by Stephan Krenn, Thomas Lorünser, Sebastian Ramacher, Florian Wohner (AIT Austrian Institute of Technology)
Performing joint computations on data coming from different data owners offers great potential for more efficient resource use, cost reductions, a reduction in certain industry's carbon footprint and improved societal benefits. However, these synergies are often not exploited because stakeholders have high confidentiality requirements for business-sensitive data and are distrusting of each other. To address this gap, in a series of projects, we have developed provably privacy-preserving and verifiable protocols based on multi-party computation.
The ubiquitous availability of connectivity and cloud services offers a wide range of novel opportunities. One innovation area involves joint computations on data collected from various sources, ranging from sensors to business internal processes, in order to gain novel insights or to optimise existing processes. The potential sensitivity of the data involved in such applications makes their protection of utmost importance to successfully incentivise data owners to participate in joint computations, and thus to leverage tremendous potential.
Besides contractual agreements and legal obligation on data protection, cryptographic research on privacy-preserving federated computation has leaped forward over the last decades towards providing technical means with formal and provable security guarantees. Besides, e.g. fully homomorphic encryption, one key enabling technology is secure multi-party computation (MPC), which allows multiple parties to jointly evaluate an arbitrary function without revealing anything about the input data, beyond what can be derived from the computation result itself. In its most secure configuration, even confidentiality against computationally arbitrarily powerful attackers – including quantum attackers – can be achieved. As a result, MPC offers a provably secure alternative to trusted parties: for instance, in the case of sealed-bid auctions, instead of having to reveal secret bids depending on sensitive information about one’s internal cost structure to a trusted notary, MPC allows the bidders to interactively identify the best offer. While only the tenderer obtains the final computation result, no information about the remaining bids is disclosed to any other party in the system.
One caveat of MPC is that its security relies on a non-collusion assumption: if more than a (parametrisable) number of parties collude, privacy and soundness of computation results can be jeopardised. Furthermore, the result of the computation in general cannot be verified by any party not participating in the computation, which may be necessary, e.g. for auditing or transparency reasons. These challenges are addressed by ongoing research activities on so-called verifiable MPC. There, besides the computation result, the MPC nodes also compute a cryptographic and publicly verifiable certificate in the form of a non-interactive zero-knowledge proof of knowledge, proving that indeed the correct computation on valid and legit input data was carried out.
Unfortunately, the complexity of MPC and, in particular, its verifiable version is often considered too high for real-world adoption of the protocols and solutions, especially compared to their non-privacy-preserving counterparts. Within a series of national and European research and development projects, we have studied the feasibility of efficient verifiable MPC for a variety of application cases and found very favourable results.
FFG FlexProd considered the case of a sharing economy, where supply and demand of industrial capacities among potential competitors had to be matched, in order to increase the average load factor of production machines, increase competitiveness, and decrease costs, while at the same time protecting the individual bids of all involved stakeholders [1]. The H2020 SESAR JU SlotMachine project worked on optimising the assignment of airport slots in air traffic management across different airlines at major airports, aiming for minimising costs, delays, and carbon footprint of airlines, while avoiding privileging single players and while keeping business-critical information regarding the internal cost structure confidential [2]. Finally, H2020 KRAKEN developed a marketplace for personal data, allowing end users, data unions, and companies to commercialise their data in a privacy-enhancing fashion, while also ensuring the quality of the sold data products [3].
Interestingly, on a high level, we also identified a generic pattern for decentralised data markets that underlies all use cases, which is illustrated in the Figure 1. In the first step, the data owner commits to their input values without revealing them, and stores these commitments in an immutable manner, e.g. using a blockchain, together with the corresponding inputs for the MPC nodes and proofs that these data items are consistent. The MPC nodes then perform the requested computation, resulting in potentially encrypted fragments of the computation result as well as proofs of correctness. The data consumer may now reconstruct the final computation result, while everybody can verify the soundness of the computation.
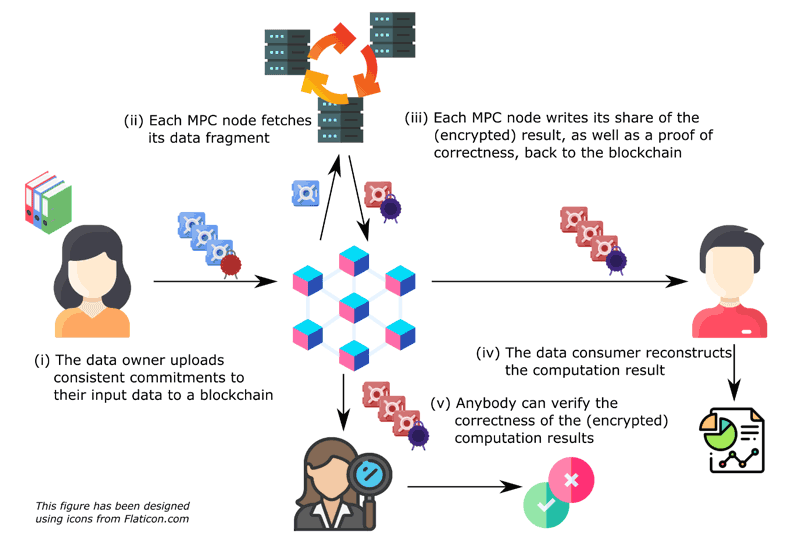
Figure 1: High-level architecture for verifiable multi-party computation.
As a result, we developed a generic architecture for verifiable MPC and demonstrated that it can be instantiated in an efficient manner if the protocols are tailored to the specific needs and requirements of each use case, e.g. in terms of real-time requirements or metadata protection. In particular, by replacing generic approaches to verifiability with problem-specific constructs, the alleged inefficiencies can be overcome for a broad range of computations such as auctions, optimisations and statistics. This proves that data sovereignty and authenticity are not mutually exclusive requirements that prohibit a sharing economy, but can be achieved simultaneously in collaborative environments and data spaces through the use of modern cryptography.
Links:
[L1] https://flexprod.at/de
[L2] https://www.frequentis.com/en/research/projects/slotmachine
[L3] https://www.krakenh2020.eu/
References:
[1] T. Lorünser, F. Wohner, and S. Krenn, “A privacy-preserving auction platform with public verifiability for smart manufacturing”, in ICISSP, 2022, pp. 637–647.
[2] T. Lorünser, F. Wohner, and S. Krenn, “A verifiable multiparty computation solver for the linear assignment problem: and applications to air traffic management”, in CCSW@CCS, 2022, pp. 41–51.
[3] K. Koch, et al., “KRAKEN: a privacy-preserving data market for authentic data”, in DE@CoNEXT, 2022, pp. 15-20.
Please contact:
Stephan Krenn, AIT Austrian Institute of Technology, Austria
Thomas Lorünser, AIT Austrian Institute of Technology, Austria











