by Peter Kieseberg (St. Pölten UAS), Michael Herburger (UAS Upper Austria) and Alexandra Anderluh (St. Pölten UAS)
Supply chains can be considered the backbone of modern industry. Although supply chains may be highly integrated, security practices are often focussed around single companies and do not incorporate issues that arise from the integration of other partners within the chain. Thus, to make supply chains resilient against cyber-attacks, we need to adopt a holistic view of supply chain security.
Networked, highly integrated supply chains (SC) are an essential characteristic of modern business. Complex supply chains can already be found behind relatively simple-seeming products, owing largely to the increasing specialisation of companies. In addition, complexity has significantly increased in recent years due to three trends: (i) the trend towards customised products, such as in the automotive industry, where a car can only be completed after an order has been placed, based on individual wishes; (ii) the trend towards just-in-time production (JIT) and lean management in order to keep storage costs low; and (iii) globalisation, resulting in worldwide branched SCs.
These trends have led to a massive increase in time pressure, even in non-critical industries. Redundancies have been reduced as far as possible, and accordingly supply chains must function as smoothly as possible to avoid incurring considerable losses, e.g. due to waiting times and idle machines. The vulnerability of SCs and entire industries has been demonstrated not only by the disruptions caused by the COVID-19 pandemic, but also during the recent blocking of the Suez Canal [L1].
Different degrees of integration exist in SCs, depending on the size and structure of the partners involved, and the level of collaboration. Among equal partners, or within very open structures with many different customers, often no dedicated integrated SC-platforms are created. This can lead to very low levels of organisation, which are correspondingly susceptible to social engineering techniques [1], but also to a proliferation of different tools, which are correspondingly difficult to maintain. This can easily lead to attacks on partners, e.g. by changing payment modalities, or by stealing know-how or tender and bid documents. Such information is often used merely to obtain information for subsequent social engineering.
Large companies, having recognised the problems of low-integration SCs, have integrated their suppliers into their backbone systems and require them to perform any communication and information exchange within this platform (see Figure 1). This integration is particularly important in terms of cyber security: while large enterprises spend vast sums of money to make their IT and OT (operations technology) systems secure, many of their specialised suppliers are SMEs, often competing in a very aggressive market and therefore unable to focus on IT security issues. Due to the deep integration of their systems with the big players' platforms, they provide a perfect vector to attack large enterprises, enforcing several different attack strategies: (i) the attacker might try to leverage a vendor's corrupted system to attack the platform; (ii) vendors can often access a variety of information from the platform, so information exfiltration may be an issue; and (iii) it can be used as a means of reconnaissance to launch other forms of attack, such as social engineering. Finally, (iv) the corrupted system could be used to inflict damage by disrupting the SC through attacks such as Denial of Service (DOS), command manipulation, or other acts of vandalism.
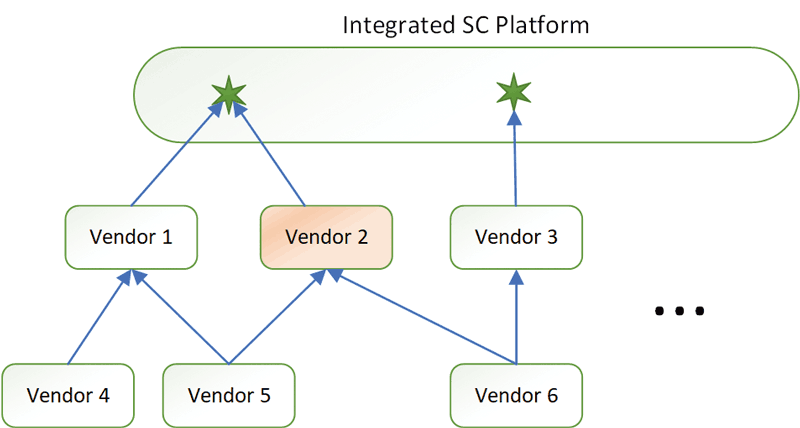
Figure 1: Schematic of highly integrated SCs.
Securing SCs against cyber risks is not a new idea [2]. Nevertheless, essential aspects have so far only been researched in a rudimentary way and dealt with on an academic level:
- Holistic analysis of attacks and attack targets: Currently available literature on securing SCs essentially focuses on specific use cases and application areas, typically looking at only a small section of an SC, usually one or two companies. In addition, security literature typically focusses on single entities (companies) and do not consider the SC [3].
- SCs with different degrees of organisation: SCs differ significantly in their degree of integration, which must be taken into account accordingly in the security architecture and in the choice of countermeasures.
- Real-world use cases: Most of the literature does not focus on model cases, which are useful for developing and demonstrating specific technologies, but make it very difficult to translate the lessons learned into reality.
- Situational awareness for SCs: Situational awareness is currently typically associated with governments and related agencies, though many large companies also use similar technologies. The aim is to continuously monitor all entities in a system, regardless of whether they are technical assets or resources. However, classical security approaches are not suitable for SCs, as the focus is currently put mainly on relatively static computer networks, which means that the strong dynamics in complex adaptive systems such as SCs cannot be considered accordingly.
Within the SSCCS project [L2], methods for solving these challenges will be researched, with the general aim of defining problems as close to real life as possible, i.e. the problems to be solved are defined from real use cases. For this purpose, the project consortium can draw on a great deal of comprehensive know-how from many areas of supply chain management and logistics, especially in the field of multimodal logistics. From an academic point of view, the targeted research results are not only interesting from the point of view of SCM and logistics, as well as IT security, but also relevant to the topic of resilience, a theme that has moved into the focus of research, and also of relevant societal and governmental actors.
Links:
[L1] https://edition.cnn.com/2021/03/24/middleeast/suez-canal-container-ship-intl-hnk/index.html
[L2] https://projekte.ffg.at/projekt/3984614
References:
[1] S. Nasralla, A. Croft, Adrian: “Austria’s FACC, hit by cyber fraud, fires CEO”, 2016. Reuters. URL:https://www.reuters.com/article/us-facc-ceo-idUSKCN0YG0ZF
[2] V. Hassija, et al.: “A survey on supply chain security: Application areas, security threats, and solution architectures”, IEEE Internet of Things Journal, 8 (8), 6222-6246, 2021
[3] C. Colicchia, A. Creazza, D. A. Menachof: “Managing cyber and information risks in supply chains: insights from an exploratory analysis”, Supply Chain Management: An International Journal, 24(2), 215-240, 2019.
Please contact:
Peter Kieseberg
St. Pölten UAS, Austria
Michael Herburger
Steyr UAS, Austria










