by Stephan Krenn, Thomas Lorünser and Christoph Striecks (AIT)
A large body of research in cryptography was established over recent decades but little of it has been commercialised. This is to the detriment of cloud computing, where the new methods would help to establish end-to-end security, which is not yet common practice.
Cloud computing has made its way into all domains and remains one of the major growth areas in information and communication technology. It will also form the main backend platform of the internet of things and therefore play a crucial role in information society. Nevertheless, it still suffers from its outsourcing paradigm and intrinsic security and privacy problems.
Cryptographic research has made substantial progress over recent years and now provides a portfolio of mature cryptographic primitives and protocols suitable for addressing several of these problems in an effective and efficient way. Nevertheless, there still exists a substantial gap between what is possible and what is actually available in the cloud.
In PRISMACLOUD [L1] and CREDENTIAL [L2] we analysed the situation, extracted main inhibitors and developed promotors for the use and integration of cryptography in engineering work flows of interdisciplinary projects.
Inhibitors
Going from specification to implementation requires substantial cryptographic knowledge to be able to translate the very compact and abstract specifications provided in the literature and very often they focus on formal specifications and proofs, but leave real-world aspects unspecified. Furthermore, implementing cryptographic schemes also requires non-standard skills from software engineers to exclude side-channel attacks (e.g., timing attacks). Overall, this makes the secure, sound, and efficient realisation of cryptographic protocols published in the literature a time-consuming, expensive and potentially error-prone task.
While even theoretical cryptographic research is often motivated with applications, typically no market-driven requirements engineering is performed. Specifically, the motivation aims at other cryptographers rather than practitioners, and therefore does not address real-world problems adequately. In fact, the gap between cryptographic theory and practice used to be huge.
While security can be used as market differentiator, we see little commercial interest in comprehensive practical usage of cryptography for this purpose. This is because the used technologies are mostly hidden from the user for best usability and there is normally no gain in functionality that is visible to a user, hence, the added value is hard to grasp.
Establishing trust into novel algorithms before they get adopted by industry often takes significant amounts of time, e.g., because of security engineers waiting for them to be standardised. Although a conservative approach makes sense, many results are already mature enough to be picked up for commercial use, especially in the field of public key cryptography, where rigorous security proofs can at least partially replace the test of time.
Finally, due to the missing knowledge about novel technologies, it is not easy for developers and architects to understand what could be possible and which solutions really have practical relevance from the large amount of published work in the literature.
Promotors
Systematically addressing the multidisciplinarity in our projects required the development of a system architecture as a first step. It was important to encapsulate expert knowledge in different domains ranging from theoretical cryptography, up to service and application development.
The architecture was then used as a basis for a modern tool and service based engineering approach, which was essential for integration into modern software development life cycles. A tool in our context is a well specified combination of cryptographic methods which serves a specific purpose and comes with readymade cryptographic software and hardware components to system developers. The tools must be easily configurable and usable without cryptographic knowledge, only support a limited set of options and, ideally, already come preconfigured for most typical application scenarios. Additionally, by integrating the tools into ready-made security enhanced cloud (micro-)services it became even easier for developers to integrate them into applications. By doing so, we could further reduce the security knowledge required for system architects and developers to apply the cryptography and therefore significantly lower the entry bar for use in applications.
Although standardisation can be a tedious process, it provides multiple opportunities for an accelerated uptake of cryptographic cloud solutions. However, for best proliferation of the technologies the full architectural stack must be addressed in the standardisation efforts. In our case, it was not enough to initiate standards for new cryptographic schemes, we also had to make sure that the new cryptographic capabilities became visible in cloud service level agreements (SLAs), as the ISO/IEC 19086 series.
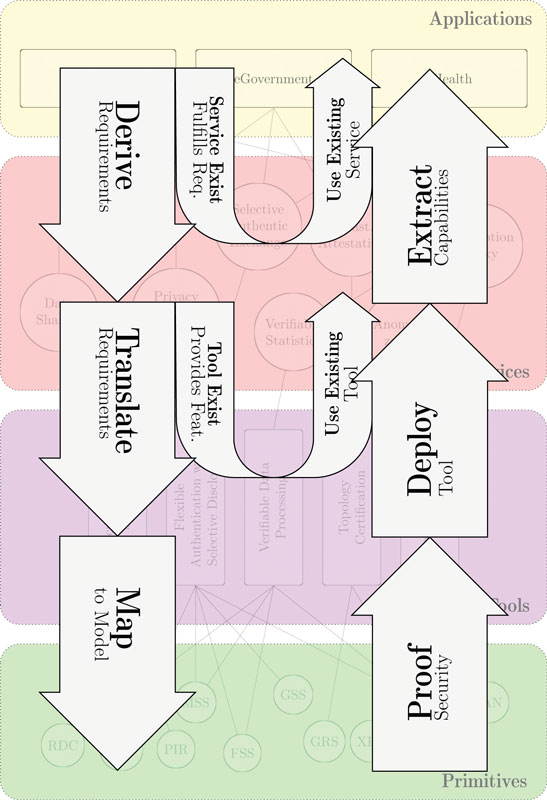
The engineering methodology overview.
Another issue of importance is usability for all stakeholders, which are end users, application designers, cloud service designers as well as cryptographic tool designers who need to share a common understanding of the basic technology. The tool designers and the cloud service designers need to understand the requirements of the end users, while the cloud service designers need to understand the capabilities of the cryptographic tools so that they employ them in the intended way. These complex requirements can efficiently be addressed by using design patterns, and specifically cloud security and privacy design patterns, as well as human computer interaction (HCI) patterns.
This short list of promotors turned out to be the most effective approaches and procedures during our project work in recent years and helped to mitigate many of the main roadblocks mentioned above.
Links:
[L1]: https://prismacloud.eu,
https://at.linkedin.com/in/prismacloud
twitter:@prismacloud, http://twitter.com/prismacloud
http://cordis.europa.eu/project/rcn/194266_en.html
[L2] https://credential.eu/
References:
[1] T. Lorünser, S. Krenn, C. Striecks, T. Länger: “Agile cryptographic solutions for the cloud”, Elektrotechnik und Informationstechnik 134(7), pp. 364-369 (2017)
[2] F. Karegar, et al.: “Opportunities and Challenges of CREDENTIAL - Towards a Metadata-Privacy Respecting Identity Provider”, Privacy and Identity Management 2016, pp. 76-91
[3] T. Lorünser, D. Slamanig, T. Länger, and H. C. Pöhls: “PRISMACLOUD Tools: A Cryptographic Toolbox for Increasing Security in Cloud Services”, ARES 2016, pp. 733-741
Please contact:
Thomas Lorünser
AIT Austrian Institute of Technology GmbH
+43 664 8157857,










