by Maria Bartnes Line
The power industry faces the implementation of smart grids, which will introduce new information security threats to the power automation systems. The ability to appropriately prepare for, and respond to, information security incidents is of utmost importance, as it is unrealistic to assume that one can prevent all possible incidents from occurring. Current trends show that the power industry is an attractive target for hackers. A major challenge for the power industry to overcome are the differences regarding culture and traditions, knowledge and communication, between ICT staff and power automation staff.
Two major technological changes make smart grids interesting from an information security point of view. One is that new technologies are introduced into the power automation systems; commercial off-the-shelf products replace proprietary hardware and software. The other is integration; ICT systems and power automation systems will be much more tightly connected than before. Smart grids consist of complex power grids that interact with equally complex ICT systems. This implies that well-known information security threats like computer break-ins, industrial espionage, malware attacks and denial-of-service attacks will be highly relevant for the power industry in the near future, if not already. ICT security incidents targeting power automation systems, or other types of SCADA systems, are not science fiction - they are already happening. We have had Stuxnet, Duqu and Flame, and we should expect to see more of the kind in the near future.
Power automation systems and general communication oriented ICT systems have traditionally been operated separately. There have been limited, if not zero, logical connections between them, and they have served quite different purposes. The staff operating the two systems tend to have different backgrounds; electric power engineering and computer science. The technology bases are different, and so are management routines. Facilitating and achieving understanding and well-functioning collaboration in this intersection between ICT staff and power automation staff will be the most important task on the way to successful information security incident management for smart grids.
Incident management is the process of detecting and responding to incidents, including supplementary work such as learning from the incidents, using lessons learnt as input in the overall risk assessments, and identifying improvements to the implemented incident management scheme. ISO/IEC 27035:2011 Information Security Incident Management [1] describes the complete incident management process as consisting of five phases; 1) Plan and prepare, 2) Detection and reporting, 3) Assessment and decision, 4) Responses, and 5) Lessons learnt.
Current practice in the power industry
In order to study current practice on how information security incidents are being detected and responded to, and to identify needs for improvements in order to be prepared for the introduction of smart grids, we are now performing qualitative interviews. Our interviewees represent three different roles in a set of large distribution system operators (DSO):
- Chief Information Officer (CIO) /Head of ICT
- Chief of Information Security Officer(CISO)/Head of ICT Security
- Head of control room/power automation systems
We chose these particular interviewees with the intention of identifying current cooperation and possible synergy effects from future cooperation, and viewing the overall management system in general. Both technical measures and human actions are being identified, including how the post-incident analysis is performed. Such an aftermath typically includes information sharing, lessons learnt, and how experiences are transferred into the overall information security routines in the organization.
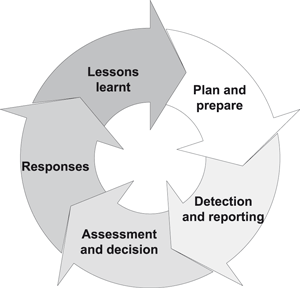
Figure 1: The complete incident management process (ISO 27035)
Future activities
Qualitative interviews give us a large amount of information. There is, however, a risk of getting the “perfect picture”, how things should be done according to the book, and not just actual practice. We would therefore like to follow-up the interviews by running retrospective group interviews at selected DSOs. If, or when, they experience a high-impact incident, we would like to go through the complete course of events in order to understand how the organization responded to that specific incident. Questions we are interested in exploring include how the incident was detected, reported and resolved, in which ways they followed their plans, and if not, how, and in particular why, they deviated from their plans.
We would also like to study smaller DSOs to see whether there are differences regarding their current practices compared to those of the larger DSOs.
There are usually quite a few differences between theory and practice. Observation is therefore also included in our plans for the near future. While the interviews give much insight in how incident management is planned and performed, observing the work in practice will give invaluable additional knowledge. Having knowledge of both theory and practice will enable us to compare the routines actually implemented, suggest realistic improvements, and hence make a valuable contribution to the industry.
The longterm goal is to contribute to an efficient incident management process in smart grid environments.
The project is being carried out at NTNU, in close cooperation with SINTEF and the Norwegian Smart Grid Centre. The project period is 2011-2015.
Reference:
[1] ISO/IEC 27035:2011 Information Security Incident Management
Link:
http://www.item.ntnu.no/people/personalpages/phd/maria.b.line/start
Please contact:
Maria Bartnes Line
Dep. of Telematics, NTNU, Norway
Tel: +47-45218102
E-mail:











