by Jan van Eijck and Floor Sietsma
When you send an email message to more than one address using the Cc: field, all recipients see the same message, including the To: and Cc: fields. Sending a message to undisclosed recipients (using Bcc) has a quite different communicative effect: no common knowledge about the recipient list is created. If a communication network is complex and lots of messages pass through it, it becomes a real challenge to trace who has learnt what from the communication. This challenge is taken up in a project at CWI that started recently.
Social interaction protocols are specifications for carrying out tasks with specific social goals, such as fair division of desirable goods, rational decision making in groups, voting, creation of common knowledge, and so on. Perhaps the simplest fair division mechanism is the well known ‘Cut and Choose’ protocol. Two agents are dividing a set of items X, and they agree to let one of them divide X into two subsets A and B, and next leave the choice between A and B to the other agent. In general, the two agents will value the items in X differently. Indeed, as was already observed by H. Steinhaus in 1948, if the two parties have different estimations, then there exists a division that gives both parties more than their due part; "this fact disproves the common opinion that differences in estimation make fair division difficult".
Issues of knowledge and ignorance are relevant in such protocols. Take ‘Cut and Choose’, and suppose both parties are ignorant about the valuation of the other party. Then the party that chooses has the advantage over the party that makes the cut. For since the one who makes the cut does not know which items the other person values most, the best she can do is make equal piles according to her own valuation. Although issues of knowledge and ignorance are crucial for analysis of fair division protocols, in traditional studies of ‘cake cutting algorithms’ the role of knowledge is not taken into account.
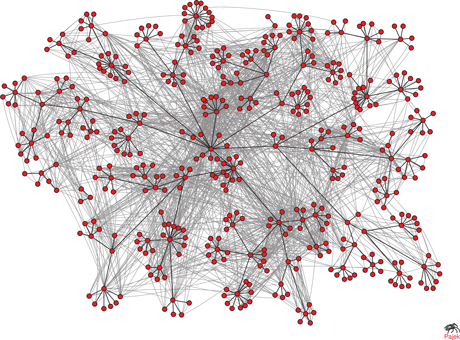
Figure: Email communication between employees of HP Research Lab.
CWI is developing a general framework for studying interaction in social and economic networks, building on epistemic logic and theoretical computer science. As a first step, we are studying the epistemic effects on email message exchanges, including the subtle logical differences between cc and bcc of messages. In follow-up research, we will address the influence of communication links and knowledge of communication links on communication protocols. The nature of the communication links matters to the outcome of a protocol. Consider the decision making process for taking social action. Everyone communicates to their neighbours: "I promise to join the action on condition that I know for sure that at least two others are going to do so as well". Now it depends on the direct communication links between the agents whether collective social action will result or not.
The effects of email communication may seem trivial: if I send you an email, the result will be that you know the information contained in it. But there are more complicated things going on here: I also know that you got this information, and you consider it possible that I sent a BCC of this message to any other person I know. If I do send such a BCC, the third recipient will know that you know, but that you do not know that the third recipient knows. Additionally, I know all this, and the third recipient knows I know this... etcetera.
People intuitively understand all these different levels of knowledge but to express them in a logic is harder than it may seem. This all becomes even more interesting when the number of emails becomes very large. Suppose the director of Google finds out that one of his employees secretly works for Facebook, and he wants to know which information this person can have leaked to the competitor. He could go through all emails this person received one by one in order to determine this, but it would be much more efficient if we could let the computer do this. One of the long-term goals of the research is to automatically visualize information streams within a company, making clear who has which information about basic facts but also about the knowledge of others.
Link: http://homepages.cwi.nl/~jve/
Please contact:
Krzysztof Apt,
CWI, The Netherlands
Tel: +31 20 592 4057
E- mail:
Jan van Eijck
CWI, The Netherlands
Tel: +31 20 592 4052
E-mail:
Floor Sietsma
CWI, The Netherlands
Tel: +31 20 592 4266
E-mail:










