by Philipp Lämmel (Fraunhofer Institute for Open Communication Systems FOKUS), Stephan Borgert, Lisa Brunzel, ([ui!] Urban Software Institute GmbH), and Paul Darius (Fraunhofer Institute for Open Communication Systems FOKUS)
Digital transformation, innovations and increasing data collection in the field of administration and urban development are opening up more and more opportunities to incorporate urban data into key decision-making processes for our society. This dynamic decision-making basis influences the response of security and administrative authorities, which can lead to increased vulnerability to external attacks. The KIVEP project demonstrates how AI-based anomaly detection can be used in Internet of Things (IoT) networks to identify potential threats.
Information and Communication Technology (ICT) has led to the generation of vast amounts of data in all sectors, fostering interconnectedness. Smart cities use this data to improve areas such as transport, energy, water and waste management, climate monitoring and civil security. It is important to protect data used in decision-making and thus, IT security must be deeply integrated in secure smart cities. Advanced Deep Intrusion Detection Systems (Deep IDS) help distinguish normal traffic from potential attacks. As more smart cities and connected devices are created, the amount of sensitive data being sent increases. Research on smart city security, such as the KIVEP project [L1], looks at ways of preventing and detecting attacks on IoT devices.
Practical Example: AI-based Anomaly Detection
IoT is heavily used to collect data in smart cities. This is done by connecting small computers with sensors or actuators to the Internet. For example, in LoRaWAN, this is done through LoRaWAN network servers (LNS) and gateways. Gateway-level protocol anomaly detection requires insight into end-to-end encrypted packets. A simple solution would break end-to-end security. However, if a gateway is compromised, an attacker could access all data traffic from connected IoT devices. To address this, [ui!] and Fraunhofer FOKUS initiated the KIVEP project [L1] to enable privacy-preserving protocol anomaly detection on DIN SPEC 91357 compliant Open Urban Platforms [L2], hereby enhancing system robustness and improving overall security.
What is Anomaly Detection?
Anomaly detection is the problem of finding patterns in data that don’t match what’s expected [1]. These patterns that don’t fit the norm are often called anomalies or outliers. Thus, anomaly detection can be used to find attacks in IT security. Here, an abnormal pattern in network traffic could for example mean that a computer is sending sensitive data to an unauthorised target [2].
A simple approach to anomaly detection is to define a normal range and declare any observation outside this range as an anomaly. However, this approach can be challenging for several reasons [1]:
- It is difficult to define a region as “normal” that encompasses every possible normal behaviour. In addition, the line between normal and abnormal behaviour is often difficult to draw precisely.
- When anomalies are the result of malicious actions, the malicious aggressors often adapt to make the anomalous observations appear normal, making the task of defining normal behaviour even more difficult.
- In many areas, normal behaviour is constantly evolving – including in a smart city – and a current definition of normal behaviour may no longer be representative in the future.
The developed solution can be seen in Figure 1. The middlebox (Figure 1.1 “Middlebox”) is a virtual environment that detects anomalies in network traffic. It can be placed in different locations, depending on the needs of the network. When anomalies are detected, events are created and processed. These mechanisms could be placed directly in the middlebox or in the NOC or SOC.
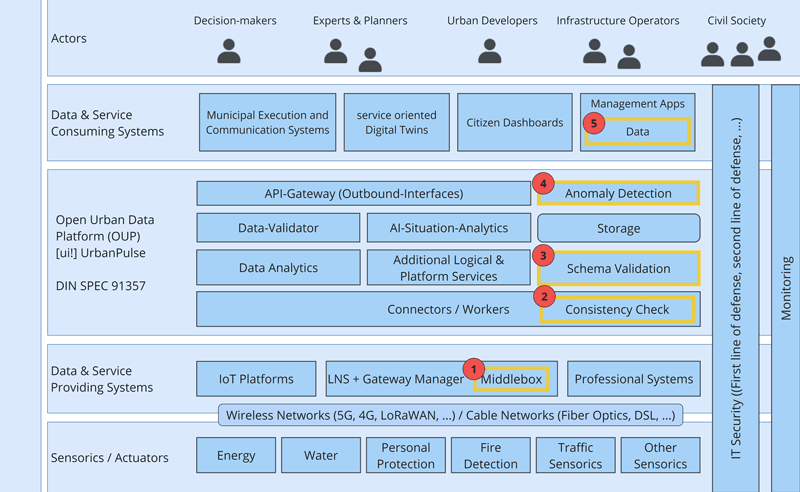
Figure 1: An Open Urban Platform (OUP) with KIVEP's AI-based anomaly detection.
Once the data has been extracted, it is verified to make sure it is correct (Figure 1.2 “Consensus verification”). This is important in allowing the data to be used in a use case. The used metrics can be updated and shown to users at the management app level. Before processing, a schema validation is done (Figure 1.3 “Schema validation”). This checks that the data matches the expected schema and requirements. Schema validation can check data types, barriers, and that all required data fields are present. The data is then processed and archived on the Open Urban Data Platform (OUP).
In the third step, the data is rigorously checked (Figure 1.4 “Anomaly detection”). This involves testing methods that can process large volumes of data. AI forecast results from data analytics are compared with actual data to identify anomalies in the data flows.
Lastly, all results are shown to the operators of the OUP (Figure 1.5 “Data”). If an anomaly is found, the results are shown. Then, standard security measures can be started after being checked.
Conclusion and Future Work
Digital transformations, new innovations and the increasing collection of data in the context of governance and urban development are creating more and more opportunities to incorporate urban data into sovereign and formative decisions for our society. This dynamic basis for decision-making means that attacks with the intention of damaging resources or people can have a major impact on the ability of security and administrative authorities to respond.
OUPs are at the heart, enabling the transfer of verified, refined and validated data. The integration of security mechanisms is essential to guarantee this transfer at a high level of quality. Anomaly detection is an effective and efficient security mechanism. Using a variety of AI-based techniques, anomaly detection can identify patterns in the data that do not match the expected behaviour and react autonomously to these deviations. Due to the dynamic nature of the research field of IT security and cyber threats, the security of public administration decision-making systems will continue to be an important area of current and future research. Predominantly complex research topics such as homomorphic encryption, privacy-preserving mechanisms and the overall integration of security modules based on zero trust will become increasingly important as data-intensive systems help shape our society.
The KIVEP project is funded by the Federal Ministry of Education and Research (BMBF) under the code 16KIS1421.
Links:
[L1] https://www.forschung-it-sicherheit-kommunikationssysteme.de/projekte/kivep
[L2] https://www.beuth.de/de/technische-regel/din-spec-91357/281077528
References:
[1] V. Chandola, A. Banerjee, and V. Kumar, “Anomaly detection: A survey,” ACM Comp. Surv. 41, 3, Art. 15 (July 2009), 58 pages, 2009. https://doi.org/10.1145/1541880.1541882
[2] V. Kumar, “Parallel and distributed computing for cybersecurity,” IEEE Distrib. Syst. Online 6, 2005.
Please contact:
Philipp Lämmel, Fraunhofer Institute for Open Communication Systems, Germany
Stephan Borgert, [ui!] Urban Software Institute GmbH, Germany











