by Marek Klonowski, Michał Koza and Mirosław Kutyłowski
Recent work carried out at Wroclaw University of Technology shows that a fair level of security can be achieved for wireless sensor networks without heavy cryptographic technology.
Wireless sensor networks processing sensitive data are facing the risks of data manipulation, data fraud and sensor destruction or replacement. This concerns applications such as the gathering of data on environmental pollution around industrial installations, or sensor systems replacing traditional video monitoring. Large-scale deployment in practice is conditioned by solving these kinds of security problem and reducing the risks due to limited physical protection of the devices and openness of the wireless communication channel. While modern cryptography and computer security offer many ways of solving these problems, they are focused on solutions for high-performance devices, and not for computationally weak sensors with limited communication bandwidth. New 'lightweight' solutions tailored for the special needs of wireless sensor networks have to be designed. This is one of the focal points of the EU project FRONTS (Foundations of Adaptive Networked Societies of Tiny Artefacts). Fortunately, some recent developments have shown that without heavy cryptographic technology it is still possible to achieve a fair level of security in a practical sense. This report indicates a few ideas of this kind.
Due to the energy required for transmission over long distances, it is often a good idea to route data along a sensor network by making many hops over small distances instead of a direct transmission from a sensor to the sink node. However, such a solution has the disadvantage that an adversary can attack the network by gaining control over intermediate sensor nodes. The cryptography used by such devices is usually weak and can provide opportunities to reveal information sent or to manipulate them.
The following idea may be applied in order to make it much more difficult to carry out attacks. Instead of a single information path, each message is sent over a double path. This means that instead of a single ith node Ni we have two nodes: Pi and Ri. The encryption scheme has the following basic properties when processing a message M:
- Pi+1 receives encrypted messages from Pi and Ri in order to compute its share of message M,
- Ri+1 receives different encrypted messages from Pi and Ri in order to compute its share of M.
The encryption scheme guarantees that corrupting either Pi or Ri reveals no information about M. Also, combining the shares from different stages of message processing gives no information about M as long as the adversary has only one share from each level of the path.
What is the advantage of such a design? The main point is that while it might be relatively easy to find and corrupt one of the nodes (say Pi ) for this to be useful, the adversary must still find and corrupt the matching node Ri. This can be difficult for purely practical reasons: if each sensor is hidden in the environment, then while the first might be found by chance, the second must be found by a detailed search in the same area. This could be hard without arousing the interest of observers.
Moreover, we propose a far more sophisticated design in which on each level of routing there are many potential sensors to play the roles of Pi and Ri. In this case the adversary usually has to collect and corrupt many sensors until the matching pair is found.
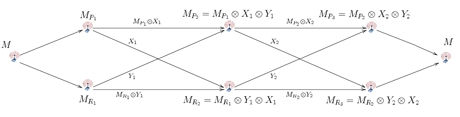
Another step of the design is to make the path self-evolving: at any time a node may negotiate with its predecessors and successors a change of the transmission key and redirect its duties to another node. Since these changes can be made independently and uniformly at random, the data path may evolve so fast as to make unfeasible any attempt at data analysis based on monitoring radio traffic. Indeed, a cryptanalytic attack would face the difficulty that assigning the messages to sensor-to-sensor links (and to the pairwise keys) would be hard, due to the number of possibilities growing extremely fast as the number of links increases.
The architecture described here is currently being analysed from the point of view of hiding the transmission routes in the case of heavy traffic, under the assumption that an adversary can select the traffic coming out of each node. This involves studies concerning combinatorial issues of traffic analysis as well as stochastic investigations of the rapid mixing of Markov chains. Further details of the scheme will be developed in cooperation with other partners of the project; in particular, we plan to develop a prototype of the system.
Link:
FRONTS: http://fronts.cti.gr/
Please contact:
Mirosław Kutyłowski
Wrocław University of Technology, Poland
Tel: +48 71 320 21 09
E-mail: miroslaw.kutylowski![]() pwr.wroc.pl
pwr.wroc.pl










