by Christoph Schmittner, Zhendong Ma, Thomas Gruber and Erwin Schoitsch (AIT)
Connected, intelligent, and autonomous vehicles pose new safety and security challenges. A systematic and holistic safety and security approach is a key to addressing these challenges. Safety and security co-engineering in the automotive domain considers the coordination and interaction of the lifecycles, methodologies, and techniques of the two disciplines, as well as the development of corresponding standards.
Connected, intelligent, and autonomous vehicles transform traditionally mechanical and electrical cars into ‘networked computers on wheels’. Along with the many technology breakthroughs and benefits, challenges of safety and security become imminent and real. The electrical and electronic systems that control an automated vehicle are no longer immune to cyberattacks commonly seen in IT systems. A combined safety and security approach is necessary to address the challenges that have arisen in recent years, including co-engineering activities, methodologies, techniques, and a coherent approach in relevant standards.
The correct identification of safety and security goals is the first step in the development lifecycle of a system. The identification of hazards and assets reveals potentially vulnerable parts of a system. Subsequently, a first concept architecture for these parts is defined which can then be analysed to identify potential weaknesses, e.g., if a failure or an attack could trigger an intolerable risk. In both cases, requirements are defined which aim at preventing such risks. Different methods should be used to address various issues during the development lifecycle with different levels of detail. Figure 1 displays the most common methods in the respective phases of the V-model.
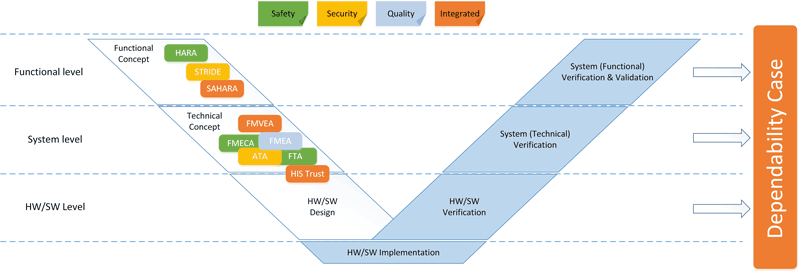 Figure 1: Dependability engineering in the development lifecycle.
Figure 1: Dependability engineering in the development lifecycle.
A useful security technique is threat modelling, which defines a theoretical model of perceived threats to a system. We developed a systematic approach to apply threat modelling to automotive security analysis and combined it with the Failure Mode and Effect Analysis to FMVEA, Failure Modes, Vulnerabilities and Effects Analysis [1]. Threat modelling should be performed in all phases of the development lifecycle. Different levels of detail can be used along the lifecycle with different objectives in each phase. In the concept phase, modelling results in high-level security and safety requirements and security concepts. In the product development phase, it can define technical security and safety requirements for functional, security and safety design. It can also be used to discover design vulnerability and flaws and to specify comprehensive requirements that can be verified and validated in unit and integration testing in an iterative way in parallel to system design and implementation. In the production and operation phase, it prioritises risks and prepares penetration testing on completed automotive components and systems. A knowledge base is continuously enriched by the output from threat and failure modelling activities, enabling the reuse of artefacts across different projects. Further, related vulnerabilities and threats from external sources are promptly incorporated into the threat and mitigation catalogue.
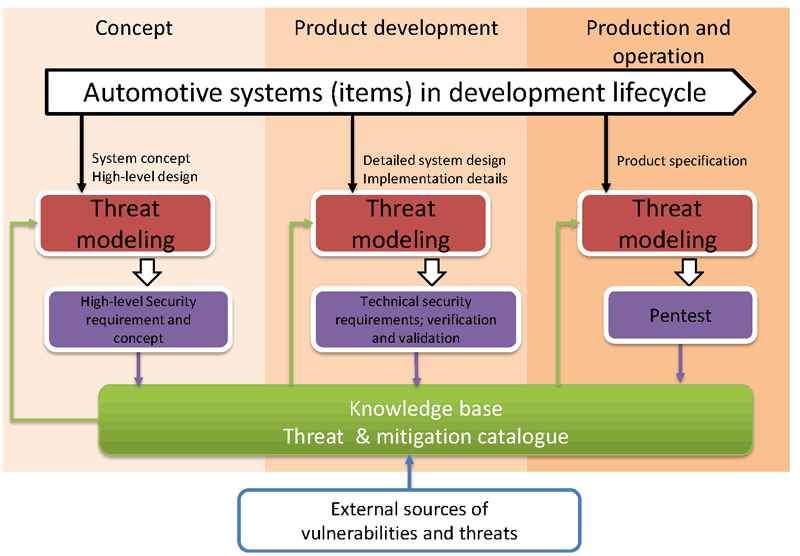
Figure 2: Iterative threat modelling and mitigation during the development lifecycle.
A new version of the automotive functional safety standard ISO 26262 is currently under development. Although not suited for completely autonomous cars, automated functions are considered to a significantly higher degree than in the first edition. This is supported by the new standard development SotIF (Safety of the Intended Functionality). SotIF describes nominal performance metrics for sensor systems and automated functions. This regulates the area where a system may cause a hazard without a failure in the traditional understanding. The processing algorithm made, based on the received understanding of the environment, a hazardous decision without a fault in the system. This could be caused by a limitation in the sensor algorithm or signal noise or insufficient performance of a sensor. A new ISO/SAE automotive security standard completes these activities. All three standards need to consider the increased interaction and co-engineering between system-, safety- and security- engineers. AIT is involved in the development of all three standards and is a member of the cybersecurity and safety task group that developed the Annex. The goal of interaction and communication points is to lay the groundwork for a workflow with shared phases [2].
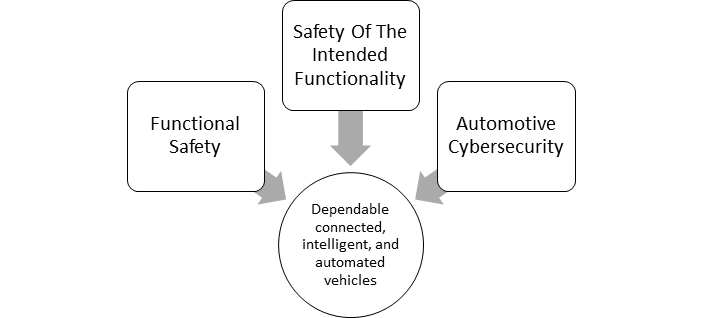
Figure 3: SotIF approach combined with safety and cybersecurity co-engineering.
AIT has further developed automotive safety and security co-engineering in the Artemis project EMC2 and demonstrated it for a Hybrid Electric Powertrain control system of AVL. In the SCRIPT project, we applied the newly published SAE J3061 standard for conducting TARA in the development of a secure communication gateway for autonomous off-road vehicles [3]. We are also working towards an efficient and model-based approach to multi-concern assurance including safety; security, reliability, and availability in the scope of ECSEL project AMASS. AIT will take the next step towards safe, secure and cost-efficient automated driving in the ECSEL project AUTODRIVE starting in 2017. The interaction point approach of ISO 26262 Edition 2 will be the object of research in the ECSEL project AQUAS also starting in 2017.
Links:
[L1] http://www.ait.ac.at/en/about-the-ait/center/center-for-digital-safety-security/
[L2] http://www.emc2-project.eu/
[L3] https://www.tttech.com/company/research-projects/austrian/script/
[L4] http://www.amass-ecsel.eu/
References:
[1] C. Schmittner, Z. Ma, E. Schoitsch, T. Gruber: “A Case Study of FMVEA and CHASSIS as Safety and Security Co-Analysis Method for Automotive Cyber-physical Systems,” in 1st ACM Workshop on Cyber-Physical System Security, Apr. 2015, ACM, pp. 69-80.
[2] E. Schoitsch, C. Schmittner, Z. Ma, T. Gruber: “The Need for Safety & Cyber-Security Co-engineering and Standardization for Highly Automated Automotive Vehicles”, AMAA 2015, Berlin, Germany, July 2015.
[3] C. Schmittner, et al.: “Using SAE J3061 for Automotive Security Requirement Engineering”, in International Conference on Computer Safety, Reliability, and Security, pp. 157-170. Springer, 2016.
Please contact:
Christoph Schmittner, Zhendong Ma, Thomas Gruber, Erwin Schoitsch
AIT, Austria










