by Sandor Plosz, Markus Tauber and Pal Varga
A common communication language is the key element for interoperation of systems. Defining such a common language can be a formidable task, particularly in legacy and industrial systems. This problem is addressed within the Arrowhead project, which focuses on the automation of industrial systems with the goal of achieving energy efficiency and flexible use of energy.
The Arrowhead project consortium comprises 78 partners, including the Austrian Institute of Technology and AITIA International, Inc., as well as a number of manufacturers, energy providers, energy grid maintenance companies and communication system providers.
The investigated domains and use cases indicate that the integration of (legacy) sensors and M2M communication components into an automation system facilitates improved efficiency of operations.
The Arrowhead framework
An important task within the ARROWHEAD project is to design a generic framework to achieve interoperability of various sub systems, which often derive from legacy applications. The concept of this framework is based on service oriented architectures (SOA). For each system, an interface description must be provided (black box design) which can be made accessible to other systems through the core system functions. Each system may have multiple instances for different application areas, which are represented as System of Systems. System functions are derived from System of Systems Design Description (SoSDD) template. The structure of the framework is depicted in Figure 1.
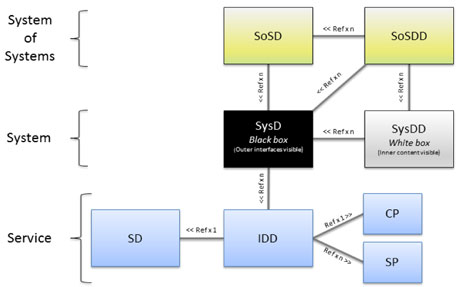
Figure 1: Structure of the Arrowhead framework.
A system may provide four core functionalities that are defined within the System of Systems Design (SoSD): Information Infrastructures, Information Assurance, System Management and Application related functionalities. These functionalities comprise services, such as service discovery, orchestration, authorization, and status, which are required to be defined for every system. Each partner involved in an individual use case publishes a list of functionalities that their (automation) system can provide and requirements for their system to accomplish particular goals that have been defined at the start of the project. Requirements may relate to dependability, safety, reliability, integrability, interoperability, architectural and communication. Based on these, the framework will be refined, and finally the procedure on how to integrate legacy systems into the arrowhead framework will be described and disseminated in project deliverables.
Information assurance
In the information assurance core system a security assessment methodology is designed which makes the security assessment of systems and applications straightforward for the developers and system designers prior to integration into the Arrowhead framework. This method is based on threat modelling [1] and risk assessment [2] techniques which can be applied from the early stages of development. Additionally, applications can make use of dependability analysis methods, where additional factors are considered for evaluation, such as socio-technical aspects, safety and reliability and maintenance support. Despite their potentially large impact on security, socio-technical aspects - such as user expectations and goals, and how users use their systems - are often neglected [3].
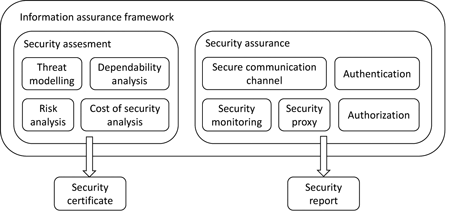
Figure 2: Arrowhead Information assurance framework.
Security requirements are outlined during application design. Important security assurance services will be developed within the information assurance core system. These include: key distribution for authentication, creating secure tunnels between systems for safe communication, certificate distribution security monitoring and security proxy for maintaining autonomy. Within the Arrowhead project we will initially collect the security requirements of different systems. Services will be developed accordingly to meet these requirements. Ways of integrating additional functionalities into the system will also be analysed and described.
An important use case for achieving energy efficiency within the inter-framework communication infrastructure is provided by cost-of-security analysis. Robust security solutions are accompanied by large processing demands in terms of speed and energy efficiency. In the security assessment methodology we address this issue by examining individual application requirements and common security assurance methods, which will enable us to suggest best methods for applications in terms of energy efficiency.
Main research question
Assuring security in the M2M communication domain requires much forward planning to make sure no interruption will be inflicted on a deployed service during operations, especially if novel IT systems are interoperating with traditional/legacy M2M components. Security assessment needs to be revisited to get the best of both the IT and M2M worlds. This planning requires the security assurance framework to be flexible, allowing security services to be updated or replaced, and new services to be installed on-the-fly. To achieve this, we need to detach security assurance from the applications themselves. This is a new approach which differs from traditional IT trends. We will address these issues as part of our work for the Arrowhead framework. This approach will enable application designers to concentrate on the task at hand without having to worry about interoperability, efficiency and security, which will be assured by well-tested systems through the Arrowhead framework.
Link: http://www.arrowhead.eu
References:
[1] M N. Johnstone:, “Threat Modelling with Stride and UML”, in proc. of the 8th Australian Information Security Management Conference, 2010
[2] P. Saripalli, B. Walters: “QUIRC: A Quantitative Impact and Risk Assessment Framework for Cloud Security”, 2010 IEEE 3rd International Conference on Cloud Computing
[3] P. Masci et al.: “Towards Automated Dependability Analysis of Dynamically Connected Systems”, International Symposium on Autonomous Decentralized Systems (ISADS) 2011
Please contact:
Sandor Plosz
AIT Austrian Institute of Technology
Tel: +3614633402
E-mail:











