by Fabio Martinelli, Fabio Massacci, Paolo Mori, Christian Schaefer and Thomas Walter
Capabilities and Ubiquity of mobile devices have dramatically increased in the last few years, with many mobile devices now able to run Java applications, create Internet connections, send SMS messages, and perform other expensive or dangerous operations. As a consequence, better security support is required. We propose an approach to enhance the security support of Java Micro Edition using MIDlets to monitor the usage of mobile device resources.
In recent years, the market for mobile devices such as mobile phones or personal digital assistants (PDAs) has grown significantly. The capabilities of mobile devices have also increased, and up-to-date units can be used to connect to the Internet, read and write e-mails, and also to run Java Micro Edition (Java ME) applications (MIDlets). Moreover, the increase in available bandwidth due to UMTS means that downloading software on mobile devices is becoming more popular.
Yet, the security model provided by Java ME is not flexible enough to allow the spread of MIDlets developed by third-party companies, because it only takes into account the trust in the MIDlet provider. If the principal that signed the MIDlet is on the list of trusted principals stored on the device, the MIDlet is allowed to perform any security-relevant action. On the other hand, MIDlets from unknown providers are not allowed to perform such actions, and the mobile device user is asked to explicitly allow each of them.
To overcome the limitations posed by the model adopted by the standard Java ME security support, the European S3MS project (Security of Software and Services for Mobile Systems) proposes a new paradigm: security by contract. A contract is a claim by a mobile application on the interaction with relevant security features of a mobile platform. At the same time, a policy defines the security requirements of a mobile device, and resides on the device itself. The contract should be published by applications and understood by devices and all stakeholders (users, mobile operators, developers, platform developers etc). The contract is specified at development time as a requirement to the application development teams or as derivation from the analysis of the application. When the application is downloaded onto the device, the contract-matching step is performed to check whether the contract claimed by the application is compliant with the mobile device policy. If the contract-matching step succeeds, the MIDlet can be safely executed on the mobile device.
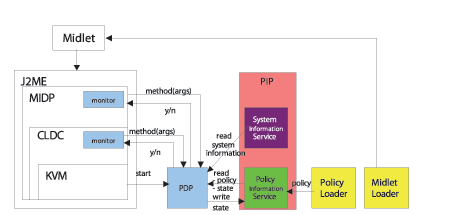
If the contract-matching step is unable to verify whether the MIDlet is compliant with the device policy, the policy enforcement is performed at runtime. The enforcement is based on the continuous monitoring of the MIDlets to control the usage of the mobile device resources.
The architecture for the runtime monitoring of MIDlets follows the reference monitor model, and consists of the following main components:
- The execution monitor is responsible for monitoring the MIDlet during its execution. Specifically, it intercepts all the security-relevant actions that the MIDlet tries to perform on the underlying mobile device, asks the policy decision point to decide whether the action is allowed and enforces the decision by actually executing the action or by returning an error to the MIDlet.
- The policy decision point is responsible for evaluating whether a given action is permitted in the current state by the policy on the mobile device. It is invoked by the execution monitor and contacts the policy information service to get the policy and to manage the policy state, while it exploits the system information service to retrieve information about the mobile device state.
- The policy information service is responsible for managing the policy state. In particular, it stores the policy variables, which could have different scopes.
- The system information service is responsible for providing information about the system, such as the current date and time, the battery state, the CPU load and so on.
- The policy loader is responsible for loading the mobile policy on the mobile device.
- The MIDlet loader is responsible for loading the MIDlet on the mobile device.
To confirm the effectiveness of our approach, we also developed a prototype of the modified Java ME runtime environment that runs on a real mobile device, namely an HTC Universal smart-phone running Openmoko Linux and exploiting the PhoneME Feature Software MR2 Java Virtual Machine.
Link:
http://www.s3ms.org/
Please contact:
Fabio Martinelli, Paolo Mori
IIT-CNR, Italy
E-mail: {fabio.martinelli, paolo.mori}![]() iit.cnr.it
iit.cnr.it
Christian Schaefer, Thomas Walter
DoCoMo Euro-Labs, Germany
E-mail: {schaefer, walter}![]() docomolab-euro.com
docomolab-euro.com
Fabio Massacci
Università di Trento, Italy
Fabio.Massacci![]() unitn.it
unitn.it










