by Christoph Schmittner, Egbert Althammer and Thomas Gruber
Certification and Qualification are important steps for safety- and security-critical systems. In Cyber-Physical Systems (CPS), connected Systems of Systems (SoS) and Internet of Things (IoT), safety and security certification should be done in a holistic and unified way. Assurance that a system is safe needs to include evidence that the system is also secure. WEFACT is a workflow tool originally developed for guidance through the safety certification and testing process, which is now extended towards holistic safety and security assurance.
Mission-critical Cyber-Physical-Systems (CPS) often need to follow well-defined safety and qualification standards. Most safety standards demand explicitly or implicitly a safety case, which contains evidence and assurance that all safety risks have been appropriately identified and considered. To generate such a safety argumentation, requirements tracking and workflow support are important. The Workflow Engine for Analysis, Certification and Test (WEFACT) has been developed as a platform for safety certification and testing in the ARTEMIS/ECSEL projects SafeCer, MBAT and CRYSTAL. The final result of the WEFACT supported workflow is the safety case (Figure 1).
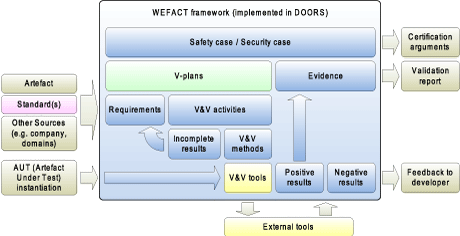
Figure 1: The WEFACT Framework.
WEFACT’s requirements tracking, testing and certification support is based on a workflow derived from the requirements of functional safety standards, but other domain-specific requirements and company-specific practices can also be included. These requirements, together with functional and non-functional requirements defined for the individual application, are stored in a DOORS© database; ‘V-plans’ (validation plans) are defined for these requirements, and their successful execution proves that the requirements are fulfilled. Recently, WEFACT is being developed in the ARTEMIS/ECSEL project EMC² towards a framework for supporting a general assurance case covering all relevant dependability attributes, including safety, security and performance (see Figure 2).

Figure 2: The V&V process as guided by WEFACT.
With increasingly interconnected and networked critical systems, a safety case needs to be aware of security risks because security threats have to be considered as a potential cause for hazards. A security aware safety case includes security assurance in order to demonstrate that a system is safe and secure. The security assurance part of WEFACT is based on the ISO/IEC 15408 (Information technology - Security techniques - Evaluation criteria for IT security (Common Criteria)) and IEC 62443 (Industrial communication networks - Network and system security - Security for industrial automation and control systems). ISO/IEC 15408 defines Security Assurance Requirements (SAR) for different parts of the Artefact under test (AUT). A system is evaluated based on the assigned Evaluation Assurance Level (EAL), which describes a set of SAR. There are seven EAL with increasing requirements on formalism and thoroughness of the evaluation. The V-plan for the AUT describes the responsibilities and activities, based on safety and security standards as well as other sources such as domain-specific and company-specific practices. WEFACT guides the combined process of achieving certification according to safety and security standards. In addition, activities for verification and validation (V&V) are connected to external tools which can be integrated into the workflow engine.
WEFACT supports automated tool integration over Open Services for Lifecycle Collaboration (OSLC), an interoperability standard for the cooperation of lifecycle management tools. Depending on the level of integration, i.e. whether the V&V tool can be called directly via OSLC or command line interface, or a V&V activity needs manual interaction with external tools, WEFACT will be able to conduct the V&V activity more or less automatically and change the requirement status according to the result (<pass> or <fail>). After all V&V activities of the V-plans are conducted successfully, and all requirements are therefore fulfilled, a holistic safety and security case is generated. This so called dependability or assurance case uses an argument notation - for instance, the Goal Structuring Notation (GSN) to demonstrate the assurance that a system is safe and secure.
This work was partially funded by the European Union (ARTEMIS JU and ECSEL JU) under contracts MBAT, nSafeCer, CRYSTAL, ARROWHEAD and EMC² and the partners’ national programmes/ funding authorities.
Links:
http://www.ait.ac.at/wefact
http://open-services.net
http://www.goalstructuringnotation.info/
http://www.ecsel-ju.eu
References:
[1] J. Spriggs: “GSN-The Goal Structuring Notation: A Structured Approach to Presenting Arguments”, Springer Science & Business Media, 2012.
[2] E. Althammer, et al.: “An Open System for Dependable System Validation and Verification Support – The DECOS Generic Test Bench”, in proc. of the INDIN 2007, Vienna, ISBN 1-4244-0864-4, p. 965 – 969.
[3] E. Schoitsch: “An E&T Use Case in a European project”, special session TET-DEC (Teaching, Education and Training for Dependable Embedded and Cyber-physical Systems); in proc. of SEAA 2015, IEEE CPS, to appear.
Please contact:
Egbert Althammer
AIT Austrian Institute of Technology GmbH
E-mail:











