educational setting, specific attack scenarios against well-defined infrastructures need to be taught and analysed, these attacks and infrastructures need to be simulated. Thus, a simulation engine allowing for varying scenarios needs to be developed.
- In addition, simulations purely based on artificially conceived data lack details due to the enormous amount of data that is available in real life attacks. Thus, it is beneficial to use data gathered through actual attacks in the simulations that needs to be packed in the form of well-defined scenarios fit for training the students.
The teaching CDC works like a "teaching hospital" with the approach of "clinical clerkship" and "residency". In this approach, students will learn on the job with pseudo-real data and incidents under the guidance of the teaching faculty. This puts students in a position, upon graduation, to strengthen the cyber security field, which now has much more demand than there are highly qualified professionals available.
This is exactly where the “Educational CDC” (eduCDC) of the FH St. Pölten comes into play. By integrating the teaching CDC into a wide variety of courses on a wide variety of topics and with the help of different scenarios, our students can gain this important experience, and they can virtually move in a (simulated) real situation, with all the additional characteristics available, such as stress, unclear objectives and technical challenges. This also provides much-needed practical experience (hands on the job) as an optimal preparation for professional entry, with a focus on the following key competencies of our students: systems monitoring in order to detect vulnerabilities and ongoing attacks, digital forensics of system components to find the root causes of security incidents, penetration testing for the proactive detection of vulnerabilities, malware analysis for the detection of (previously unknown) malicious software ,and threat intelligence that analyses state-of-the-art attacks in order to be able to react in a timely manner and with profound countermeasures. Aside from this technical level, we also focus on security management for the identification and assessment of risks, as well as disaster recovery, focusing on the restoration of systems after successful attacks. This is all rounded off with lessons in training security awareness for reducing the human attack surface.
Summarised, the introduction of the eduCDC into our curricula is a novel concept enabling us to provide our students with the most cutting-edge security education.
Link:
[L1] https://www.fhstp.ac.at/de/campus/labore-und-ausstattung/cyber-defense-center
References:
[1] Directive (EU) 2016/1148 of the European Parliament and of the Council of 6 July 2016 concerning measures for a high common level of security of network and information systems across the Union
[2] Miller, J.N. and Butler, R.J., 2021. National Cyber Defense Center: A Key Next Step toward a Whole-of-Nation Approach to Cybersecurity. Johns Hopkins University-Applied Physics Laboratory.
[3] O'Reilly, C., Bustard, D. and Morrow, P., 2005, May. The war room command console: shared visualizations for inclusive team coordination. In Proceedings of the 2005 ACM symposium on Software visualization (pp. 57-65).
Please contact:
Peter Kieseberg
St. Pölten UAS, Austria











