by Jocelyn Aubert, Christophe Incoul and Djamel Khadraoui
In today’s world, where most critical infrastructures are based on distributed and interdependent systems, security failures have become very common, even within large corporations. The FP7 MICIE (Tool for systemic risk analysis and secure mediation of data exchanged across linked CI information infrastructures) project aims to design and implement an alerting system that identifies, in real time, the level of possible threats induced on a given critical infrastructure (CI) by ‘undesired’ events occurring in the CI and/or other interdependent CIs. Here, we briefly describe the approach of a real-time risk-based monitoring solution for interdependent services of CIs.
Current risk analysis methods do not provide a way to share risk knowledge between providers who together form a CI. Providers have expertise on risks to their own infrastructure, but not on those to related infrastructures of other providers. In most cases, this knowledge cannot be shared between providers for confidentiality reasons. The idea of the approach developed by The Public Research Centre Henri Tudor, in the MICIE project, is to limit the exchange of data between CIs to the status of the security properties related to shared services. Confidential pieces of information about the CI (infrastructure, tools, equipment) are not exchanged. To reach these goals, we have developed a risk-based methodology that will monitor interdependent services based on generic risk and assurance levels using the classical security properties: confidentiality, integrity and availability. This allows each CI owner to monitor, react to and adopt the best behaviour corresponding to the security status of its different services.
A three steps methodology
The methodology allows a realistic representation of the security properties of interdependent systems. Using security properties to abstract the physical implementation will allow a wider range of systems to be addressed since the security objectives are the same for all systems. The security properties of an interdependent system are defined by the attributes confidentiality, integrity and availability. As illustrated in Figure 1, this methodology is composed of three steps: the security model step, the measurement and aggregation step and the monitoring step. These three steps are described below.
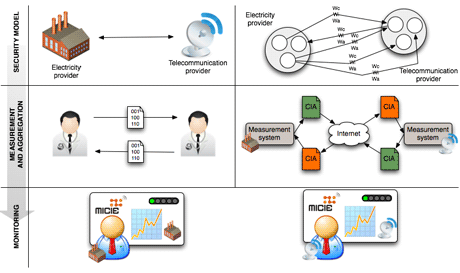
Figure 1: IT security risk-based prediction methodology for CI. (Some icons in Figure 1 were desgined by DaPino Colada and were extracted from www.iconfinder.net under CC NY 3.0 license.)
Security model
The whole methodology is based on an efficient and realistic modelling of the infrastructure paired with a global estimation of the dependencies between services. This service-oriented modelling aims to identify and represent all the critical services within the infrastructure as their links on external services in terms of confidentiality, integrity and availability. Using this model, the infrastructure will be able to define a generic level of risk and assurance of the different services that will be exchanged among interdependent CIs. Modelling relies on a reductionistic representation of the services, combining a functional model that defines and balances in terms of importance the relations between each critical service, with the results of a risk analysis made on each CI that aims to identify the main critical services. The reasoning based on the security model is only possible if all the CIs share a common representation of assurance and risk levels; for this, generic scales for both assurance and risk levels were defined.
Measurement and aggregation
Using the security model, the developed system is able to continually perform measurements on the various components composing monitored services. The results of such measurements are normalized and aggregated in the form of risk levels for each of the considered security attributes. Normalization and aggregation are realized thanks to advanced algorithms.
Monitoring
Using the security model, each CI sends local computed risk levels to each of the services depending on it. A service that receives a risk level can compute a risk linked to its dependencies, and thus update its global risk level by combining its own local data with the data provided by services on which it depends. This consolidated information enables the CI operator to integrate risks induced by remote services on the global CI risk estimation. Doing so, the operator is able to identify and to act and prevent security incidents from propagating in the interdependent critical services.
Experimentation
The methodology is the subject of experiments. An application prototype has been developed and is based on a multi-agent system, in charge of collecting, normalizing and aggregating all the considered measures using advanced algorithms. These measures are then combined in order to provide each CI owner with consistent consolidated information on the current level of risk.
The first results show that such an approach can provide a more comprehensive view of CIs and their interdependencies. However, enhancements could still be considered, as for example a definition of dynamic interdependency weights, to provide flexibility according to the current situation.
Links:
http://www.micie.eu
http://citi.tudor.lu
Please contact:
Djamel Khadraoui
CRP Henri Tudor, Luxembourg
Tel: +352 42 59 91 1
E-mail:










