by Pau Giner, Carlos Cetina, Joan Fons and Vicente Pelechano
The Internet of Things envisions real-world environments that are augmented with digital services. With ever greater numbers of devices being added to our surroundings, simplicity is greatly appreciated by users. With the purpose of preventing service behaviour from becoming overwhelming, our project is devoted to dynamically organizing services according to user needs.
Imagine a future in which your fridge announces to you the recipes that can be prepared with the available goods, your TV tells you that your favourite program is beginning, the book you want to start reading is suggesting you try other similar books; and all of this is happening at the same time. Clearly living in such an environment on a daily basis would be annoying. On the other hand, if services behave in a completely automatic manner (without requiring human input), users can feel that their environment is out of their control, which is also undesirable.
Since user attention is a valuable but limited resource, we believe that an environment full of embedded services must behave in a considerate manner, demanding user attention only when it is required. In the same way that a musical orchestra requires a conductor to indicate who should play and the tempo to be followed, we propose to incorporate orchestration techniques in Internet-of-Things (IoT) environments, in order to achieve a balance between automation and user participation.
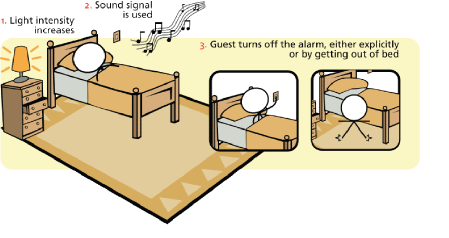
Our project consists in a method for building IoT environments that are automatically reorganized in order to offer the degree of obtrusiveness required by the user. For example, several devices could be gradually used in order to make the experience of waking up less shocking (see Figure 1). We make use of model-based techniques to face the development of such systems from a technology-independent perspective. The method comprises the following steps:
1. Business process modelling. The activities in which the users are involved and their temporal dependencies are captured by means of business process modelling techniques. In particular, we use Business Process Modelling Notation (BPMN), a graphical notation standardized by the Object Management Group (OMG), since it is well understood by business analysts and provides facilities for deriving executable solutions from the BPMN models.
2. Implicit interaction design. Each task is analysed to determine the level of obtrusiveness it requires. In particular we are focusing on two factors that affect the design of implicit interactions: initiative and attention. Initiative defines whether the service is activated automatically or by the user. The attention factor relates to the users awareness of a service, defining whether the service performs in the foreground or the background of user attention. Table 1 illustrates the requirements for the various tasks involved in the example process of waking a hotel guest.
|
Obtrusiveness
|
||
| Task |
Initiative
|
Awareness
|
| Wake up | Proactive. The system triggers the activation of the mechanisms for waking the user. | Increasingly from background to foreground. The goal is to make the user aware in a gradual manner (using lights first, then sound). |
| Turn the alarm offTurn the alarm off | Proactive. The user can decide to turn off the alarm, either because he/she decides to get up or because he/she consciously decides to continue sleeping. | Foreground. The deactivation of the alarm is something that should be consciously done by the user. |
| Get out of the bed | Reactive. The user activates the sensors that detect that he/she is getting out of bed. Alarm is turned off as a consequence. | Background. Sensor activation is not intended to be conscious for the user. |
3. Deployment in an orchestration engine. Business process execution technologies have proven successful when applied to coordinating networked services, especially in Service-Oriented Architectures (SOAs). We have extended these technologies, which have already been applied in the traditional Internet, and applied them to the Internet of Things. In particular, we have developed middleware for integrating automatic identification technologies such as RFID or QR codes with business process execution engines based on WS-BPEL (Web Services Business Process Execution Language).
4. System reconfiguration. A model-based reconfiguration engine is used to automatically adjust the system architecture to the requirements presented as models. To achieve this, the system architecture is based on components and communication channels that can be dynamically established among them for achieving a particular behaviour. In this way, a service can transit from silent behaviour to behaviour that is noticeable by the user as a reaction to the business process evolution.
This work is part of a four-year research project at the ProS research centre, which is devoted to the development of new methods for the production of software in different areas. The techniques presented here have been successfully applied to scale environments with real technology in our research lab, with the measurement of acceptance by real users being the next step in our research.
Link:
http://www.pros.upv.es
Please contact:
Vicente Pelechano
Universidad Politécnica de Valencia/SpaRCIM, Spain
E-mail: pele![]() pros.upv.es
pros.upv.es










