by Michael Baentsch and the IBM LRSC Team
The major challenges in turning the IoT (Internet of Things) vision into a reality are manifold: end-device power consumption, wireless range and penetration, coordination and control, and security. The Semtech LoRa(tm) modulation scheme enables extremely energy-efficient end devices that communicate wirelessly over distances of up to 40km in a single hop. The IBM Long-Range Signaling and Control (LRSC) software enables deploying and securely operating large-scale multi-tenant networks based on LoRa.
Over the next five years, Gartner estimates that more than 25 billion devices will be connected and become part of the IoT covering a broad range of applications from metering to environmental monitoring to waste management to tracking. This number strains the capability of current day technology: A large percentage of the envisioned applications further share some common characteristics that are not well served by the existing IoT infrastructure based on cellular networks. Most importantly, end devices must be able to live on a single set of batteries for extended periods, sometimes up to ten years or even longer. On the other hand, the communication requirements are rather moderate, typically sending a couple of bytes uplink every hour and receiving downlinks even far less often. From an infrastructure perspective, in turn, the challenge is to manage large numbers of end devices while utilizing the available bandwidth in the best possible way. On top, the challenge is to achieve this without sacrificing end-to-end data security and integrity between the end device and the application backend.
The key component for the solution to this problem is the use of a long-range, low-data-rate communications infrastructure that needs fewer base stations to serve simple end devices like smoke detectors, temperature sensors, or smart electrical heating controllers. While several radio technologies exist, one radio technology appears to be most promising: Semtech LoRa. The LoRa modulation scheme has ideal characteristics for many IoT applications by providing a robust, spread-spectrum modulation that can be used both in licensed and license-exempt (ISM) wireless spectrum between 70 MHz and 1GHz. This permits bi-directional low-power transmission using dynamically adaptable data rates from 300 bps up to 50 kbps over variable distances of up to 40 km. This modulation technique has significant advantages when compared with cellular networks and Wifi, including lower cost, good penetration of obstacles, greater coverage over longer distances, and better battery life. Based on the LoRa modulation, Semtech, Actility and IBM Research have created the LoRaWAN MAC specification for the just recently launched LoRa Alliance, an open, non-profit association of infrastructure providers, telecom operators and end-device manufacturers.
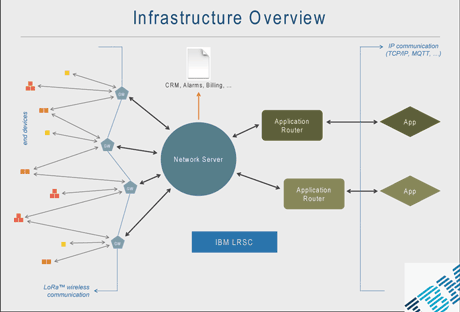
Figure 1: A typical Long-Range Signaling and Control (LRSC) installation comprises a central network server linking hundreds or thousands of radio gateways (GWs) to dozens of application routers. In this way, hundreds of thousands of end devices can establish a secure bidirectional, low-data-rate connection with corresponding Apps, thus enabling millions of small, IoT-type transactions per day per system installation.
To deploy and operate a network of millions of connected sensors in a reliable, efficient, and secure way is a huge challenge, for which IBM Research has developed the IBM Long Range Signaling and Control (LRSC) system. This includes all the software components to deploy and manage a large-scale multi-tenant network of wireless devices using the LoRaWAN protocol. It comprises all functional and security logic distributed over the gateways to a central network server and multiple application routers as well as the corresponding end-device protocol software. End devices may be fixed or mobile and even roam across network boundaries and, according to LoRaWAN may send messages at their own discretion. For downlinks, end devices may fall into different classes according to LoRaWAN: end devices of Class A listen for a downlink only directly after an uplink; end devices of Class B further listen regularly to a network beacon for time synchronization according to some specific schedule; and end devices of Class C always listen when not sending.
In line with the LoRaWAN specification, the system further uses cryptographic authentication and end-to-end encryption of application payloads with device-specific AES128 keys. Most notably, and in line with the LoRaWAN specification, the architecture clearly separates the network operator from the users of the network. All cryptographic (session) keys are unique per end device (i.e., no network-wide keys exist) and the network operators are only enabled to do cryptographic integrity checking without gaining access to the actual user data.
Gateways
The primary role of the gateways is to relay traffic between end devices and the network server bi-directionally: concretely, to add timestamps and metadata to the messages received from the end devices, send messages to the end devices following a schedule set by the network server, regularly broadcast beacons for end devices of Class B, and provide operational meta-information to the network server for network optimization. LoRa gateways managed by IBM LRSC communicate with the network server using TLS (Transport Layer Security) certificate-based authentication, and limit the impact on the network server potentially caused by traffic from malicious end devices. Furthermore, gateways are time-synchronized, provide management commands for the network operator, and allow for automatic updates.
Network Server
The network server functions as the central control center and communication hub, managing the complete infrastructure and scheduling all up- and downlink traffic for potentially millions of end devices while maximizing the use of the available bandwidth. It further keeps the network in an optimal state (e.g., by global data-rate optimization for every single end device), collects usage data for network operation, optimization, and billing, and provides a broad range of management and maintenance interfaces. Billions of events are generated by all entities in the system, e.g., gateways, devices, application routers, conveying not only data-flow related information but also system health and security critical aspects. All these events are persistently logged, and can be queried and analyzed to enable network operators full insight and control over the infrastructure. To ensure fault tolerance, a warm stand-by network server on a remote secondary node can take over using regularly mirrored data.
Application Router
The application routers serve as the interface to the backend application servers with typically one application router per application. As part of this, application routers relay traffic between network server and application servers, authorize LoRaWAN JOIN requests issued by end devices, and serve as the application-level encryption endpoint for the end-to-end user data payload encryption. To ensure fault tolerance, application routers are typically run in a warm stand-by configuration.
The overall system separates the network operator from the application owners, providing privacy, fault tolerance, and security. After large-scale simulation with hundred thousands of end devices, a physical test bed has been built in the laboratory to study and improve the system subject to real-world problems like RF-interference.
Links:
http://www.research.ibm.com/labs/zurich/ics/lrsc/
http://lora-alliance.org/
http://www.zdnet.com/article/25-billion-connected-devices-by-2020-to-build-the-internet-of-things/
Please contact:
Michael Baentsch, IBM Research Zurich, Switzerland
E-mail:











