by Johanna Ullrich and Edgar Weippl
The CyPhySec project (Framework to Cyber-Physical System Security) is embedding security in safety control for protecting Cyber-Physical Systems in the presence of adversarial behaviour.
CyPhySec addresses security threats to physical infrastructure operated by information technology (IT), such as water treatment or power plants. Although security incidents of this kind date back as far as the 1980s, attacks on cyber-physical systems (CPS) have been more frequent since the early 2000s [1]. Common targets include transport systems, power and utilities. The metal working industry has also been under attack: last year a steel mill in Germany was compromised when attackers gained access to the relevant networks by means of spear phishing, and ultimately sabotaged physical components of the plant [2]. Also in 2014, numerous European and U.S. energy companies were victims of a hacking group known as ‘Dragonfly’; although the methods were similar (e-mail attacks, malware), cyberespionage seems to have been the main goal [3] – however, in cyber-physical systems it’s just a small step from data theft to damaging physical components or whole infrastructures. Therefore, CPS must be protected as comprehensively as possible.
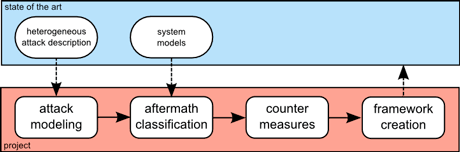
Figure 1: Methodology of the CyPhySec project.
IT is a fast-evolving field in which new vulnerabilities are constantly emerging. Currently, the most common approach to cyber-security is to reuse existing IT solutions, such as: access control, patching, firewalls and encryption; which mainly defend against known attack vectors. The physical component of a cyber-physical system is not necessarily taken into account by these countermeasures, and so, in the absence of further protection, remains vulnerable. Even without this additional challenge, it can be difficult for system operators to keep up with innovations and hazards, and given the complexity and size of cyber-physical systems, this security issue should be addressed urgently. In addition, the possibility of attacks exploiting the dynamic of a system’s physical parts must be considered.
CyPhySec faces the challenge of combining the two diverging points of view of control engineers and computer scientists. The former can predict a system’s reaction to an event, while the latter are able to analyse such events in terms of their security issues. Consequently, CyPhySec aims to develop a multidisciplinary and consistent framework, which focuses on the impact that sophisticated attacks may have on a system’s physical components. We have three specific goals:
- Attack Modelling: This topic has not been comprehensively addressed, and a mutual and consistent method for describing attacks and their aftermaths is still lacking. We aim to bring together the respective fields and systematically determine probable consequences of cyber-launched attacks on physical systems.
- Countermeasures: Current measures for the protection of cyber-physical systems consist either of IT security solutions or of traditional control engineering approaches. We aim to acquire an in-depth understanding of existing countermeasures and include new alternatives that might enable cyber-physical system protection. Such alternatives go beyond traditional IT protection, and aim at integrating defences within the control algorithms themselves towards protecting the CPS from adversarial behaviour that exploits IT weaknesses.
- Consistent notation: Since this is a multidisciplinary project, the documentation has to be understandable by all parties involved to preserve the gained insights and to accelerate their spread within the related fields. Therefore, we are developing a consistent notation, including mathematical, textual and graphical explanations.
The CyPhySec project has been running since January 2014 and is funded by the BRIDGE Early Stage program (a funding scheme of the FFG, the Austrian Research Promotion Agency). The project is carried out by SBA Research in collaboration with Theobroma Systems, both located in Vienna, Austria.
Currently a group of four researchers – electrical engineers and computer scientists – is working on this project and has created a sophisticated collection of software, hardware and mathematical attacks that can be launched against cyber-physical systems; work on a multidisciplinary description of these attacks is also in progress.
Links:
https://www.sba-research.org/research/ projects/cyphysec/
https://www.sba-research.org/
https://www.theobroma-systems.com/
References:
[1] RISI – The Repository of Industrial Security Incidents, http://www.risidata.com/ Database/event_date/desc
[2] R.M. Lee, M.J. Assante, T. Conway: “SANS ICS Defense Use Case (DUC) Dec 30, 2014: ICS CP/PE case study paper – German Steel Mill Cyber Attack”, https://ics.sans.org/media/ ICS-CPPE-case-Study-2-German-Steelworks_Facility.pdf
[3] J. Langill, E. Zambon,
D. Trivellato: “Cyberespionage campaign hits energy companies”, available at http://www.secmatters.com /sites/www.secmatters.com/files/documents/whitepaper_havex_US.pdf
Please contact:
Johanna Ullrich, SBA Research, Austria
E-mail:











