by Michael Baentsch, Paolo Scotton and Thomas Gschwind
Using private workstations for business purposes – securely
In recent years, the concept of consumerization has led to consumer IT equipment that is often more powerful and easier to use than workplace computers such as notebooks. This phenomenon, coupled with the rapid generation and renewal cycle of modern ultrabooks and the administrative overhead involved in the purchase of business computers, is fueling the trend of enterprises offering their employees a contribution towards buying a private notebook for use as workplace computer. This is problematic from a security point of view: How can an enterprise ensure that privately owned computers fulfill all security requirements for accessing confidential enterprise data?
Solving the security challenge
The Secure Enterprise Desktop Team (http://www.zurich.ibm.com/secure-ed) of the IBM Research – Zurich Computer Science department believes that it has found an innovative and easy-to-use solution: By using a security token addressing questions of, for example, secure PIN entry, secure back-end connectivity and 2-factor authentication support in an easy-to-use package, namely, the IBM ZTIC (http://www.zurich.ibm.com/ztic) [1], [2] in combination with a secure bootloader and an abstraction layer (hypervisor), a complete separation of private and business-related use of a computer can be implemented: If an employee wants to access data and applications on the enterprise network via a privately-owned computer, he or she must connect the “enterpriseZTIC” to the USB port of the private computer and reboot the latter. The bootloader on the enterpriseZTIC takes control of the computer, establishes a secure connection to the enterprise server, validates the access rights of the employee, and downloads a hypervisor or control operating system. As soon as this hypervisor has been installed on the computer, a normal operating system, such as Windows 7® or Linux® can be activated. This normal operating system is provided by the enterprise and contains all security mechanisms necessary for accessing the enterprise network.
The use of the enterpriseZTIC and the secure hypervisor ensures that any malware, for example spy software such as a keyboard logger that may exist in the “private” part of the computer ie the part of the computer that is not “known” to the enterprise, becomes ineffective. This is guaranteed by booting a different operating system that does not utilize the private part of the computer and cannot be modified by any malware present therein. To guarantee fast operation of the entire system, any components of the enterprise operating system that have already been downloaded are encrypted and stored on the hard disk of the computer so that the network does not have to be accessed again to download them. As the secure hypervisor controls all access to the hard disk, the “enterprise operating system” can start up even if some components that are traditionally needed in an operating system have not yet been downloaded. This is achieved by dynamically downloading missing components only when they are requested for the first time.
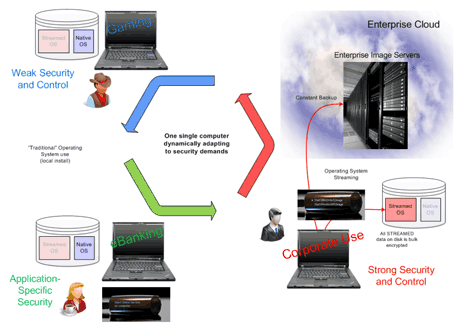
Figure 1: A single PC with different roles – and security properties – over time.
Advantages and benefits
The system described here offers a number of advantages over a classical solution, such as mere hard-disk encryption to safeguard business secrets:
First of all, private use of the computer can readily be permitted as the computer is only used for enterprise purposes in a specially secured software environment. Secondly, thanks to a suitable abstraction layer, the environment of the special “enterprise operating system” becomes very simple, as the abstraction layer will hide any hardware-specific problems by making generic device drivers available. In this way, the tasks normally performed by an IT service centre, such as selection of computers and deployment of customized operating systems, are no longer necessary. Thirdly, the constant synchronization of the hard-disk contents of the computer with the “enterprise operating system” of that particular employee as it is stored on the central server of the enterprise ensures a continual backup of all of the employee’s data.This also means that the employee can decide to use another computer, start it up with his or her “enterpriseZTIC”, immediately access the enterprise operating system and user data, and thus continue right where he or she left off. In this way, the employee is able to freely switch computers. All data stored on a particular computer are encrypted by the enterpriseZTIC and can only be decrypted and used if that particular enterpriseZTIC is plugged into the USB port of the computer.
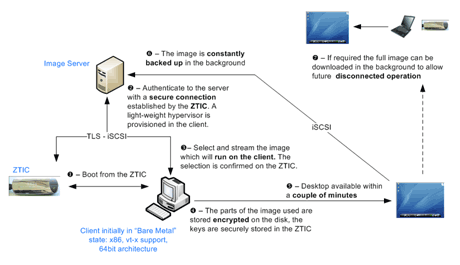
Figure 2: Overview of the entire system from start up to continual data backup and travel mode.
A further advantage of this solution is that the images of all enterprise computers are centrally stored and thus can also be centrally managed even if an employee and his or her computer are not physically on-site, ie a corporate campus.
Finally, it is also possible to use this solution in a “travel” mode. To do so, the employee informs the system that he or she wants to start using it without network connection. In this case, all data not yet available locally, ie on the computer, will be downloaded, encrypted and stored. As soon as the system reconnects to the network after offline use, any changes made during offline use will be transmitted back to the server.
Outlook
A special development focus is on solving the challenges involved when computers of one enterprise are used to execute the specifically configured operating system of another enterprise. This situation can arise if third-party employees (external consultants for instance) have to comply with desktop security requirements of the enterprise at which they are temporarily working.
Current state & next steps
The solution described herein is currently deployed as internal pilot, and the development team is actively searching suitable first users outside of IBM.
Links:
http://www.zurich.ibm.com/secure-ed
http://www.zurich.ibm.com/ztic
References:
[1] T. Weigold, et.al.: The Zurich Trusted Information Channel – An Efficient Defence against Man-in-the-Middle and Malicious Software Attacks; In P. Lipp, A.-R. Sadeghi, and K.-M. Koch (Eds.): TRUST 2008, LNCS 4968, pp. 75–91, 2008. © Springer-Verlag Berlin Heidelberg 2008.
[2] M. Baentsch, et.al.: A Banking Server's Display on your Key Chain; ERCIM News 73, 2008; http://ercim-news.ercim.eu/a-banking-servers-display-on-your-key-chain
Please contact:
Michael Baentsch
IBM Research Zurich
Tel: +41 44 724 8620
E-mail:










