by Raquel Cortés Carreras, Juan Carlos Pérez Baún and Miryam Villegas Jiménez (Atos Spain S.A.)
In the context of EU Horizon 2020 CyberSec4Europe project the medical data exchange demonstrator creates a trusted ecosystem for sharing medical data in a secure and privacy preserving manner.
The personal and sensitive data generated in the health domain including hospitals records, patient records or wellbeing wearable devices (data providers) is growing sharply. This huge amount of health data can be used by health organizations and research laboratories (data consumers) for improving the population’s health. At the same time this information acquire economic value to pharmaceutical industry and insurance companies. These personal and sensitive data needs to be effectively managed in terms of quality, security, and privacy, assuring the integrity and reliability when this information is shared between parties. In the context of H2020 CyberSec4Europe project [L1, L2] the Medical Data Exchange demonstrator addresses these security and data protection challenges to ensure trust between two main actors: the data providers and the data consumers. The use of privacy preserving techniques has been adopted by this demonstrator for creating a trustworthy environment by developing a data anonymisation service (DANS) and a functional encryption service (FE2MED), increasing the user privacy and security when sharing data through a data exchange platform (Figure 1).
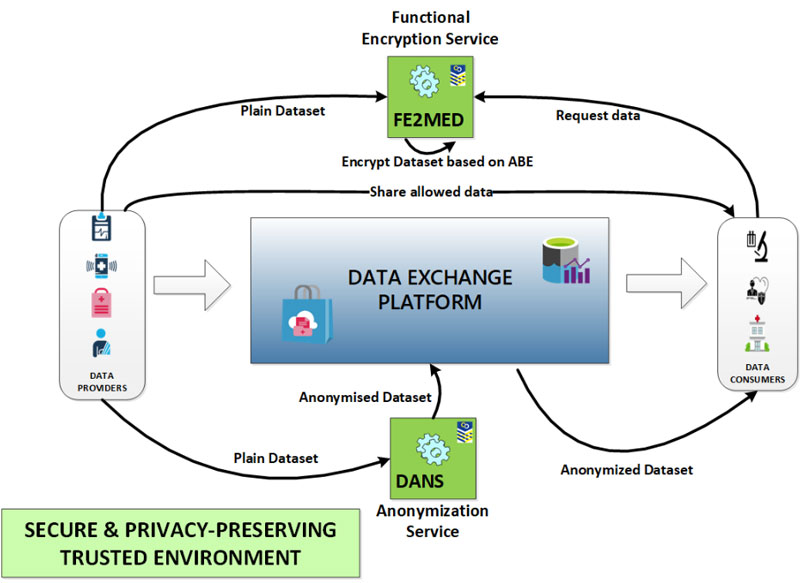
Figure 1: The privacy-preserving techniques anonymisation and functional encryption services create a trusted environment for sharing health records.
Anonymisation tool
The Data Anonymization Service (DANS) is an anonymization tool, developed by Atos, based on an open-source tool named ARX [1]. DANS makes it possible to mitigate tracking and user re-identification by anonymizing sensitive personal data, leveraging k-anonymity and l-diversity privacy models, which enable the application of some privacy criteria over a particular dataset, protecting biomedical data against data disclosure. Preserving data privacy applying anonymisation techniques, helps health stakeholders, such as health authorities, hospitals, research bodies and the private health sector, to be regulatory compliant, as fully anonymised data are considered out of the scope of the GDPR regulation (according to Recital 26 [L3]). Unfortunately, perfect anonymization is not possible, the use of anonymisation algorithms that maximise the utility and the privacy protection is quite difficult. and it is necessary to find a balance between privacy and utility. To this end privacy metrics and privacy risk features are envisage be included in the DANS service in the future.
DANS tool is offered in two flavours for being used by the data providers:
- A java library to be integrated in the data provider legacy systems. Also, this option allows the use of privacy-preserving techniques on the Internet of Things (IoT).
- An anonymization service to be deployed on the data provider premises or in a trusted third party, exposed as a RESTful API. In this case a graphical user interface is provided to the user to facilitate the use of the anonymisation tool and improving the user experience.
Functional encryption tool
The Functional Encryption to Medical Data (FE2MED) service is developed by Atos, based on Horizon 2020 FENTEC project crypto libraries [L4]. The FE2MED tool leverages libraries containing attribute-based encryption (ABE) and inner-product encryption schemes used for preserving privacy during the health data management. This technology allows selective share of the encrypted data in a fine-grained level. Basically, the encrypted data are labelled with sets of attributes and private keys are associated with access structures that control which encrypted data a user can decrypt [2]. This means that, only the allowed users are able to access the encrypted data or the results, ensuring the integrity and the confidentiality of shared data.
The FE2MED service is deployed in the data provider infrastructure, in order to have the full control on the generated key elements. Also, exposes a RESTful API to the users. Additionally, provides a graphical user interface to users for hiding the complexity of the encryption/decryption processes, improving the user experience. While the data provider is able to access to all the FE2MED functionalities, the data consumer only has access to certain features related to the decryption process.
The FE2MED service acts as a trusted entity managed by the data provider. It is in charge of generating cryptographic keys for encryption and for decryption. The two scenarios developed in the medical data exchange demonstrator are the following:
- Share encrypted datasets with different data consumers which can see only specific data. In this scenario the ABE schemes are applied, which give a more fine-grained control of the decryption capacities of third parties.
- Share encrypted results with data consumers which are able to see only the results but not the data. In this case the Inner-product schemes are applied for performing basic (Inner product-simple DDH scheme) or more complex (Inner product- Fullysec Damgard DDH scheme) statistic calculations.
Currently, the FE2MED tool is focused on encrypting health datasets to be shared with third parties, the protection of data generated in the health IoT infrastructure domain (e.g., connected medical devices and mobile devices) will be addressed in the future [3].
Links:
[L1] https://cybersec4europe.eu/
[L2] https://cordis.europa.eu/project/id/830929
[L3] https://gdpr-info.eu/recitals/no-26/
[L4] https://github.com/fentec-project/gofe
References:
[1] F. Kohlmayer et al., “Highly efficient optimal k-anonymity for biomedical datasets”, in: 25th IEEE International Symposium on Computer-Based Medical Systems (CBMS), 2012.
[2] V. Goyal et al., “Attribute-Based Encryption for Fine-Grained Access Control of Encrypted Data”, in Proc. of the 13th ACM Conf. on Computer and communications security, 2006.
[3] N. T. Dang et al., “Applying attribute-based encryption on mobile devices”, in Sci. Tech. Dev. J. – Engineering and Technology, 2020.
Please contact:
Juan Carlos Pérez Baun
Atos, Spain









