After more than a decade of research, system security and resilience is now the major technological barrier for the Cognitive Radio (CR) to be adopted by the telecommunication industry. New ideas are required to make CR networks secure and robust against attacks taking advantage the inherent characteristics of the CR functionality. This work explores key points that urgently need to be addressed.
Cognitive radio (CR) is a term with many possible meanings in the telecommunications literature of the past decade. Most commonly, a cognitive radio device is based on a software-defined radio (SDR), and has an adjustable front-end, which allows it to tune on different frequencies, power levels and modulation schemes. The SDR infrastructure has a programming interface that enables these configuration options. These, in conjunction with the context of operation (radio interference and noise, traffic demand, mobility levels, element status, location, etc) are made available to a decision-making entity, which selects the best configuration by solving an optimization problem with respect to some objective function. Further input is contained in a system knowledge base that codes the contexts encountered and maps them to specific radio configurations that can be used. This mapping can be done through a reasoning engine which is essentially a set of logical inferring rules (policies) and “reasons” (i.e. searches) for a proposed set of actions that will manipulate the current state of the knowledge base in an optimal way. In principle, the CR functionality may also include a learning engine making it capable of starting with no policies, and by utilizing a variety of classic Artificial Intelligence (AI) learning algorithms identify which configuration will work optimally in the current and future contexts.
While CR devices are built with components that have been well-established in the telecommunications and computer science disciplines, the existing approaches to provide robustness and effective security for a network of CR devices are inadequate. Due to the particular characteristics of the CR systems, new types of attack are possible and some of the well-known types increase in complexity. Therefore, new ideas are needed to make CR networks secure and robust against specific attacks, especially against those that are inherent to the CR functionality.
Specifically, sample attacks can target the inputs considered for the formation of the CR networks and the respective optimization problem, for instance attacks might compromise the accuracy of the context information sensed or the set of candidate nodes that may be involved in the network. One of the key features of cognitive radio is that sensory manipulation can lead to knowledge manipulation, meaning that malicious actions in the present can affect the radio performance in the future. Other attacks can target the outputs describing the CR network that should be formed even under unharmed inputs, eg, a set of nodes that should be involved, configurations that should be selected, etc. Finally, as in all wireless networks, attacks can be designed to lead the client devices to configurations that are inefficient in terms of energy and make them run out of batteries.
There is, therefore, the need for comprehensive and energy efficient mechanisms to discourage, identify and mitigate the attacks at all phases of the cognitive cycle, in order to obtain CR systems that are trustworthy, efficient and dependable. Furthermore, in this scope there is need for a new systemic evaluation of the robustness of a CR system, in order to set the requirements and expectations for a resilient CR network from a security viewpoint.
The targets of this joint work are to initially identify the threats at the different layers and to classify the major topics, such as jamming, sensory manipulation, belief manipulation, routing, etc , for each layer.
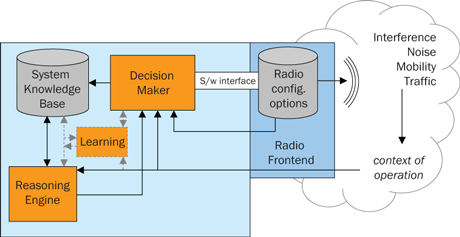
Figure 1: Components of a SDR-based Cognitive Radio.
Further on we aim to develop new mechanisms for detecting, isolating and expelling misbehaving insiders. Such malicious nodes may have all the credentials provided by an “off the shelf” security solution as the ones proposed to be applied in IEEE 802.22. This therefore requires the detection of abnormal secondary user operation through pattern analysis and node cooperation, since the feedback from the CR devices will enhance the efficiency required for such an Intrusion Detection System (IDS).
Improving sensory input can reduce the exploitability of cognitive radios in a cross-layer fashion. For example, if the CR could identify the difference between interference and noise, they would distinguish between natural and malicious RF events. Identification and quantification of potential gains from the interference identification is important in order to define more robust CR MAC policies. Furthermore, in a distributed environment, a network of cognitive radios can fuse sensor data to improve the quality of input for the cognitive engine. Such techniques should be designed with small information exchange requirements in order to be energy efficient, keeping in mind that the client CR devices will be battery operated.
This project is a joint effort by the Mobile Telecommunications group of the Department of Science and Technology in Linköping University and the Institute of Computer Science of the Foundation for Research and Technology-Hellas (FORTH-ICS).
Please contact:
Vangelis Angelakis,
Mobile Telecommunications, ITN-LiU, Sweden
Tel: +46 11 363005 begin_of_the_skype_highlighting +46 11 363005 end_of_the_skype_highlighting
E-mail:
Ioannis G. Askoxylakis,
FORTH-ICS, Greece
Tel: +30 2810 391723 begin_of_the_skype_highlighting +30 2810 391723 end_of_the_skype_highlighting
E-mail:









