by Beatriz Gallego-Nicasio Crespo, Melek Önen and Ghassan Karame
The main goal of the TREDISEC project is to increase trust in cloud technology by providing solutions that enhance data security and provide strong privacy guarantees, without hampering the efficiency-and-reduced-cost attractiveness of existing cloud systems.
The cloud is the go-to technology for companies and businesses these days. Cloud adoption is growing exponentially each year, fueled by new functionalities and capabilities. Although it has many advantages, the cloud also has drawbacks and security-related issues that can make customers shy away from adopting it. Large-scale adoption of the cloud by enterprises and SMEs is hampered by serious concerns about the security and availability of data stored in the cloud. These concerns have been further exacerbated by recent data leak scandals (e.g., corporate data stolen [1], resulting in millions of dollars in losses in just one day) and privacy intrusions (e.g., users’ private information illegally accessed and used for blackmail [2]). Moreover, companies are no longer happy to rely on standard cloud security solutions, instead demanding full control over the security and integrity mechanisms employed to protect their data across its lifecycle. As this data is typically a very valuable asset, security and privacy emerge as key features in cloud offerings. TREDISEC addresses these issues by providing a set of security primitives that enhance the resilience of existing cloud infrastructures against attacks and vulnerabilities, protecting data end-to-end, and thus making secure and trustworthy cloud systems a reality.
Achieving end-to-end security within the cloud environment is nevertheless not a straightforward task. Indeed, end-to-end security is at odds with current functionalities offered by the cloud, as shown in Figure 1. For example, while protecting cloud customers’ data at rest usually requires data encryption solutions, such a security service inherently refrains cloud services from offering standard APIs for efficiently processing these encrypted data.
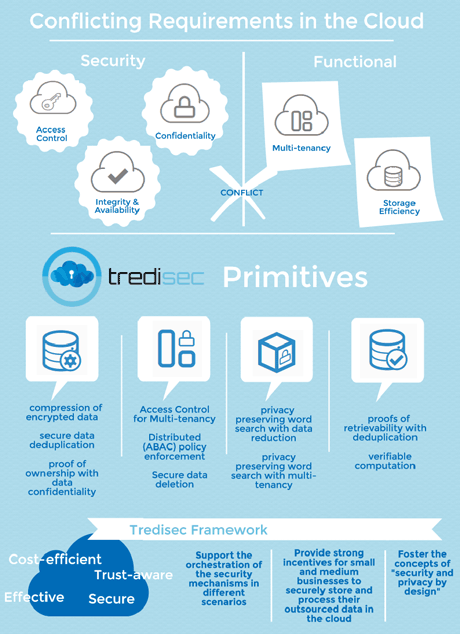
Figure 1: The TREDISEC approach.
TREDISEC addresses security and privacy issues by analyzing, designing and implementing a set of cloud security primitives that are integrated naturally with existing cloud capabilities and functionalities, such as multi-tenancy or storage efficiency. Among other capabilities, these primitives support data reduction, enable secure data processing, enhance data availability and integrity and ensure user isolation and confidentiality in multi-tenant systems. Therefore, the innovation potential of TREDISEC covers:
- Deduplication on encrypted and multi-tenant data
- Means to verify the integrity and availability of multi-tenant data in presence of storage efficiency
- Secure deletion of multi-tenant data in presence of deduplication
- Storage efficiency in presence of securely outsourced database management services
- Secure outsourced analytics/processing in a multi-tenant environment
- Trustworthy, consistent access control for multi-tenancy settings
- Distributed enforcement of access control policies.
Addressing these innovations is only the first step of the project. The subsequent, and more challenging step, is to consider scenarios with multiple functional and security requirements to evaluate the effectiveness of our approach. These security primitives will be integrated and validated in real use case scenarios designed by four partners of the project, representing diverse business goals (for more detail about use cases see the Links section). Namely, our results will be validated onto (1) the Greek Research and Technology Network’s computation and storage cloud (used by the University of Athens), (2) the cloud storage service provided by Arsys, (3) Morpho’s identification solutions using biometric data that are stored in the cloud , and finally (4) SAP use case focuses on migration of legacy databases into a secure cloud, which is an important concern for small, midsized and large enterprises that wish to move their day-to-day business processes (e.g., ERP, CRM, HR) to the cloud.
We believe that the results of TREDISEC will have a big impact in business (both large companies and SMEs), allowing them to achieve greater business throughput, and lowering the barriers to enter new markets. We are fully aware of the problem of adoption of new technologies by companies and believe that TREDISEC will cover at least three of the top five barriers: security, data protection, trust, data access, and portability [3].
This paper is a joint work of the TREDISEC project consortium. The TREDISEC project is funded by the H2020 Framework of the European Commission under grant agreement no. 644412. In this project, nine renowned research institutions and industrial players with balanced expertise in all technical aspects of both security and cloud are working together to address the challenges of the project: Atos Spain (project coordinator), NEC Europe, IBM Research, ETH Zurich, Eurecom, Arsys Internet, Greek Research and Technology Network, SAP SE and Morpho (SAFRAN group).
Links:
TREDISEC official website: http://tredisec.eu
TREDISEC Use Cases Definition: http://tredisec.eu/content/use-cases
References:
[1] Deadline – Sony hack: A Timeline (Last access: 05.11.15), http://kwz.me/QY
[2] Tripwire – The state of security. The Ashley Madison Hack – A Timeline (Last access: 05.11.15), http://kwz.me/QB
[3] European Commission:“Quantitative Estimates of the Demand for Cloud Computing in Europe and the Likely Barriers to Up-take”, 2012, http://kwz.me/Qr
Please contact:
Beatriz Gallego-Nicasio Crespo
Atos, Spain
Tel: +34 912148800
E-mail:











