by Pavel Minařík
The MyNetScope development project is an example of academic and business cooperation resulting in a platform for advanced network traffic processing, analysis and visualization. MyNetScope overcomes the barrier of traffic content by focusing on traffic characteristics and behaviour patterns and targets the intrusion detection and prevention systems (IDS/IPS) segment of this century.
The MyNetScope platform is a reaction to the current tendency to analyse or process network traffic using statistical methods. While traffic content processing is inapplicable in encrypted traffic, statistical methods are unable to detect precisely targeted or sophisticated attacks. The MyNetScope platform overcomes these limits by performing behaviour-based analysis. It moves down from the application layer to the network and transport layer, reducing the amount of data to be processed but still focusing on individual data flows. Typical tasks for behaviour analysis include dictionary attacks against network services or the misuse of secured hypertext transport protocol (HTTPS), where signatures can't be specified and a statistical approach may detect only massive attacks or HTTPS protocol misuse.
MyNetScope focuses on data flow characteristics and statistics - NetFlow data - and doesn't work with traffic content. NetFlow is an open industry standard defined by Cisco and designed to monitor large-scale and high-speed networks. MyNetScope provides an interactive insight into network traffic. It combines various visualization methods (dynamic mind maps, tables, forms and statistical graphs) in a single workspace and guides the user through visualization showing a greater or lesser level of detail according to the user's preference.
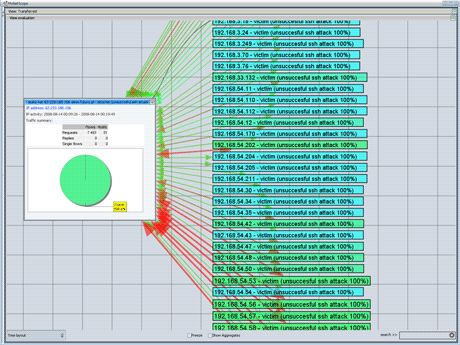
The main purpose of MyNetScope is the detection of anomalies based on behaviour patterns. Behaviour patterns are built upon individual NetFlow data processing and IP address classifications. MyNetScope is able to distinguish between requests and replies (servers and clients) in the network since it implements the Bidirectional Flows Standard as one of the first systems. A successful example of behaviour pattern is dictionary attack against SSH (secured shell) service which was developed at the Institute of Computer Science of Masaryk University. MyNetScope is open to extensions, meaning it is possible to add new detection methods to the application. MyNetScope is also able to integrate data from various sources, eg, it uses DShield portal to support detection methods and identify world-famous attackers.
The MyNetScope development project was started in September 2007 by a Masaryk University spin-off company called Mycroft Mind. Since January 2008 it has run in cooperation with the Institute of Computer Science at Masaryk University, combining the technology provided by the company (visualization engine, memory engine, pattern-matching engine and data integration engine) with expert knowledge from university. Its alpha version was finished in April 2008 and deployed on the university network of Masaryk University in Brno, which comprises about 10,000 computers, with more than 200 million data flows per day. In January 2009 a beta version was deployed and is being used to detect dictionary attacks against the SSH service and in the investigation of security incidents.
MyNetScope is also being used in other research activities, eg, grant Cyber defence of the Czech Ministry of Defence, the goal of which is to provide the knowledge to face organization-specific and other new types of threats. The MyNetScope development team currently focuses on the detection of network infiltration or misuse of HTTP and HTTPS services (tunnelling using these services) and its detection is based on NetFlow data characteristics.
While the application is heading to the domain of IDS/IPS, it focuses on behaviour detection and specific threats which are out of reach of common IDS/IPS. Another advantage is the ability to visualize network traffic and explore suspicious behaviour on the network. The project goal from the point of view of Masaryk University is to transfer the research and development results into industry.
Link:
MyNetScope: http://www.advaict.com/mynetscope
Please contact:
Pavel Minařík
Institute of Computer Science, Masaryk University/CRCIM
Tel: +420 605 852 335
E-mail: minarik![]() ics.muni.cz
ics.muni.cz










