by Christophe Ponsard, Jean-Christophe Deprez and Robert Darimont
Engineering Cyber-Physical Systems (CPS) is challenging in many respects, including at the Requirements Engineering (RE) stage. In addition to generic RE techniques that already encompass the system dimension of CPS, such systems can benefit from domain knowledge related to specific requirements, such as accuracy, dependability and security. This knowledge can be structured as a reusable requirements pattern library.
Cyber-physical systems are complex systems with intertwined computation, communication and physical elements, often including human interactions in the loop. The design of such systems goes well beyond traditional embedded system controllers and exhibits characteristics of multi-agent systems. This is quite challenging for the engineering requirements process as it must be able to deal with multiple agents either under (co-)design or located in the environment (including physical processes, devices and human interactions). It also requires software design to be mixed with physical system design, and these two design processes rely on different sets of modelling languages (e.g. logic for computational elements and differential calculus for physical elements). Moreover, CPS are increasingly manipulating critical infrastructure such as the power grid, transportation systems, medical devices, security systems, which means they must satisfy a whole set of challenging non-functional requirements about safety, security, privacy, usability, energy-efficiency and adaptability.
In the scope of the SYLIS CORNET project (involving the CETIC and Fraunhofer IESE Research Centres), it is important to help companies to deal with the design of such complex systems, especially from the requirements engineering phase (RE). From a RE point of view, the most adapted methods able to deal with such complexity are goal-oriented methods, such as KAOS, which is able to capture and reason about multiple agents both within the environment and the system under design of hardware/software/human natures. KAOS also enables capturing of global system properties that are achieved as a result of the global collaboration of all CPS elements. Furthermore, KAOS enables the refinement of high level system goals into specific requirements or expectations placed on each kind of agent [1].
Based on those premises, in SYLIS, we revisited a set of key requirements found in a collection of CPS systems (such as [2]) with the aim of reusing them based on the successful technique of pattern (e.g. OO design patterns, security patterns, cloud patterns). The purpose of these patterns is to capture specific knowledge related to the design of CPS systems, such as:
- Accuracy: This is a key property of CPS systems and it can only be achieved through the proper collaboration of many components. Typically, the goal of feedback loops is to maintain a specific controlled variable at some target value level. On the dynamic side there are a number of typical behaviours to control systems that are generally managed by the control designer. These control characteristics should also be made visible to the requirements analyst to unveil possible impact on system or sub-system goals: for example: how fast should a target value be reached, what is the permitted overshot (occurring on step transition), what amplitude of oscillation is acceptable, etc.
- Human interaction: different patterns are possible: humans can be in a partial control loop (which should be adapted to the individual’s reaction time); a human agent responsible for a specific requirement can be monitored by the system and their actions overridden by the system if the human fails at the duty. On the interface side, different modalities can be imagined with different kinds of ergonomics and cognitive loads.
- Cyber-security: CPS are composed of tightly interconnected elements which may be connected to the Internet either permanently or periodically. Consequently, exposing these elements to cyber threats with potentially high impact (e.g. SCADA systems controlling power grids, transportation system networks, connected cars, etc.). Reasoning based on anti-goals patterns on security threats is especially relevant to capture knowledge about how malicious agents can potentially attack a CPS, e.g. physical CPS element attack, denial of service, wrong command to controller. A number of security patterns can be enriched for the cyber-security context such as a secure controller or a secure communication channel.
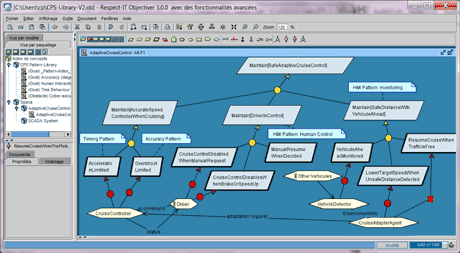
Figure 1: Structure of the CPS pattern library and instantiation to an adaptive cruise control system.
The Objectiver tool is currently used to model our CPS patterns. The tool supports the full KAOS methodology and includes support for pattern management and instantiation. Figure 1 illustrates the structure of our pattern library model (package view on the left) as well as a simple instantiation to an adaptive cruise control system including multiple agents such as a car under control, a driver, and other cars in the environment (goal diagram on the right). We plan to deploy it in a more specific tooling, already successfully applied to the smartcard domain [3], and further enrich it. We also plan to release our pattern catalogue in a tool independent collaborative knowledge oriented web-site.
Links:
http://www.objectiver.com
https://www.cetic.be/SYLIS-1934
http://cloudpatterns.org
References:
[1] A. van Lamsweerde: “Requirements Engineering - From System Goals to UML Models to Software Specifications”, Wiley, 2009.
[2] M. Heimdahl, et al.: “Modeling and Requirements on the Physical Side of Cyber-Physical Systems”, Second International Workshop on the Twin Peaks of Requirements and Architecture, San Francisco, 2013
[3] N. Devos et al.: “Efficient Reuse of Domain-Specific Test Knowledge : An Industrial Case in the Smart Card Domain”, in proc. of 34th ICSE, Zurich, June, 2012
Please contact:
Christophe Ponsard, CETIC, Belgium
E-mail:











