by Alessio Bianchini, Elena Sartini and Luigi Briguglio (CyberEthics Lab.)
Security is a mandatory requirement for critical infrastructures that are increasingly threatened by cyber-attacks. However, when designing cyber-shield systems to protect assets and networks we must also consider other fundamental dimensions. This article presents the experience of CyberEthics Lab. defining and applying a holistic approach based on privacy, ethics, security and social dimensions.
Normalcy in daily life relies on vital systems (also known as critical infrastructures) such as transportation, communication, industry, finance, disaster response, water and energy. These infrastructures are continuously monitored and maintained to guarantee that their day-to-day operations can continue uninterrupted by failures, as well as to mitigate potential physical and cyber threats. The Electrical Power and Energy System (EPES) is one of the most complex infrastructures, and its disruption may have huge cascading impacts on other critical infrastructures. The EPES is evolving towards the integration and potential convergence of physical operational technology and cyber information technology through the adoption of industrial internet and internet of things (IOT) [1]. In this context, the PHOENIX project [L1] aims to offer a cyber-shield armour to European EPES infrastructure, enabling cooperative detection of large-scale, cyber-human security and privacy incidents and attacks, guaranteeing the continuity of operations and minimising cascading effects in the infrastructure itself, the environment, the citizens and the end-users at reasonable cost. To be effective, such cyber-shield armour has to be applied to organisational, communication, technological and process frameworks. Indeed, EPES process data from a huge number of edge network nodes (e.g., smart meters, gateways, primary and secondary stations, SCADA and control rooms). As a consequence, traditional EPES development and operation process, which is mainly driven by functional and security requirements (also known as DevSecOps process), is not applicable, and it is vital to pay attention to a wider set of perspectives, including privacy and data protection, ethics and social concerns.
The PHOENIX project aims to reconcile technology development activities with privacy, ethics, security and societal concerns, and to this end an ad hoc methodology has been developed and implemented: the PRESS framework. To enable a harmonic dialogue between technical components and legal/ethical issues, we have drafted a comprehensive tool for all the companies involved in the project, which follows four steps (see Figure 1):
- definition of the conceptual framework in which the technological solution was intended to be placed and with which the desired solution should find a way to dialogue in harmony;
- identification (i.e. logical deduction from the conceptual framework) of the compliance requirements for the final design of the technological solution;
- juxtaposition of the requirements identified with potential concerns/threats which might have originated from their non-compliance, alongside guidelines and policies that aim to avoid (or at least mitigate) the occurrence of threats/concerns;
- definition of a checklist with the translation in technical language of the “conceptual” requirements, relevant concerns/threats and policies, alongside the most apt technical components. The latter is a valuable tool, to be shared between technical teams and auditors, for monitoring the appropriate evolution of the technology implementation, enacting the compliance assessment, and reporting tests and evidence for qualifying the delivered artefact.
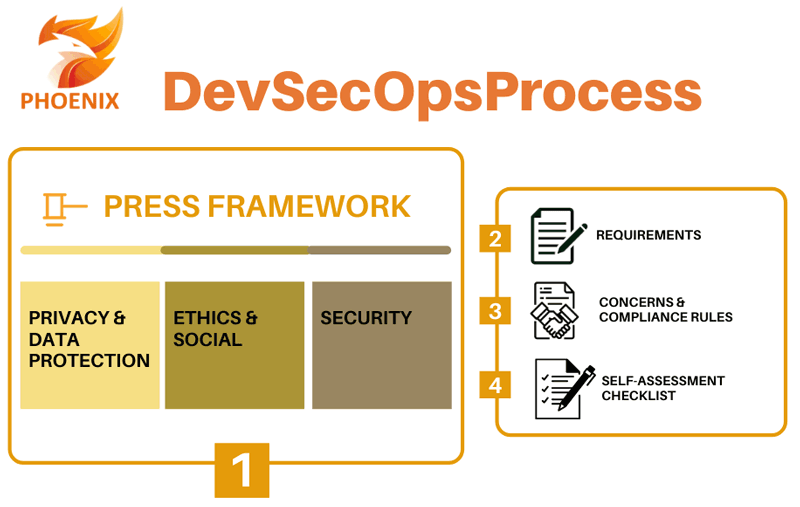
Figure 1: Privacy-by-Conception in PHOENIX DevSecOps process.
Although this approach was defined within the context of the PHOENIX project, it can easily be applied in other contexts. Indeed, the ultimate goal of this methodology is to reconcile legal and ethical requirements with the necessities connected to the deployment of technology.
The PRESS Framework established in PHOENIX evolves the usual approach of the DevSecOps paradigm by introducing the analysis and validation of privacy and data protection, ethics and social, and security dimensions at the point of conception of the technology, ushering in a holistic assessment. Specifically, the “PRESS Checklist” (step 4 of PRESS Framework) has been defined with an 18-go/no-go steps checklist for self-assessment of DevSecOps tasks. All the actors involved in the PRESS-based assessment will use and adapt this checklist for performing the specific checks, in order to satisfy both specifications and PRESS recommendations. This checklist provides developers with flexibility to adapt acceptance constraints and rules based on their specific component specification and development, as well as the possibility to refine template during the life-cycle of components.
To this end, the PRESS Checklist is an effective tool for driving the specification of the components by taking care of the PRESS recommendations and the suggested mechanisms and techniques to address them, as well as to trigger warnings during the development process and flag where support is required from the ethics team and committee.
As mentioned above, EPES deals with a huge amount of data from different sources. PHOENIX ensures that those data are organised and managed in such a way that organisations can meet enterprise business needs along with legal and governmental regulations. A blockchain-based privacy protection enforcement (PPE) mechanism guarantees better protection for personal data in compliance with the GDPR [2] by providing the following features (see Figure 2):
- express consent required to process data;
- the right to rectify given consent;
- more and clearer information about processing;
- the right to notification if data is processed/compromised;
- immutable data access log.
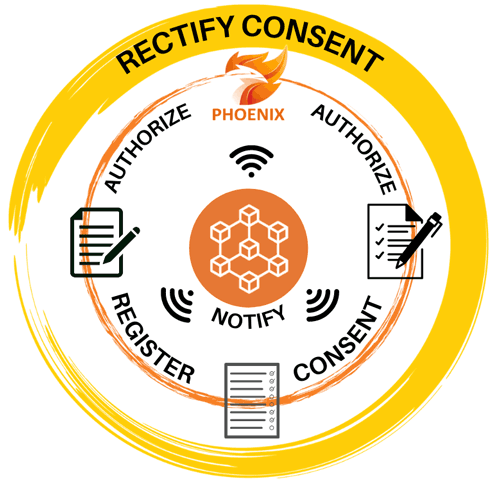
Figure 2: Blockchain-based Privacy Protection Enforcement features.
In PHOENIX, the concept of “Advanced Permission” has been introduced. It comprises two concepts: Consent and Permission.
Consent represents, as stated in Art.4(11) of the GDPR, the data subject’s agreement to the processing of personal data relating to him or her, whereas Permission is an abstract concept that represents the system’s agreement (or disagreement) to the processing of that specific data based on the Consent status. The combination of that concept of “Advanced Permission”, together with blockchain technology and the PRESS framework represents one of the biggest challenges that the PHOENIX project is addressing.
The PHOENIX project received funding from the European Union's Horizon 2020 research and innovation programme under Grant Agreement No.832989.
Links:
[L1] https://phoenix-h2020.eu/
[L2] https://www.cyberethicslab.com
References:
[1] Bailey, et al.: “The energy-sector threat: How to address cybersecurity vulnerabilities”, 2020, https://kwz.me/h6V
[2] Regulation (EU) 2016/679 General Data Protection Regulation (GDPR), https://eur-lex.europa.eu/eli/reg/2016/679/oj
Please contact:
Luigi Briguglio
CyberEthics Lab., Italy











