by Daniel Augot (Inria, École polytechnique, and Université Paris-Saclay), Hervé Chabanne (OT-Morpho and Telecom Paristech) and William George (École polytechnique and Université Paris-Saclay)
We propose a way for users to obtain assured identities based on face-to-face proofing that can then be validated against a record on Bitcoin's blockchain. We obtain anonymity for users by making use of a scheme of Brands to store a commitment against which one can perform zero-knowledge proofs of identity and also enforce the confidentiality of the underlying data by letting users control a secret of their own. This way, users can gain access to services thanks to the identity records of our proposal.
We authenticate part of our identity with documents provided by third parties. These can be primary forms of identification like passports or driver licenses, issued by governments, but can be weaker, like bills provided by utility companies (banking, energy, phone). Our joint ongoing research between École polytechnique, Inria, and OT-Morpho (former Safran Identity and Security) consists in thinking of a blockchain as a platform for publishing such identity documents, taking advantage of the public availability, integrity and openness of the Bitcoin blockchain, while we also want to provide strong privacy for users. A natural idea, already proposed by MIT for academic diplomas [1], is to publish hashes of digitally signed certificates, using the “OP_RETURN” facility of Bitcoin transactions, which enables embedding 80 bytes of arbitrary data in a transaction. Our research is building and improving on this proposal, by considering digital certificates which do no reveal anything about their owner identity.
This can be achieved with Brands' certificates, and associated zero-knowledge proofs [2], which are as follows. Suppose an identity has n fields, (X1, …, Xn), with an auxiliary random X0, to prevent dictionary attacks. Let G be the group associated to the elliptic curve underlying Bitcoin signatures, which has 256-bit size (32 bytes). Knowing the DLREP of a given public h enables to make powerful zero-knowledge proofs. (see Figure 1).
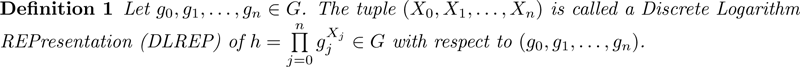
Figure 1: Discrete Logarithm Representation of h.
Being in possession of the Discrete Logarithm Representation (DLREP) of h, the prover can authenticate by proving knowledge while revealing no fields, or, if required, may reveal one or several fields to the verifier. Moreover, the prover can also prove more complicated statements about her identity. This provides the user a tight control of divulged information, in a “PIMS” way [3]. Proof verification can be done by service providers, and by an intermediate service enabler (for single sign-on).
There are various ways for users to build h and convince identity providers of its validity, thanks again to Brands' proofs. The service enabler can then sign it, and h can be made public without revealing anything about its owner, except that a strong, validated, identity is blindly encoded in h. Also, the random X0 is not known to the identity provider, which thus cannot make fraudulent proofs.
Bitcoin mechanisms make it easy to insert such a h (32-bytes short) in the “OP_RETURN” field (80 bytes) of a transaction, by identity providers or utility services. Such a transaction being signed with the underlying Bitcoin mechanisms, this provides a proof that the issuer has accepted h from the user. Using the blockchain, the user can point to the transaction which contains its h, and use it to authenticate to a service provider. It is well known that Bitcoin has limited bandwidth and this problem can be alleviated by publishing roots of Merkle trees of users h's. Updating identities can be also done, and revocation seems easier using a public blockchain.
Using the Bitcoin blockchain offers several advantages. In particular, its robustness, openness, public availability, and the cryptographic platform it provides, make it easy to deploy a cryptographic solution, without heavy software engineering, and without relying on a central body for providing servers, bandwidth and availability. These features could help weak or failed states to issue identities.
We are also imagining ways to take advantage of the linkability of Bitcoin transactions. A user's proof may be linked to the certificate issuer's transaction, and/or, when convinced by the proof, the service provider could also publish an “accept” transaction, linked to the proof. A reputation can then be built, under the user's control. We are furthermore investigating the semantics of these linkability features.
References
[1] J. Nazaré, K. Hamilton, P. Schmidt: “Digital certificates project”, online, source code available on https://github.com/digital-certificates, Consulted 2016, http://certificates.media.mit.edu.
[2] S. Brands: “Rethinking Public Key Infrastructures and Digital Certificates (Building in Privacy)”, MIT Press, Cambridge, MA, USA, 2000.
[3] S. Abiteboul, B. André, D. Kaplan: “Managing your digital life”, Commun. ACM, 58(5):32-35, April 2015.
Please contact:
Daniel Augot
Inria, Laboratoire LIX, École Polytechnique & CNRS UMR 7161, Université Paris-Saclay, France
Hervé Chabanne
OT-Morpho, Télécom Paristech, France
William George
Laboratoire LIX, École Polytechnique & CNRS UMR 7161, Université Paris-Saclay, France










