by Nicolas Anciaux, Philippe Bonnet, Luc Bouganim and Philippe Pucheral
The Smart City concept is founded on the collection, sharing and analysis of data that is either about citizens or produced by them, with the view to enhancing efficiencies and the social sustainability of cities. The current Web model which is fully centralised is not appropriate for managing such data as it raises potential privacy abuse and misuse issues. In the Trusted Cell project, we propose the addition of a personal dimension to the Web model: each citizen would possess their own personal data server which would provide tangible privacy and security guarantees and help individuals to share and disseminate their data properly.
In smart cities, the convergence of mobile communication, sensors and online social networks technologies has lead to an exponential increase in the creation and consumption of data which can be linked to individuals (i.e., personal data). These data are considered by the World Economic Forum as “the new oil”, creating an unprecedented potential for new applications and business. However, there are privacy concerns linked to the Web model currently in use and its underlying businesses. Frequent breaches of users' privacy are thwarting enthusiasm for the use of this data.
In smart cities, privacy is a fundamental value, upheld by social sustainability. The personal data given back to citizens can potentially describe all of the activities undertaken in day-to-day lives. To exploit the data, a new sharing and usage model which is more user-centric and prioritises privacy must be invented. Our vision [1] is to launch a sea change in the way data and applications are managed, enabling users to exercise control over how their data is used by introducing trusted cells in the architecture. Trusted cells are units of hardware and software, owned by citizens, which are able to perform data management tasks in a privacy-preserving manner. Our goal is (i) to provide data management and access control techniques embedded into trusted cells which limits the personal data exposed to the services and applications to a minimum subset; and (ii) to rely on trusted cells to implement a usage control model which protects the personal data used by applications against unexpected disclosures once they have left the security sphere of a trusted cell.
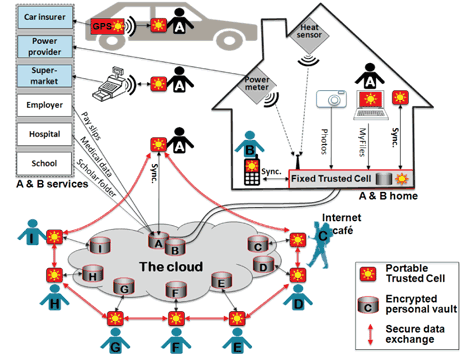
Our approach is based on the vision that privacy-preserving trusted cells, i.e., trusted gateways deployed at home (fixed) or in users' hands (portable), can enforce a usage control model in connection with an untrusted cloud infrastructure. From a technical point of view, the challenges associated with this approach are:
- Developing trusted cells which provide strong security guarantees: in a Smart City, many devices can be considered as potential trusted cells including microcontroller based tokens (e.g., SIM cards or sensors) or mobilephones endowed with an ARM Trustzone processor. Preliminary proposals start addressing the support of relational operations like selection, projection and join within secure microcontrollers [2].
- Designing usage control models, as well as the mechanisms needed to enforce them. We are currently exploring a solution which relies on two building blocks that enforce access and usage control models when the data is transmitted outside the trusted cell to perform a computation. We designed and implemented a set of rich operations within the trusted cell that can be combined to reduce the computations to be performed outside the trusted cells. Then we investigated solutions based on the definition of sandboxed computation containers, that are able to connect to the trusted cell and extract the raw data whilst guaranteeing that unexpected data disclosures will not occur. We expect that these efforts will give rise to a new paradigm for the design of privacy preserving, user-centric applications.
- Global and anonymous computations. To compute results at a population-level, a large number of trusted cells may be required. The aim is to only reveal the results, but organize the computation so that the raw data and their owner’s identities remain hidden. Large sets of trusted cells with limited resources and potentially, low connectivity, may be involved. The feasibility of this approach has been illustrated in previous work [3] which addressed the problem of Privacy-Preserving Data Publication in this context. Computing regular queries, e.g., aggregations to discover overcrowded roads or conduct public surveys, is still an open issue.
Link:
CityLab@Inria Project Lab on Smart Cities: http://citylab.inria.fr
References:
[1] N. Anciaux et al: “Trusted Cells: A Sea Change for Personal Data Services”, in CIDR, 2013.
[2] N. Anciaux et al: “MILo-DB: a personal, secure and portable database machine”, in Distributed and Parallel Databases 32(1), 2014.
[3] T. Allard, B. Nguyen, P. Pucheral: “METAP: revisiting Privacy-Preserving Data Publishing using secure devices”, in Distributed and Parallel Databases 32(2), 2014.
Please contact:
Nicolas Anciaux
Inria and University of Versailles, France
E-mail:











