by Florian Skopik, Maria Leitner and Timea Pahi (AIT Austrian Institute of Technology)
The final draft of the Network and Information Security (NIS) Directive stipulates that operators of essential services and digital service providers must report certain security incidents to competent authorities or national computer security incident response teams (CSIRTs) in their member state. It is the authorities’ job to collect and process information about security incidents to increase network security in all organisations by issuing early warnings, assisting in mitigation actions, or distributing recommendations and best practices. However, before an appropriate response to a severe cyber situation can be undertaken, it is essential to establish cyber situational awareness – which turns out to be a tricky task.
The smooth operation of critical infrastructures, such as telecommunications or electricity supply is essential for our society. In recent years, however, operators of critical infrastructures have increasingly struggled with cybersecurity problems. Through the use of ICT standard products and the increasing network interdependencies, the attack surfaces and channels have multiplied. New approaches are required to address this serious security situation. One promising approach is the exchange of security incident information and status information of critical services across organisational boundaries with strategic partners and national authorities. The main goal is to create an extensive cyber situational awareness picture about potential threats and ongoing incidents, which is a prerequisite for an effective preparation and assistance in case of large-scale incidents.
The Challenges of Establishing Situational Awareness
Critical services, such as energy supply, transportation and banking services, are largely managed by private operators. Since these services are essential to maintaining public order and safety, it is the state’s responsibility – and in the state’s best interest - to guarantee the security of the related infrastructures [1]. A formal arrangement between the public and private sectors must therefore be established. Ideally, the state would directly support infrastructure providers to secure their service operations by providing them with important security information. The infrastructure providers, in turn, would provide to the state, security-relevant information, such as the status of their service or indicators of compromise in their networks. This data from every single organisation is essential to create a clear picture and cyber situational awareness of the operational environment, thus to create the basis for justified and effective decision-making by authorities at a national level.
In recent years, technical solutions for capturing network data and processing within organisations have been developed [2], and high-level security strategies have been already formulated in the national scope [3]. However, the question of how technical information from cyberspace can be processed and presented in such a cyber-situational awareness picture, is a challenging problem for which there is still no adequate solution. The objective of the project CISA (Cyber Incident Situational Awareness) is to fill this gap and create a link between the technical data and the strategic decisions required to mitigate cyber threats at national level. Cyber situational awareness (CSA) is a required capability of national stakeholders and governments to effectively perform their operations relying on the contemporary knowledge about the technical status of critical infrastructures. This situational awareness requires a holistic methodology to synthesise perception, identify and visually represent the current trends, and construct future projections.
Design Principles of the CISA Approach
The CISA approach carefully follows considered design principles to facilitate its fast adoption. The full approach is sketched in Figure 1. CISA foresees private as well as governmental stakeholders to share information with a cybersecurity centre, and covers all management and decision levels from the organisational scope to the (pan-)national scope in order to provide a holistic picture of the cyber threats in the state. Here it is important to establish an understanding of the numerous categories of relevant information, which need to be treated differently. For instance, low level technical information, such as IP addresses of command and control servers or descriptions of technical vulnerabilities, need to be modelled and shared according to different policies compared with higher-level business information, such as the potential economic impact of certain service outages. In that sense, CISA aims to adopt organisational structures and existing reporting channels (e.g., links to CSIRTs) to avoid any unnecessary overheads and lower the barriers for all stakeholders to use and support CISA. It is noteworthy that CISA respects the human-in-the-loop model. This means it attempts to support the appropriate balance between manual human-controlled activities, such as incident classification or preparation of recommendations, and automatic processes, such as intrusion detection, big data analysis etc.
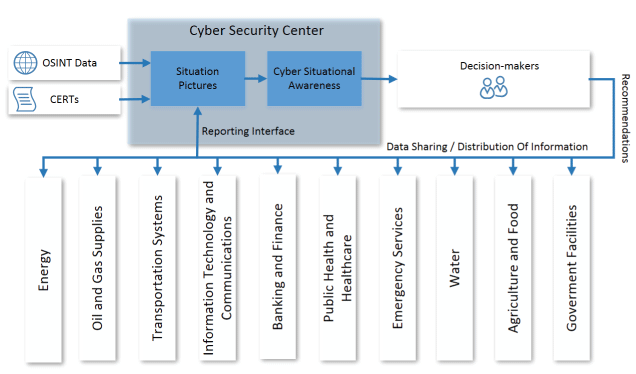
Figure 1: Approach to establishing national cyber situational awareness for competent decision makers.
The model foresees that numerous cyber situational awareness pictures are created in a cybersecurity centre – depending on the type of affected decision maker (civil, military) and the level at which the decisions need to be made (operational, tactical, strategic). These situational awareness pictures may be further enriched with external information, originating from open-source intelligence (OSINT), CSIRTs as well as closed (national, European) intelligence sources.
Eventually, recommendations to carefully selected recipient circles are issued to mitigate the effects of ongoing/recent incidents and to increase the preparedness for future ones (e.g., through distributing early warnings).
The Project CISA and its Consortium
In order to attain these ambitious goals and finally ensure the wide applicability of developed tools and procedures, the project consortium consists of a vital mix of academics with deep knowledge in security (Austrian institute of Technology, SBA Research), security solution vendors and service providers (Thales Austria, T-Systems Austria), and industry practitioners (Repuco, Infraprotect). Furthermore, the involvement of legal experts (Vienna Centre for Legal Informatics (WZRI), Netelligenz e.U.) is essential to ensure compliance with regulations and the legal framework and by the employment of a data protection impact assessment and privacy enhancing technologies the necessary privacy requirements are fulfilled. Eventually a project in this area can only be successful with the active involvement and support of the competent authorities (Ministry of the Interior, Ministry of Defence and Sports, Federal Chancellery). In addition to the development of scientific methods, the proper demonstration of the applicability of CISA’s results in a real-world environment is of paramount importance in order to test and evaluate the planned system. Therefore, exercises with external stakeholders on a national scale are planned together with the competent authorities. CISA is a two-year national project running from 2015 to 2017 and is funded by the Austrian security-research program KIRAS and by the Austrian Ministry for Transport, Innovation and Technology (BMVIT).
Link:
http://www.kiras.at/projects/detail/?tx_ttnews[tt_news]=535&cHash=519847e6fc040eac8cb0a6af14a1f47b&L=1
References:
[1] Network and Information Security (NIS) Directive; https://ec.europa.eu/digital-single-market/en/news/network-and-information-security-nis-directive, 15/03/2016.
[2] Leopold, H., Bleier, T., & Skopik, F.(2015) Cyber Attack Information System. Springer-Verlag Berlin Heidelberg.
[3] ENISA, National cyber Security Strategies, Practical Guide on Development and Execution, December 2012
Please contact:
Florian Skopik
AIT Austrian Institute of Technology, Austria
+43 664 8251495











