by Gabriele Spini and Alex Sangers (TNO)
Social welfare programmes are complex, and individuals who might be entitled to a form of social assistance are sometimes unaware of it. Identifying these individuals is a difficult task potentially requiring large amounts of sensitive personal data; access to these data is regulated by law and typically limited. Cryptographic techniques, however, can help in identifying eligible welfare beneficiaries while minimising the amount of data that is revealed in the process.
The Netherlands has various forms of social welfare programmes. An institution named SVB (Sociale Verzekeringsbank) is responsible for some of these programmes, including the AIO scheme, a supplementary income provision for retired people. Low income retirees who meet certain criteria are entitled to this provision; however, a survey by the Dutch court of audit [1] estimated that approximately half of the AIO-entitled individuals do not receive it, presumably because they are unaware that they are eligible for it.
The SVB would like to inform the individuals that are potentially eligible for the AIO about this supplementary income provision, but it needs to safeguard the privacy of involved citizens. This safeguard is complicated by the fact that two types of data are essential to identify potential AIO-beneficiaries: household composition and income. While the SVB does know household composition of retirees, income data are known to another institution, UWV (Dutch Employee Insurance Agency). If the income of a relevant household is below a certain threshold, then it is reasonable to assume that the corresponding individual is entitled to the AIO. However, these are personal data and cannot simply be linked. A Privacy Impact Assessment (PIA) has been used to investigate the privacy risks and potential benefits, and simply sharing data between UWV and SVB on this scale has been deemed non-proportional with respect to the European General Data Protection Regulation (GDPR).
Therefore, TNO (the Dutch Organisation for Applied Scientific Research), Novum (the innovation lab of the SVB), the SVB itself and UWV have started a research project to investigate whether advanced cryptographic techniques can enable the SVB to identify potential beneficiaries of the AIO in a privacy-preserving manner.
Using cryptographic techniques for privacy-preserving data analysis
Cryptographic techniques, and in particular, Secure Multi-Party Computation (MPC), can provide a solution to this problem. Such a solution should allow the SVB to identify which households in their database have a cumulative income that is below the relevant AIO-threshold, but without revealing any extra information about this income. Similarly, UWV should not obtain any information about household composition or on which individuals may be entitled to the AIO.
Several approaches and techniques are possible within MPC; for this project, Homomorphic Encryption (HE) was selected. Intuitively, HE is a form of encryption that enables computations to be done on encrypted data; decrypting these modified ciphertexts yields the result of the computation on the original data. HE was selected for two main reasons: first, it is inherently “asymmetric” (compared to other popular MPC techniques such as Secret Sharing), which means that one organisation takes a lead role and needs to perform most computations; this is important for the AIO-problem, as the primary responsibility lies with one party: the SVB. The second advantage of HE is that it can be more readily connected with the existing IT infrastructure of the SVB and UWV.
Secure solution with homomorphic encryption
The developed solution works in five steps (see Figure 1). In the first step (I), the SVB sends to UWV a list of identifiers of individuals in their database and, if applicable, of their partner. UWV then gathers the gross income data of these individuals, encrypts them with an HE scheme and sends the encrypted values back to the SVB (II). At this point, the SVB computes encryption of (approximated) net income data per individual, and then per household (III). The fourth step (IV) is to compare these encrypted income values with the relevant threshold; due to the type of encryption scheme used, this step requires some interaction with UWV, which will nevertheless learn no information as a result of this step; the reader can refer to [2] for more details and to [L1] for an open source publication. Eventually, the SVB thus obtains a list of individuals whose cumulative household income lies below the relevant threshold (V).
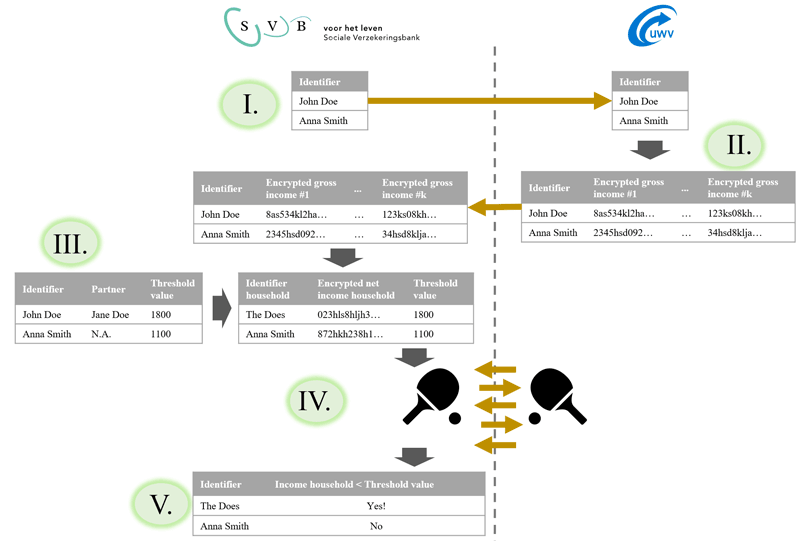
Figure 1: High-level visualisation of the solution.
Results
A Proof-of-Concept was developed within this project, simulating the two data parties SVB and UWV with servers in two different Dutch cities. Experiments were run on synthetic data, showing how the solution scales linearly in the number of involved individuals; preliminary results on non-optimised code yield a run-time of roughly 10 hours for 8000 households: more than non-private computation, but in line with requirements of the SVB and UWV, and with plenty of room to improve efficiency.
Aside from these technical results, a PIA has been written to argue that the data usage is, in this case, proportional to the expected benefit, and is under scrutiny by the relevant stakeholders.
Future work
Given the promising results obtained in this first phase, a follow-up pilot has been started to assess the impact of the solution on real data. The pilot will identify a first batch of 1000 potential AIO-beneficiaries and evaluate the effectivity of this proactive policy.
Link:
[L1] https://github.com/TNO-MPC/protocols.secure_comparison
References:
[1] Algemene Rekenkamer. (2019). Ouderdomsregelingen ontleed, https://kwz.me/h6f
[2] T. Veugen: “Correction to “Improving the DGK comparison protocol”, IACR Cryptology ePrint Archive, 2018”, https://eprint.iacr.org/2018/1100.pdf
Please contact:
Gabriele Spini
TNO, the Netherlands
Alex Sangers
TNO, the Netherlands











