‘Cloud computing environments have become a new battlefield for cyber crime’ [3], posing an unprecedented risk to individuals’ privacy. A survey with 257 respondents on Cloud forensic capabilities and perceived challenges shows the state of Cloud forensics.
Cloud computing is radically changing the way information technology services are created, delivered, accessed and managed, as well as the corresponding business models. Keeping pace with the continuous adoption of Cloud computing, a rapidly increasing amount of data is being transferred to and processed by clouds. Trusting massive quantities of data processing to third parties raises security and privacy concerns, which – despite existing mechanisms – turn out to be the main inhibitor for Cloud adoption.
If available, forensic techniques could be used to provide accountability and hence re-establish trust. A representative survey conducted by researchers [3] captured the current state of “Cloud forensics”, ie the application of digital forensics in Cloud computing environments. The survey is a primer in this research field. It received 257 responses worldwide, from academics, practitioners, service providers and industry. The top challenges for Cloud forensics are depicted in Figure 1. The complete survey is under review at Elsevier’s Digital Investigation; a preliminary status can be found in [2].
The background part of the survey regards the definitions of and expectations of Clouds. The majority of the respondents (62%) agree that the Cloud is not a new technology but a novel means of delivering computing resources. This does not imply that all the technical means needed to provide reliable Cloud is at hand: in fact 70% of the respondents disagree with this. Over 49% of participants believe that Cloud computing reduces cost and compromises security. Some argue that the rapid growth of Cloud computing is driven by cost reduction with known risk and sacrifice of security. This popular argument among early-adopters is only partly supported by the respondents of this question, but backed in other surveys carried out in the US and Europe, where up to 70% of the participants are concerned with security.
The survey highlights the importance of forensic techniques tailored to the Cloud: 81% of respondents agree that forensics is an indispensible component of Cloud security, while 76% claim that this area needs more funding and investment than it currently receives. Interestingly, 71% of respondents believe that the general lack of awareness of Cloud security will endure until a major critical incident happens. This could explain the aforementioned fact that security concerns are not levelled as “critical” by respondents. The results of this question show that the respondents have reached consensus on the significance of Cloud forensics. However, leading organizations driving Cloud security standards still largely neglect the importance of integrating forensic capabilities into Cloud security in their most recent releases.
Up to 41% of participants believe that Cloud forensics is a “brand new area” and only 25% agree that Cloud forensics “is” classical computer forensics”. Up to 46% of the participants believe that Cloud computing makes forensics harder. The reasons are manifold, including reduced access the physical infrastructure and storage (26%), lack of standard interfaces (15%) and evidence segregation (12%). Among the 37% believing that Cloud makes forensics easier, 17% state that evidence is harder to destroy as a result of mirroring, 15% consider that forensic functionalities can be integrated into Clouds and 10% believe that there will be less work for the investigator/law enforcement side because the data are centralized on the provider.
Regarding the focus of Cloud forensics, 56% of respondents regard it as an interdisciplinary effort, in contrast to 44% believing it to be purely technical. 80% of respondents agree that there is a “technical” as well as “legal” dimension for Cloud forensics; 14% of respondents clicked “other” dimensions. “Political” and “personal” dimensions are mentioned in the comments. There was a consensus among respondents that Cloud forensics comprises three major dimensions: technical, organizational and legal.
As for forensics usage, 80% of respondents agree that Cloud forensics can be used for “investigations on digital crimes, civil cases, policy violations, etc.”, 51% agree that it can be used for "regulatory compliance", 46% agree it can be used for “data and system recovery”, 40% agree that it can be used for “due diligence” and 34% agree that it can be used for “log monitoring”. Since Cloud forensics is an application of digital forensics in Cloud computing, its usage should be similar to the usage of digital forensics in general. When applied in Cloud computing environments, the split of control among Cloud actors has made forensics a shared responsibility which adds to the organizational complexity of Cloud forensics.
Taking stock, the survey results show that Cloud adoption does pose significant novel challenges to digital investigation, rather than scaling up existing problems. In fact, there is to-date a lack of mechanisms to address forensic investigations in the Cloud [1,2], as well as solid jurisdiction on handling Cloud-related cases [2]. This gives incentives to defectors exercising cybercrime. Researchers strongly believe that it is a critical timing for standard acceleration and enhancing forensic capabilities while the technology matures.
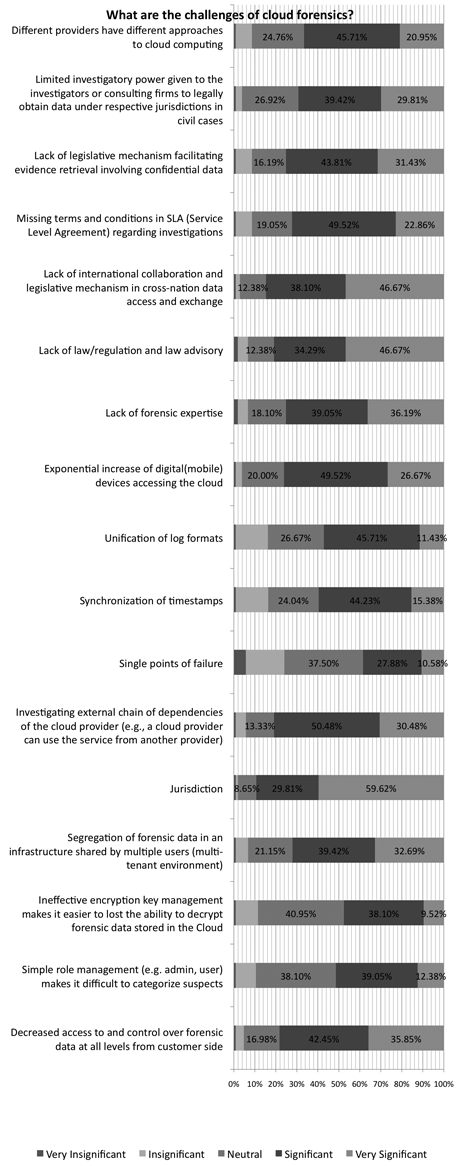
Table 1: Challenges of cloud forensics
Links:
BPSec Group: http://bpsec.telematik.uni-freiburg.de/
Cloud Forensics Research: http://www.cloudforensicsresearch.org/
References:
[1] Accorsi, R.; Wonnemann, C. (2011): Forensic leak detection for business process models. Advances in Digital Forensics VII, pages 101-113. Springer.
[2] Ruan, K.; Carthy, J.; Kechadi, T.; Crosbie, M. (2011): Cloud forensics. Advances in Digital Forensics VII, pages 35-46. Springer.
[3] Ruan, K.; Baggili, I.; Carthy, J.; Kechadi, T. (2011): Survey on cloud forensics and critical criteria for cloud forensic capability: A preliminary analysis. ADFSL Conference on Digital Forensics, Security and Law.
Please contact:
Rafael Accorsi
University of Freiburg, Germany
E-mail:
Keyun Ruan
Centre for Cybersecurity and Cybercrime Investigation
University College Dublin, Ireland
E-mail:









