by Thomas Lorünser (AIT Austrian Institute of Technology) Eva Munoz and (ETRA Investigación y Desarrollo) and Marco Decandia Brocca (Lombardia Informatica)
Distributing trust among many different players is a common approach in security. In the case of storage, many protocols are known for secure fragmentation of data, however, relatively little research has addressed the aspects relevant for real deployment in cloud based systems, i.e., how to satisfy the underlying trust assumption.
In this work we report findings encountered during the design and deployment of multi-cloud storage solutions based on secure fragmentation (secret sharing) and solutions developed within the project PRISMACLOUD [1]. It was interesting to see that major inhibitors for adoption were not the technical barriers, but human factors.
Nowadays cloud storage can be considered a commodity product. Thanks to de-facto industry standards like S3 (Amazon Simple Storage Interface) and SWIFT (Open Stack Storage) provider lock-in is no longer a problem and a prosperous market is developing. Although the cloud storage service level agreement (SLA) offered by cloud service providers (CSP) differ in many details, consumers already have access to a large and diverse cloud storage market which opens up many new opportunities for IT operators, from small to large enterprises. The natural next step would be to combine the offerings into intercloud and multi-cloud settings to gain in flexibility, availability, confidentiality as well as price. However, adoption of fragmented multi-cloud storage has not yet taken off, and we have identified two main reasons for this. Firstly, the cloud storage market is still very dynamic and no comprehensive archive exists to enable people to compare offerings. Secondly, almost all IT professionals interviewed felt overwhelmed with the many configuration options possible. The selection of suitable choices for configuration parameters combined with the selection of non-colluding sets of providers turned out to be too complex and time consuming for administrators.
These findings led us to an in-depth analysis of the decision process for the configuration of secure and cost efficient multi-cloud storage systems on the basis of Archistar [2] technology. It was important to understand how cloud customers rate the trustworthiness of providers and their likelihood to collude. It was also important to consider legal aspects, i.e., especially requirements given by the general data protection regulation (GDPR), which basically require that all personal data reside in EU or countries which provide the same level of protection. Additionally, business needs had to be considered which require strongest protection for critical assets even beyond compliance requirements.
One important feedback from industry was that the non-collusion assumption would be specifically appealing in semi-trusted environments. By semi-trusted environments we mean infrastructure pooled by communities who are following the same practices and standards, and who also trust each other to a high level, however, they would still not entrust company data to be stored in plaintext on peer server. This is typically the case for public authorities or governmental organisations sharing some common communication infrastructure but still maintaining their own data centres and wanting to maintain control over their data.
Based on this result we’ve developed two interesting use cases and demonstrators leveraging secure multi-cloud storage and data sharing in a community setting. Lombardia Informatica S.p.A. developed an eGovernment pilot for secure cloud based backup and archiving where data can be flexibly dispersed over a data centre of municipalities and public clouds. The system enables resilient and secure backup of citizen data in a cost effective and flexible way [3]. Instead of requiring remote backup data centres for each municipality by pooling resources, all operators have access to a large distributed storage network where data can be fragmented and stored.
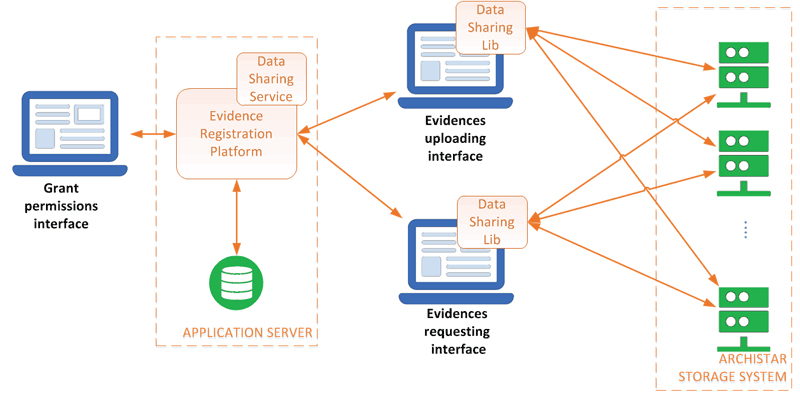
Figure 1: Evidence registration platform architecture.
On the very same principle, ETRA Investigación y Desarrollo S.A. developed a smart city application for law enforcement agencies to gather and share digital evidence, e.g. CCTV video material or images of car number plates in a parking garage, in a trustworthy way. The idea of the system is that storage nodes are operated by different authorities and build a storage network without a single point of trust or failure. A key component of this platform is the Data Sharing Lib which encodes the file in secret shares which are then sent to different storage nodes. The system allows parking/traffic managers to upload the files upon request, and the law enforcement officer to access the files only if there is an authorisation for it. A data protection officer role is crucial to approve / reject the operations that take place in this system. Once the officer is allowed to download the file, the Data Sharing Lib requests the secret shares to the remote nodes in the Archistar Storage System and once received, it decrypts and joints them in a single file again. The combination of the methods presented result in a secure and resilient distributed system, which provides a trustworthy, controlled and transparent access to sensitive data.
Links:
https://prismacloud.eu
https://at.linkedin.com/in/prismacloud
Twitter: @prismacloud, http://twitter.com/prismacloud
http://cordis.europa.eu/project/rcn/194266_en.html
References:
[1] T. Lorünser, D. Slamanig, T. Länger, and H. C. Pöhls: „PRISMACLOUD Tools: A Cryptographic Toolbox for Increasing Security in Cloud Services,” ARES 2016, pp. 733-741, http://dx.doi.org/10.1109/ARES.2016.62
[2] T. Lorünser, A. Happe, and D. Slamanig: “ARCHISTAR: Towards Secure and Robust Cloud Based Data Sharing,” IEEE 7th International Conference on Cloud Computing Technology and Science, CloudCom 2015, IEEE, 2015, https://doi.org/10.1109/CloudCom.2015.71
[3] A. Happe, F. Wohner, T. Lorünser: „The Archistar Secret-Sharing Backup Proxy,” ARES 2017, pp. 88:1--88:8, https://doi.org/10.1145/3098954.3104055
Please contact:
Thomas Lorünser
AIT Austrian Institute of Technology GmbH
+43 664 8157857










