by Nicolás Notario (Atos), Stephan Krenn (AIT), Bernd Zwattendorfer (Stiftung SIC ) and Felix Hörandner (TU Graz)
CREDENTIAL (seCuRE clouD idENTIty wALlet) is combining technological advances to create privacy-preserving data storage, data sharing and identity management services.
With rising mobility and internet usage, the demand for digital services is increasing and has reached critical and high assurance domains such as e-Government, e-Health and e-Business. One fundamental building block that is needed for many such applications is secure data sharing functionality. The main ambition of the CREDENTIAL project [L1, L2, L3] is therefore to develop a data sharing platform that provides strong privacy, security, and authenticity guarantees to its users. As a special case, for the sharing of identity data, a privacy preserving identity management service will be implemented.
The security of the developed services will rely on the combination of three key technologies (see Figure 1): end-to-end proxy re-encryption, privacy preserving technologies such as redactable signatures, and strong hardware-based multi-factor authentication.
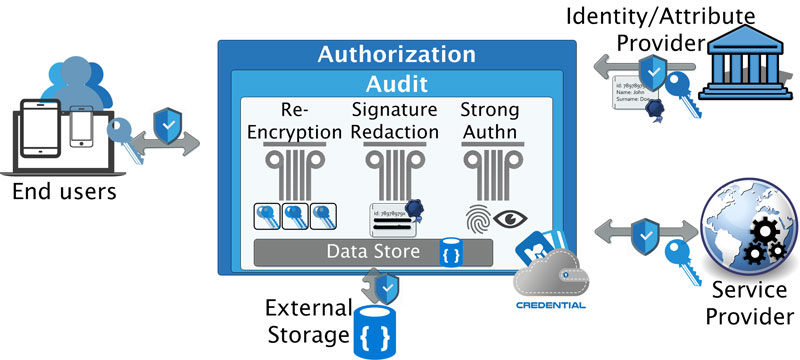
Figure 1: CREDENTIAL high level view and its main pillars.
The first key technology is proxy re-encryption (PRE) [1], which protects the confidentiality of personal data and enables secure end-to-end encrypted data sharing. In general, PRE allows a proxy to transform a ciphertext encrypted for one recipient A to a ciphertext for another recipient B, without getting access to the underlying plaintext or involved private key material during intermediate steps. For this operation, the proxy requires a re-encryption key that was generated from B's public key as well as A's private key, who thereby grants delegation rights. In CREDENTIAL, users encrypt their sensitive data for themselves before uploading them to the cloud, which ensures confidentiality. PRE enables users to securely share their encrypted data by providing a re-encryption key that is used by the cloud system to transform the ciphertext for another selected participant. As a result, the confidentiality of the users' data is protected even in a possibly insecure cloud environment, while the users are still able to securely share their data.
The second main technology included in CREDENTIAL are redactable signature schemes [2], which extend the basic functionality of standard digital signatures as follows: Upon signing, the signer can define specific parts of the message which may later be blanked out (redacted). After receiving the document and the signature, a party can now remove any subset of those predefined parts, and simultaneously modify the signature such that it is valid for the modified message. This way, the authenticity of the revealed parts of the message can be guaranteed, while no information is leaked about the redacted blocks.
Within CREDENTIAL, redactable signatures will be used for the privacy preserving identity management functionality: an authority can sign the users' electronic identities using redactable signatures. The users can then choose, from their signed identities, which specific attributes they wish to disclose to the service provider (e.g., only the birth data to prove their age).
In order to provide a truthfully secure system, CREDENTIAL follows a ‘Defence in depth’ approach, starting by including in the CREDENTIAL Wallet our third technological pillar, multi-factor authentication protocols that will univocally biometrically link the authentication process to an identity, without the need of disclosing such identity or any personal data to the Wallet or to the service providers.
Finally, one important innovative aspect of CREDENTIAL is its design process, which is carefully planned to have a multi-stakeholder point of view, taking special consideration for user-centric and privacy aspects from social, technical and legal perspectives. On the one hand, and from a functional perspective, stakeholders of three different domains are providing their own view of the system and how it can be leveraged in their own domains. These domain-specific views are consolidated into a logical view of the to-be system, representing it through a Data Flow Diagram (DFD). This DFD illustrates the system’s functionality and supports the extraction of valuable insights from a security and privacy perspective. On the other hand, CREDENTIAL combines and leverages both STRIDE and LINDDUN methodologies for security and privacy threat analysis in order to provide a full security and privacy assessment, based on the consolidated view of the system already mentioned. This view is being systematically analysed, identifying, categorising (e.g., identifiability, tampering or linkability threats) and prioritising the different threats that may challenge CREDENTIAL’s objectives.
The recently published EU General Data Protection Regulation [3] will be a catalyst for the adoption of CREDENTIAL. The main objectives of this regulation are to strengthen and unify the protection of personal data processing across the EU and to give the user full control of their personal data. To achieve the requirements outlined in this regulation, CREDENTIAL follows a data protection-by-design approach, will provide easier access to own personal data, and will facilitate personal data transfer between service providers.
CREDENTIAL is an EU H2020 three year research project which started in October 2015. The estimated costs of the project are € 6.6 million. The consortium consists of a well-balanced mixture from six European countries consisting of industry partners, universities, and applied research institutions.
Links:
[L1] https://credential.eu/
[L2] https://twitter.com/CredentialH2020
[L3] https://www.linkedin.com/in/credential
References:
[1] Matt Blaze, G. Bleumer, M. Strauss: “Divertible protocols and atomic proxy cryptography”, in Proc. of Eurocrypt ’98, volume 1403, pages 127–144, 1998.
[2] A. Kundu, E. Bertino: “Structural signatures for tree data structures”, in Proc. of the VLDB Endowment 1(1), 138–150, 2008.
[3] Official Journal of the EU, Regulation (EU) 2016/679 of the European Parliament and of the Council of 27 April 2016 on the protection of natural persons with regard to the processing of personal data and on the free movement of such data.
Please contact:
Nicolás Notario, Atos Spain (Atos Research & Innovation)
Stephan Krenn, AIT Austrian Institute of Technology GmbH
+43 664 88256006











