by Christopher Edwards, Prathyush Menon and Dragan Savic
The capability of modern utility distribution networks to exchange large amounts of data offers huge advantages in terms of efficiency of operation and optimization. On the other hand, the inherent communication network component exposes the overall system to the possibility of malicious cyber-attacks. The resilient operation of such distribution networks presents challenges to control theorists and practitioners alike.
New technologies are revolutionizing traditional water distribution systems. Currently, “smart methods” based on novel ICT technologies are being employed to deliver integrated supply-demand side management for improved efficiency. Although perhaps less well publicized than similar developments in the area of Smart Grids in power distribution networks, the aim of incorporating these new and smart methodologies into water distribution networks is to contribute to the delivery of a sustainable, low-carbon society, thus helping achieve progress towards the European 2020 targets on Climate and Energy. Figure 1 provides an example and an overview of a typical smart water network.
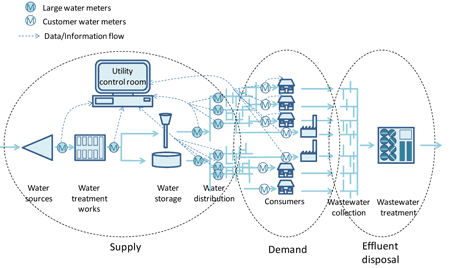
Figure1: Description of the architecture.
The primary source of information is real-time and near-real-time meter/sensor data, reporting pressures, flows and water levels at selected points throughout the water supply/distribution network This is based principally on instantaneous flow, pressure and/or level monitoring at major physical structures (i.e., intakes, treatment works, service reservoirs, pump stations, etc) delivered through a "supervisory control and data acquisition" system (SCADA). This information is augmented by flow and pressure measurements from meters at the entry to District Metered Areas (DMAs) along with selected pressure monitoring points elsewhere within the DMA, with data typically transmitted every 30-60 minutes, principally over a cellular communication network. Thus the intelligent water distribution network above comprises computing/monitoring facilities, valves/pumps (actuators), sensors (measurements), a physical commodity flow (water), reservoirs (source), consumers (sinks) and information flow (associated with actuator commands and sensors). See for example [1]. Such an infrastructure is often referred to as a Cyber-Physical-System (CPS) [2].
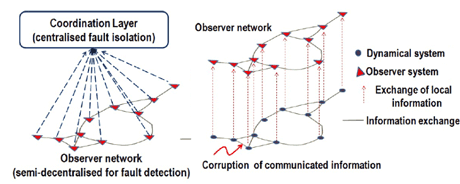
Figure 2: A simple example of a monitoring architecture.
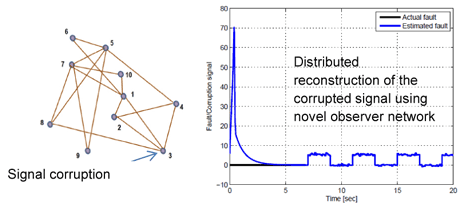
Figure 3: Signal corruption in the network and a reconstructed corruption signal.
Modelling challenges
Models of a cyber-physical infrastructure can be developed based on the underlying physics of the problem: typically there are sources and sinks, and mass/flow/energy balance constraints. At a local level, components and sub-systems can be modelled as individual lumped systems to be represented as generic, continuous/discrete time ordinary differential equations. The modelling of the interconnections between these local or node level elements, must capture both the exchange of information as well as the underlying topology of the physical and commodity flow realization, so that graph theoretic methods [3] can be exploited. Whilst such large-scale systems offer great potential and flexibility in terms of efficient operation, it is extremely important to have an effective monitoring mechanism in place so that failures/threats/risks can be swiftly identified, and suitable decisions can be made to contain and mitigate their effect. For example, timely detection of pipe burst events provides opportunities for water companies not only to save water but also money and energy, and reduce their carbon footprint, and improve their operational efficiency and customer service.
Control Challenges
For efficient functioning of such infrastructure, in addition to optimizing normal fault-free operation, associated security aspects must also be taken into account. Hence the physical layer’s control must be resilient and robust towards cyber-attacks and other malicious behaviour. A highly complex distribution network comprising many interacting, heterogeneous distributed systems, each under autonomous control and reacting to the environment and to cyber and/or physical signals of other systems, requires coordination/control – often in a decentralized or distributed manner - to accomplish a global objective/performance.
Monitoring challenges
One approach to developing monitoring schemes to detect failures/threats is to attempt to extend existing observer-based fault detection and reconstruction ideas to the CPS. In contrast to conventional observer problems, including a copy of the system being monitored internally requires a plethora of actuation and measurement signals from throughout the entire network. This is at best cumbersome and may not even be practical. Different architectures for the observer can be considered depending on which signals are realistically available. These could be classified as centralized (where global information is required), decentralized (only local information is required) and distributed (which involves an exchange of information amongst the observers themselves). Arguably, a scalable and distributed monitoring solution would be best suited to this problem. This is beneficial in terms of the sensor resources required, and hence the overall energy consumption.
Once a monitoring scheme has identified failures or cyber-attacks within the network, it is imperative to take pertinent timely decisions to isolate which of the sub-systems/elements is the root cause. Once isolated within the network, further decisions need to be made so that the operation of the remaining “healthy” part of the infrastructure experiences minimal impact and the effects of the failures/threat contained. However, since cyber as well as physical interconnections are present, an attack/fault on one sub-system may have an impact on the performance of other sub-systems and thereby globally within the network. Owing to possible redundancy within the network it may be possible to recover acceptable overall performance through reconfiguration and thereby achieving self-healing and providing resilience.
References:
[1] D. A. Savić, J. K. Banyard (Eds.): “Water Distribution Systems”, Thomas Telford Limited, 2011
[2] P. Derler, E. A. Lee, A. Sangiovanni-Vincentelli: “Modeling Cyber-Physical Systems”, in proc. of the IEEE (special issue on CPS), 100(1):13-28, 2012
[3] M. Mesbahi, M. Egerstedt: “Graph Theoretic Methods in Multi-agent Networks”, Princeton Series in Applied Mathematics, 2010.
Please contact:
Dragan Savic, Christopher Edwards, Prathyush Menon
University of Exeter, United Kingdom
E-mail:











