by Dave Raggett (W3C/ERCIM) and Theodoros Rokkas, (inCITES)
The electrical power and energy system (EPES) is a critical infrastructure for society, and as such, an attractive target for cyber attackers. The SDN-microSENSE project has demonstrated robust, resilient, distributed cyber-defence capabilities, including the use of software defined networks (SDN) for self-healing, isolation and integration of honeypots to minimise disruptions. Many of the techniques are applicable to other sectors.
SDN-microSENSE [L1] aims to provide and demonstrate a secure, resilient to cyber-attacks, privacy-enabled, and protected against data breaches solution for decentralised EPES. The project partners have built a complete framework for the detection and mitigation of cyber-attacks using various communication pathways that interconnect all commonly used tools in EPES infrastructures with new detection and analysis tools. A web-based desktop environment is integrated to provide easy-to-use overview and management. The architecture focuses on the power-grid (electrical infrastructure) and the data network that is associated with the infrastructure.
SDN-microSENSE architecture with functional blocks and interfaces
The project’s objectives are as follows:
- To design and provide a new resilient, multi-layered and SDN-enabled microgrid architecture, which will leverage the global system visibility for preventing and addressing disruptions to the underlying supervisory control and data acquisition (SCADA) and industrial control systems (ICS) infrastructure.
- To design and develop a risk assessment and management framework.
- To develop and implement applications which exploit direct networking controllability and programmability offered by SDN to investigate multiple security applications, including self-healing attack-resilient phasor measurement units (PMU) and remote terminal units (RTU), for going toward achieving resilient and secure operations in the face of various cyberthreats and failures.
- Deliver an energy trading platform for secure and flexible trading management.
- To provide a robust, distributed and effective IT cyber-defence system for large-scale EPES ecosystem.
- To design and deploy an anonymous channel of EPES which will allow secure and privacy-preserving information sharing among energy operators and actors.
- To deliver a privacy-preserving framework for enhancing EPES against data breaches.
- To design and develop and a policy recommendation framework based on the SDN-microSENSE results, lessons learnt and best practices for formulating recommendations for standardisation and certification.
- To design and demonstrate large-scale pilots across Europe.
These objectives have been pursued through the following pilots:
- Pilot 1 addresses attacks relating to communication between the SCADA servers and applications, attacks related to substation bus communication, and attacks related to process bus communication.
- Pilot 2 addresses false data injection attacks against Phasor Measurement Units (PMU) and Phasor Data Concentrators (PDC), and man in the middle attacks on smart meters and inverters for photovoltaic arrays.
- Pilot 3 addresses mitigation actions including islanding and grid restoration. Islanding is a means to isolate part of the EPES infrastructure from the rest of the grid.
- Pilot 4 addresses identity fraud, denial of service and command attacks, validation of islanding mechanisms, attacks on photovoltaic plant inverters, and mitigation through reconfiguration.
- Pilot 5 addresses detection and mitigation of denial-of-service attacks on Modbus and man in the middle attacks, e.g., ARP poisoning, along with photovoltaic park isolation and energy balancing against distributed denial of service attacks.
- Pilot 6 addresses data privacy breaches against smart metering infrastructure, along with handling attacks on a Blockchain based framework for energy trading transactions.
Attackers will try to find weaknesses at all layers in the EPES infrastructure. Strong security needs to be based on thorough threat modelling [L2], including threats to popular EPES protocols [L3], real-time monitoring of anomalous behaviour, threat assessment and speedy decisions on counter measures for mitigation. This involves security information and event management (SIEM) [L4] in conjunction with the security and risk assessment framework (S-RAF). Intelligence gained from attacks needs to be reported, and used to further strengthen security throughout the EPES.
The SDN-microSENSE architecture [L5] is composed of three main layers: (a) Intrusion Detection and Correlation, (b) Dynamic Risk assessment, and (c) Self-Healing. The first tier is responsible for evaluating dynamically the risk level of each Smart Grid asset. The first layer is responsible for detecting and correlating security events. Next, the second layer undertakes to re-evaluate the severity of each smart grid asset in a dynamic manner. Finally, the last layer executes mitigation actions, ensuring the normal operation of electrical and power energy systems. All the layers of the SDN-microSENSE architecture communicate with the SDN controller either for detecting or mitigating potential threats.
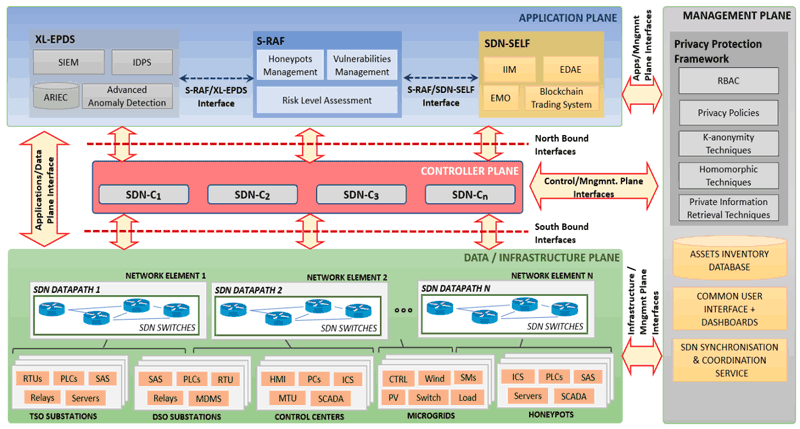
SDN-microSENSE architecture with functional blocks and interfaces.
A machine learning-based tool (L-ADS) is used for monitoring network traffic to detect anomalous behaviour. High speed event logging is used to feed the S-RAF. SDN is used to isolate malicious network traffic, and to direct it to honeypots as a means to gather further information about the attacker. Mitigation decisions are made using a rule-based framework managed through the SDN dashboard that allows the restoration of critical parts of both the power grid and data network infrastructure.
SDN-microSENSE has demonstrated the potential for applying a variety of techniques to improve the resilience of EPES against cyberattacks. Many of these techniques are applicable to other sectors, as a basis for system and security administrators to identify security gaps as well as to detect and prevent possible cyber threats.
This project has received funding from the European Union’s Horizon 2020 research and innovation programme under grant agreement No 833955.
Links:
[L1] The public website for SDN-microSENSE: https://www.sdnmicrosense.eu/
[L2] SDN-microSENSE deliverable D3.5 Risk assessment framework: https://www.sdnmicrosense.eu/wp-content/uploads/2021/09/D3.5_Risk-Assessment-Framework.pdf
[L3] SDN-microSENSE deliverable D5.2 SS-IDPS System: https://www.sdnmicrosense.eu/wp-content/uploads/2021/09/D5.2_SS-IDPS-System.pdf
[L4] SDN-microSENSE deliverable D5.1 XL-SIEM System: https://www.sdnmicrosense.eu/wp-content/uploads/2021/09/D5.1_XL-SIEM-System.pdf
[L5] SDN-based resilient smart grid: the SDN-microSENSE architecture: https://www.mdpi.com/2673-6470/1/4/13
[L6] SDN-microSENSE deliverable D3.3 EPES Honeypots: https://www.sdnmicrosense.eu/wp-content/uploads/2021/09/D3.3_EPES-Honeypots.pdf
Please contact:
Dave Raggett, W3C/ERCIM, France
Theodoros Rokkas, inCITES










