by Abdessamad Imine and Michaël Rusinowitch
Designing secure collaborative applications has become a hot topic in the area of mobile devices, posing challenging problems such as data management and security.
Smartphones (or mobile computing devices) are proliferating globally. According to a study by comScore [1], by December 2012, more than 125 million people in the USA alone owned smartphones. These mobile devices provide a variety of networking options such as GSM, GPRS, Bluetooth and Wi-Fi. Therefore, smartphones are becoming the device of choice for people to collaborate with family members, friends and business colleagues/customers. They enable us to communicate not only by telephone, by email and short messages, to play games, to share information, organize videoconferences, and coordinate business events.
The adoption of collaboration via smartphones relies on critical factors such as network coverage and security concerns. Collaboration may involve mobile users located in the same limited geographical area, yet connected via wireless channels, which can be less reliable and offer lower data rates than traditional wired ones. Moreover, the amount of personal/corporate data stored in mobile devices has increased. Sharing such data requires preventive security and privacy mechanisms to protect and regulate access to this shared data by other users.
The CASSIS project team at Inria Nancy Grand-Est has designed and developed a decentralized and secure shared calendar, which can be easily deployed on ad-hoc networks of smartphones [2]. Unlike shared calendars such as Google Calendar, our collaborative application ensures privacy and confidentiality of calendar events since it is independent of any third-party or big company servers.
The calendar enables users to share their calendar events with selected users in a dynamic group (users can join or leave the group at any time), and is as responsive as a personal calendar. This high responsiveness is achieved by replicating the shared calendar at each participating user. The consistency of these replicas is maintained in a decentralized way (without a central coordination point) using Operational Transformation (OT) approach.
To prevent unauthorized access by illegal users, our shared calendar is endowed with a flexible access control mechanism where each user can define an authorization policy for controlling access to its proper calendar events. Furthermore, all authorization policies are replicated at the local memory of each user in order to ensure low latency for access rights checking. Thus, a user will own two copies: the shared calendar and the access data-structure. It is clear that this replication allows for high data availability since when users want to read or update the shared calendar, this manipulation will be granted or denied by controlling only the local copy of the access data-structure. Due to the out-of-order execution of the shared calendar's updates and the authorization policy's updates, we have used an optimistic approach that tolerates momentary violation of access rights but then ensures the copies to be restored in valid states with respect to the stabilized access control policy.
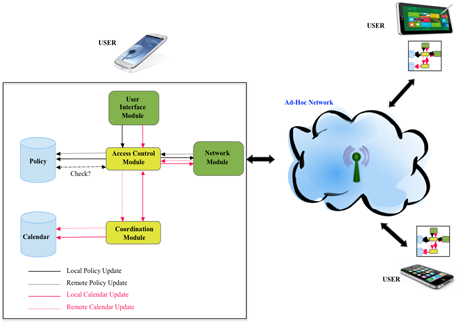
Figure 1 shows the components of our decentralized and secure shared calendar: a user locally manipulates his or her copies (the shared calendar and its authorization policy), and the remote updates from other users (arriving by means of ad-hoc networks) are processed. When a user intends to update his or her local copy of the shared calendar, this update will be granted or denied by checking the local copy of the policy. Once granted and executed, the local update is processed by coordination and access control modules in order to be wrapped by some meta-information, which are necessary to enforce the calendar consistency and its authorization policy, and next it is broadcast to other users. As for the remote calendar update, the access control module checks whether or not this update is authorized and, if granted, sends it to the coordination module for further processing to maintain the calendar consistency before its immediate execution on the local copy of the shared calendar. Note that individual users administer their own proper calendar events. Thus, a user can define an authorization policy on which access rights for other users can be specified. When an administrator modifies a local policy by adding or removing authorizations, this modification is sent to other users in order to update their local policy copies.
Our research work is funded by the European project FP7 NESSoS.
Links:
http://www.loria.fr/~imine/tools/home.htm
NESSoS: http://www.nessos-project.eu
References:
[1] comScore, comScore reports December 2012, U. S. smartphone subscriber market share, press release, February 6, 2013
[2] J. Achara, A. Imine and M. Rusinowitch: “DeSCal - Decentralized Shared Calendar for P2P and Ad-Hoc Networks”, in IEEE ISPDC 2011, Cluj-Napoca, Romania, 2011, pages 223-231.
Please contact:
Abdessamad Imine
University of Lorraine and Inria Nancy-Grand Est
E-mail:











