by Daniel Plohmann and Elmar Gerhards-Padilla
Malware is responsible for massive economic damage. Being the preferred tool for digital crime, botnets are becoming increasingly sophisticated, using more and more resilient, distributed infrastructures based on peer-to-peer (P2P) protocols. On the other side, current investigation techniques for malware and botnets on a technical level are time-consuming and highly complex. Fraunhofer FKIE is addressing this problem, researching new ways of intelligent process automation and information management for malware analysis in order to minimize the time needed to investigate these threats.
The development and use of malicious software has gained remarkable professionalism in recent years and its impact has drastically expanded. Financially-oriented digital crime operations offer high reward with a low risk of getting caught. Additionally, malware offers huge opportunities in terms of espionage when reviewing the recent incidents of targeted attacks. While attacks are easily carried out through available services and ready-to-go crimeware construction kits, on the defensive side, a thorough analysis of malware can only be conducted by experienced specialists, introducing a strong asymmetry.
The main reason for this is that on the technical side, binary code is the main subject of analysis when in-depth knowledge about malware and botnets is desired. In the analysis process, reverse engineering is the principal technique for granular inspection of functionality and derivation of possible countermeasures. The usual approach is divided into the following stages:
- A blackbox runtime analysis is performed to gain a first impression of the malware's behaviour.
- Static analysis (no code execution) is applied to the binary to achieve a general structural overview and to identify relevant functional parts.
- Dynamic analysis is performed on these selected parts to extract runtime information that supports static analysis.
- All stages are supported by Open-Source Intelligence (OSINT) methods to link the intermediary technical findings with traces of the malicious operation that are accessible or archived on the Internet.
While the first stage is easily automated through sandboxes, the later stages are mostly performed manually by humans. Reasons for this are protection mechanisms of malware samples, such as anti-reverse engineering techniques and polymorphic representation of semantically-equivalent code. A range of powerful tools cover aspects of the analysis process but they are often neither inter-operable nor suited for immediate collaboration in a team of operators. Furthermore, effective analysis often requires the malware to communicate to its Command & Control (C&C) entity.
Our approach aims at the creation of an analysis environment that bridges the aforementioned gaps. On the one hand we are designing a prototype for an intermediate platform compatible with various tools that allows organization and provision of knowledge extracted from malware samples. On the other hand, we have developed a server component that allows emulation of arbitrary connection endpoints, thus supporting the rapid analysis and adaption of custom communication protocols that is often used by malware.
We have applied parts of the developed process as a test case to investigate the Miner Botnet. This botnet received public attention after starting an extensive Distributed Denial of Service (DDoS) campaign against a range of about 500 German websites, accompanied with attempted extortion for Bitcoins, a virtual currency. The name of the botnet originates from its capability of “Bitcoin Mining”, which is the term used to describe the generation of Bitcoins.
We applied reverse engineering to the set of malicious executables obtained from an initial infection. This allowed us to infer the modular structure of the malware and to extract information about the C&C architecture and derive a specification for the protocol it uses. On these grounds, we created a tracking software for the botnet, iteratively enumerating all active hosts in the P2P layer of C&C architecture.
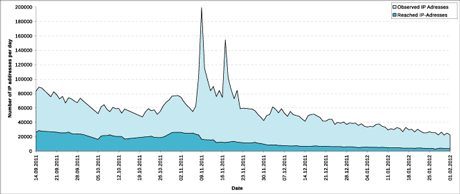
Figure 1: Results of our hourly monitoring efforts.
As an example of findings, Figure 1 shows the results of our hourly monitoring efforts for the period 14 September, 2011 to 1 February, 2012. The figure shows IP addresses that we observed in the circulating address lists and infected hosts we were actually able to reach. The two eye-catching spikes in the observed addresses result from reconfiguration of the botnet by its botmaster, which is not reflected in the actual population. On 1 December, 2011, the last binary update was published to the bots, causing a constantly decreasing trend in the size of the population thereafter. This can be interpreted as the direct natural consequence of the lack of active management of the botnet.
The full results of our investigation of the Miner Botnet were presented in June 2012 at the 4th International Conference on Cyber Conflict (CyCon) in Tallinn, Estonia.
Link:
http://www.fkie.fraunhofer.de/en/research-areas/cyber-defense.html
References:
D. Plohmann, E. Gerhards-Padilla. “Case Study of the Miner Botnet” in Proc. of the 4th International Conference on Cyber Conflict, Tallinn, Estonia, June 2012.
D. Plohmann, E. Gerhards-Padilla, F. Leder, "Botnets: Detection, Measurement, Disinfection & Defence", Technical Report published by the European Network and Information Security Agency (ENISA). Editor: Giles Hogben. Heraklion, Greece, March 2011.
Please contact:
Daniel Plohmann, Elmar Gerhards-Padilla,
Fraunhofer Institute for Communication, Information Processing and Ergonomics FKIE, Germany
E-mail:










