by Robert N. M, Watson, Simon W. Moore (University of Cambridge) and Peter G. Neumann (SRI International)
The CHERI hardware-software system has the potential to provide unprecedented security, reliability, assurance, ease of programmability, and compatibility.
Our University of Cambridge and SRI International team project is engaged in a multi-year hardware and software co-design project to produce the CHERI (Capability Hardware Enhanced RISC Instructions) system that provides fine-grained bounds checking as well as compartmentalisation managed by software and enforced in hardware. At its core is an old (historically) but new (in its present form) hardware data type: a tagged 128-bit fat-pointer capability that embodies an address, bounds, and permissions. The CHERI instruction set architecture (ISA) guarantees monotonically decreasing access rights (i.e., there can be no privilege escalation). The CHERI hardware tracks pointer integrity and enforces bounds checking. The CHERI ISA is defined in a formally based specification language, and several approaches to its formal analysis are underway. Three of our most recent papers are included in the references [1,2,3].
Software can utilize our capability hardware mechanism at a diverse range of levels. Our C compiler automatically assigns bounds to all pointers, mitigating well understood but frequently exploited buffer overflow attacks. Attempts to corrupt pointers in memory result in a clean failure rather than data or control-flow vulnerabilities. By combining code and data capabilities, compartments (e.g., sandboxes) can be constructed. Compartmentalisation can be used to prevent known exploits. By applying the principle of least privilege through fine-grained compartmentalisation, it is also possible to mitigate unknown future classes of exploits.
We have made the pragmatic choice to keep page-based virtual memory. Virtual memory is helpful in memory allocation and provides OS managed protection. Capabilities are managed by the software author and compiler. The hybridisation of the two approaches provides much flexibility and allows the two benefits of the two approaches to be exploited in a complementary manner. Where virtual memory is grounded in user and process separation, capabilities provide fine-grained in-address-space protection. For example, a modern web browser will typically use process separation for each tab, separating your banking application from your social media. Such process separation scales poorly, limiting its use. In contrast, a capability system has orders of magnitude better performance and scales elegantly. Thus, in a browser it is possible to sandbox not only each tab but each image rendered, etc.
Our open-source project is supported by the U.S. Department of Defense Advanced Research Projects Agency (DARPA) and some other much smaller sources. It began in 2010, and will continue into early 2018, working towards transferring the hardware-software technology into practical systems. We are exploring significant potential for mainstream use.
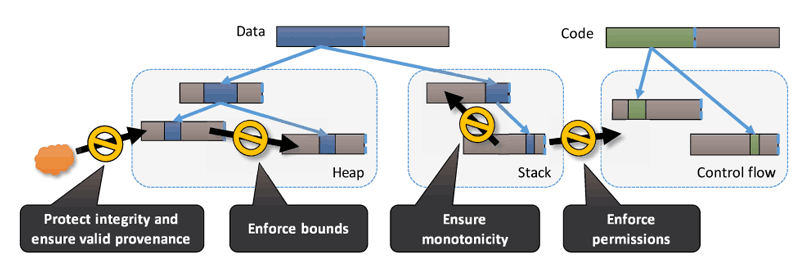
Figure 1: CHERI is a hybrid capability-system architecture supporting both conventional, pure-MMU operating-system designs (such as UNIX and Windows), pure capability-system designs, and hybrid operating-system designs that allow incremental deployment of CHERI’s memory-protection properties within current large C-language TCBs such as operating-system kernels, key libraries, system services, and security-sensitive applications, such as web browsers.
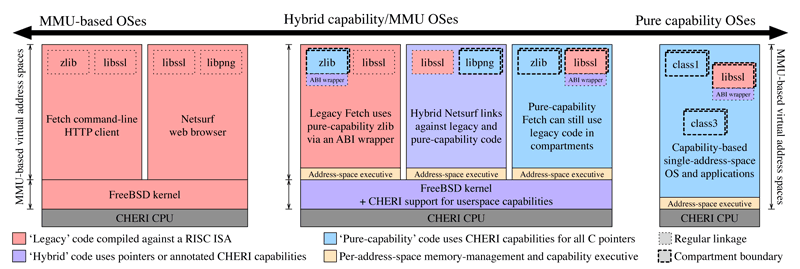
Figure 2: CHERI allows the operating system and compiler to enforce a variety of spatial memory-protection properties on pointers: strong integrity, valid provenance, bounds that enforce access to only the allocation, permissions that prevent inappropriate use, and monotonicity, which ensures that as privileges are removed from capabilities, they cannot be regained. These properties can be used to provide low-level memory safety for C — but also to construct higher-level security models such as software compartmentalisation.
References:
[1] J. Woodruff et al.: “The CHERI capability model: Revisiting RISC in an age of risk”, ISCA 2014, Minneapolis, MN, USA, June 2014.
[2] D. Chisnall et al.: “Beyond the PDP-11: Architectural support for a memory-safe C abstract machine”, ASPLOS 2015, Istanbul, Turkey, March 2015.
[3] R. N. M. Watson et al.: “CHERI: A hybrid capability-system architecture for scalable software compartmentalization, IEEE SSP, San Jose, CA, USA, May 2015.
These papers as well as further reports and publications can be found on the project website: http://www.cl.cam.ac.uk/research/security/ctsrd/
Please contact:
Peter G. Neumann
SRI International, UK
Robert N. M, Watson
University of Cambridge, UK











