by Paolo Mori, Andrea Saracino (IIT-CNR) and Francesco Di Cerbo (SAP Labs France)
In the frame of the European project CoCoCloud (Confidential and Compliant Clouds) we propose a distributed and general framework to enforce usage control policies on data shared in the cloud environment.
Cloud services are becoming increasingly pervasive in almost every field of information technology. The reasons for this are clear: cloud computing allows specific data, such as documents, to be created and seamlessly accessed from anywhere on the globe, and also facilitates document sharing. Furthermore, mobile devices such as smartphones and tablets allow access to documents stored in the cloud anywhere, anytime. After a document has been published in the cloud, the data producer is handing over partial control of the document to the cloud provider and to the other users with whom the document is shared. It is important, therefore, that the sharing framework properly guarantees data security and privacy. Enforcing security and privacy on documents often requires the continuous monitoring of conditions concerning the subjects who access the document, the document itself and additional information related to the context in which access is performed.
To handle these issues, within the EU FP7 project ‘Confidential and Compliant Clouds’ [L1] we designed and implemented a distributed and general framework to enforce usage control policies on data shared in the cloud environment. The proposed framework enables monitoring and enforcement of security policies related both to the right to access specific documents (access control) and to use them over time (usage control). A peculiarity of usage control is that ongoing access to a document is interrupted as soon as a modification in the attributes of the subject, of the document, or of the environment causes a policy violation.
In the proposed framework, each document published in the cloud embeds one or more usage control policies (sticky policies). The policy specifies the conditions to access the document, e.g., the subject(s) authorised to access and their required features (i.e., attributes such as role, reputation, location, etc.), features of the document (size, creation date, etc.), and external conditions that build the context of environment (network connection, date and time, etc.) [2]. Furthermore, the policy allows specific actions on the controlled system to be forced. These are named obligations and are used, for instance, to send notifications to the document producer [1].
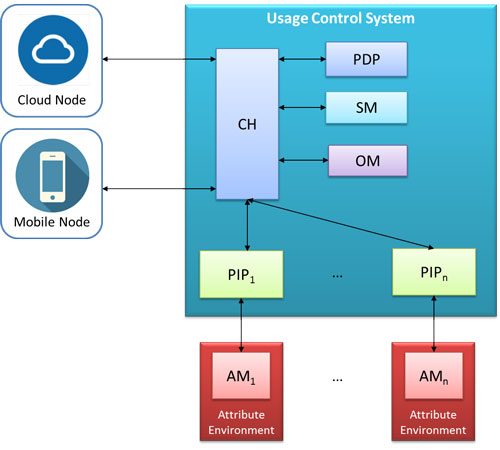
Figure 1: Logical Architecture of the Usage Control Framework.
Figure 1 shows the logical architecture of the proposed framework, which relies on the well established model defined by Sandhu [3]. The policy decision point (PDP) evaluates access and usage requests, matching them against the security policies, returning either permit or deny as an answer. The policy information points (PIPs) collect information concerning subject, object and environment, retrieving them from external components named attribute managers (AM). The cloud and mobile nodes enforce the security policies by granting or blocking access to documents, according to the decisions of the PDP. The obligation manager (OM) is responsible for handling the obligations contained in policies, forcing the cloud and mobile nodes to perform specific actions, such as sending a notification message when a document is accessed. Finally, the context handler (CH) manages the interactions among the previous components.
As discussed, the framework is designed to operate both in cloud environments and mobile devices. In the cloud use case, the enforcement is performed by managing access to data in the cloud through cloud services. The cloud service allows only those operations permitted by the policy, and is also able to revoke an ongoing access, closing the service when a policy condition is no longer matched. On mobile devices in contrast, usage control is enforced directly on the device. In particular, when an access request is performed, the document to be accessed is downloaded directly on the device, in a protected memory space not accessible to the user, nor to other apps running on the mobile device. The mobile node is embodied by an application that allows controlled access to the stored documents, denying the access when the PDP returns a deny decision. Security of files stored on the device is ensured by means of asymmetric key encryption and trusted computing base functionalities, which will ensure both data confidentiality and integrity.
The proposed framework is general and could be applied in a range of environments and applications, such as e-health or business company premises. In e-health, for example, the framework could be used to control the access rights of a practitioner to the electronic data of a patient. One way in which it could be applied in this environment is to restrict access to patient data, from a mobile device, to practitioners that are directly responsible for the patient and / or only when the practitioner is on the hospital premises. Even if the practitioner has the clinical record of the patient opened, once he or she leaves the hospital, the position acquired from the mobile device changes, and access is revoked: the application will automatically close the document and forbid further access attempts until the conditions match the policy again. It is also possible to enforce a specific retention period for patient data, guaranteeing that the data will be deleted in order to comply with data privacy regulations.
Link: [L1] http://www.coco-cloud.eu/
References:
[1] F. Di Cerbo, et al.: “Sticky policies for mobile devices”, in Proc. of the 18th ACM Symposium on Access Control Models and Technologies, SACMAT ‘13, 257-260, 2013.
[2] A. Lazouski et al.: “Stateful usage control for android mobile devices”, in Proc. of the Security and Trust Management - 10th International Workshop, STM 2014, 97–112, 2014.
[3] J. Park, R. Sandhu: “The UCONABC usage control model”, ACM Trans. Inf. Syst. Secur. 7(1), 128-174, 2004.
Please contact:
Paolo Mori and Andrea Saracino
IIT-CNR, Italy
Francesco Di Cerbo
SAP Labs France,











