Twenty-four new research projects are being launched by DG INFSO following the result of the first call for proposals in the area of 'secure, dependable and trusted infrastructures', which is part of the 7th Framework Programme (FP7) Information and Communication Technologies (ICT) theme. Most of the projects started on 1st January 2008 and all will be operational within the next few months.
Among the 24 projects, there are five Integrated Projects (IPs), one Network of Excellence (NoE), fourteen Focused Research Actions (STREPs) and four Coordination Actions (CAs). The duration of individual projects varies from two to four years and the funding is ranging from less than Euro 1 million (CAs) to more than Euro 9 million (some IPs). The projects cover an extensive range of hot security-related research topics in ICT. The overall focus of the research is on developing knowledge and technologies needed for building a trustworthy ubiquitous information society, based on secure and resilient network and service infrastructures. A central issue of the new research is the empowerment of end-users through proper handling of their digital identities and respecting their privacy when they interact in the digital world. The research topics can be broadly grouped into four closely inter-related thematic areas, with each project touching upon several areas (see figure).
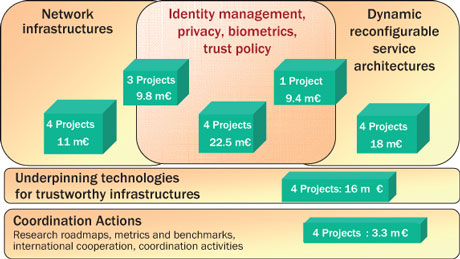
1. Dynamic, Reconfigurable Service Architectures
Modern IT systems tend to replace individual components and applications with compositions of services distributed over a network. It is vital to define and ensure trust, security and dependability properties when composing services, either at design time or dynamically at run-time. Four research projects investigate the implications of this paradigm shift in service-oriented architectures in terms of trust and security.
2. Network Infrastructures
Heterogeneous network infrastructures that are secure, resilient and able to cope with different attacks and threats are needed in order to deliver trustworthy and always available applications and services. Research funded in this area covers, on the one hand the need to design, build and maintain security in such network infrastructures. On the other hand, it covers threat prevention mechanisms with a focus on the early identification and modelling of emerging threats. This will enhance the ability of operators to detect anomalies and to counter possible cyber attacks.
3. Identity Management, Privacy, Biometrics, and Trust Policies
As users are bringing more and more of their corporate and private data within the realm of the Internet, they realise the potential, and also the risks that technology has created for the protection and management of sensitive interactions, information and data. Several projects investigate new technological solutions for the secure handling of digital identities and sensitive data by adopting a user-centric, privacy-enhancing federated identity approach. Specific research areas addressed include: new privacy and identity management schemes for social networking and Web 2.0 environments and for complex real-life applications like healthcare; novel solutions combining biometrics and crypto-hashing methods for fighting digital identity theft; new concepts in multi-modal biometric authentication; and innovative biometric authentication means for new mobile services.
4. Underpinning Technologies for Trustworthy Infrastructures
Four new projects, one of which is a Network of Excellence, will develop a number of technology building blocks underpinning trustworthy network and service infrastructures. These projects will mainly focus on: achieving further advances in cryptographic algorithms and protocols and their efficient hardware and software implementations; developing trusted computing architectures for embedded computing platforms; and, building tools to help programmers in designing and developing more secure and robust software.
Coordination Actions
Finally, four new Coordination Actions (CAs) will address sharing of knowledge and collaboration between researchers in various areas of ICT security. Two of them cover the coordination of research, respectively, in cyber-threat defence and in resilience measuring and benchmarking in computer systems and components. Another CA supports and coordinates international collaboration with a number of developed countries. A fourth one addresses the definition of new areas of work in ICT Security Research, to further EU's strategic thinking and positioning in the field.
Disclaimer: The content of this paper is the sole responsibility of the author and in no way represents the view of the European Commission or its services.
Link:
Synopsis of the new projects funded under FP7 in the field of ICT security:
http://cordis.europa.eu/fp7/ict/security/projects_en.html
Please contact:
Jacques Bus, Head of Unit "Security", DG Information Society and Media, European Commission
E-mail: Jacques.Bus![]() ec.europa.eu
ec.europa.eu









