by Engin Kirda
The Android operating system is a burgeoning platform for deploying mobile applications to users, with more than 550,000 activations per day and an approximate 75% share of the global smartphone market that eclipses the once-dominant Apple iOS [1,3]. This trend is expected to continue, considering that Android's liberal licensing structure, open development environment, wide adoption across multiple hardware manufacturers and carriers, and modern end-user experience make it an attractive platform for both civilian and military use.
The Android security model is a particularly compelling reason for security-conscious organizations to adopt Android as a platform for developing and distributing mobile applications. In this security model, applications must declare a set of permissions that describes the set of privileged actions that might be performed during execution. Examples of such actions include accessing camera data, determining the location of a device, or placing phone calls. Prior to installation, the user must explicitly approve the set of permissions requested by the application. During execution, the Android OS is responsible for ensuring that the application only performs those privileged actions that have been approved by the user.
This containment-based approach to preventing malicious behavior has the benefit of potentially high scalability, since Android applications are not necessarily subject to a manual review process (as is the case for iOS applications distributed in Apple's App Store). Unfortunately, the discovery of Android-based malware in the wild has prompted concerns that the Android security model is inadequate, especially if Android devices are to be adopted in high security environments (eg, the US Department of Defense, the European Commission, etc.) [2] A major drawback of the platform's approach to security is its reliance on user security awareness to detect potentially malicious applications. Specifically, most users are not possessed of the requisite motivation or security knowledge to determine whether an application legitimately requires a declared set of permissions, or to determine whether an attack has occurred at runtime. Therefore, there is a clear and pressing need to supplement the Android security model with the means to detect malicious code and remove the applications that contain such code from Android marketplaces.
Given their centralized nature, Android application marketplaces are well-suited as a venue for deploying static analyses to detect potentially malicious behavior in Android applications. Static analysis has the significant advantage that the entire program code can be analyzed, and thus, it is possible to guarantee the absence of certain, malicious behaviors. This is crucial for governmental stakeholders who might place a significant amount of trust into their applications. Furthermore, marketplaces also present an opportunity to deploy application instrumentation frameworks to remove malicious behavior or harden vulnerable applications against known classes of attacks prior to application installation.
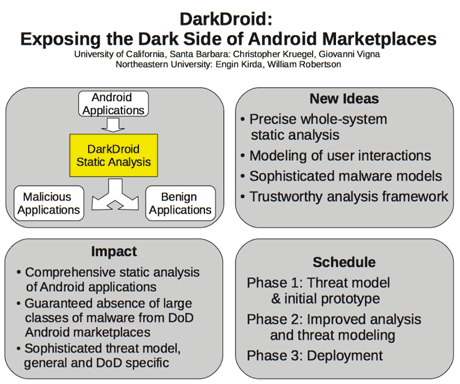
DarkDroid is a joint project between Northeastern University in Boston and University of California, Santa Barbara, that is being sponsored by DARPA since 2012. The goal of DarkDroid is to research static mechanisms for proving the non-existence of malicious code in Android applications. We use scalable and precise static analyses on Dalvik bytecode to discover attacks ranging from privacy violations to unauthorized modifications to critical sensor data. Using the results of our analyses, our tools can then excise the malicious code or harden other apps against attack.
Static code analysis has come a long way; it is nowadays an accepted technique that is routinely used for examining large source code repositories for the presence of bugs and security vulnerabilities. In most scenarios, the goal of a static analyzer is to find as many program flaws as possible rather than to guarantee the complete absence of bugs. While this unsound approach makes the analysis scalable and results in few false positives, it fails in the presence of malicious code. The reason is that malware authors write their programs to specifically exploit the difficult corner cases that an unsound analysis misses. Hence, we require a precise static analysis that accurately handles such difficult cases.
In the case of Dalvik (Android) applications, we identify two main challenges for precise analysis: First, programs make use of complex data structures (such as hash tables) and polymorphic classes with virtual methods. Second, Dalvik applications interact with the user in non-trivial ways, and multiple applications can collude (exchange messages) to achieve a single, malicious goal. We propose novel static analysis techniques that improve the precision of the analysis (and data-flow tracking) when facing complex data structures, user interaction (through intents), and virtual method calls. This guarantees that we will identify and capture malicious code with a low number of false positives, even when malware authors attempt to obfuscate their actions.
Another significant problem is that the absence of a particular class of malicious code does not imply that the application is not malware. In particular, it is crucial that the analysis guarantees the absence of a broad and diverse range of malicious behaviors for the analysis to be useful. In DarkDroid, we are working on novel ways to characterize malicious activity. First, we leverage data-flow analysis to capture malicious code that aims to breach confidentiality. Moreover, we extend data-flow tracking with a fine-grain value set analysis to distinguish cases where certain data elements are legitimately transmitted from cases where unintended information flows occur. Finally, we introduce code patterns that represent attacks against integrity and availability of data, such as patterns that indicate that the program tries to draw an unnecessary amount of energy from the battery.
If successful, the impact of this project will be significant. In particular, DarkDroid will guarantee the absence of broad classes of malicious code from Android applications. Given the anticipated low false positive rates and the detailed output to render human analysis easy, we believe that it is possible to detect malicious applications before they are deployed on an Android marketplace.
References:
[1] GOOGLE, INC. 2011 Q2 Earnings Conference Call Slides, July 2011, http://kwz.me/01
[2] MCAFEE, INC. McAfee Q2 2011 Threats Report Shows Significant Growth for Malware on Mobile Platforms, August 2011, http://kwz.me/02
[3] GOOGLE, INC. Advanced sign-in security for your Google account, February 2011, http://kwz.me/05
Please contact:
Engin Kirda
Northeastern University, USA
E-mail:











