by Gabriele Lenzini and Bob Hulsebosch
The Dutch Telematica Instituut has designed adaptive, location-based, and responsive authentication solutions for pervasive, ubiquitous, intelligent environments. This idea is validated with an intelligent coffee corner, where users can see - depending on their identity and authentication tokens - the position of their colleagues on a wall screen.
Identification and authentication strategies often combine different sources of information to determine the grade of accessibility of a service. The paradigms usually considered in identification and authorization are 'who a user is' (eg via biometric measures), 'what a user knows' (eg PIN), and 'what a user has' (eg smart-phones, PDAs). Traditional security systems are not always suitable for pervasive, ubiquitous intelligent environments, because they are often preconfigured to static behaviour, cannot be seamlessly and dynamically adapted to new constraints, and are too intrusive for the user.
Context-aware environments open the possibility of exploiting the automatic detection of users' identity tokens for a new generation of context-aware and proactive services that are less intrusive for users. The grade of access to a service is calculated depending on the user's identification and authentication level which, in turn, is determined by the number and quality of his/her identity tokens as detected by the environment.
Unfortunately, items such as badges, mobile and smart phones, and RFID tags can be stolen, forgotten or lost, with a consequent risk of identity theft. In controlled environments like buildings, location sensors can be set to detect a wide range of items. The authentication security can be improved by considering the amount of 'belief' in the identity of a user standing in a certain location, eg the area from which he/she tries to access a resource. For example, if the mobile phone identifies the user as being on the third floor (where the service is provided) whilst, at the same time, his/her badge has been detected on the ground floor, the belief in the user standing on the third floor is weak.
We studied the 'belief' in identity as a property with which to enhance identification and authentication of users. We calculated identification and authentication levels as a combination of the number and quality of the identity provided by a user, and of the belief we have in that user standing at a certain access point. If the belief is weak, the level calculated is low, and the security mechanism can either grant access with reduced privileges or ask the user for more identification tokens, such as visual identification. In this way we propose a responsive authentication, where users can be proactively requested for other, non-contextualized, tokens if the identification and authentication level that emerges is insufficient to grant full access to the resource.
We studied two implementations of 'belief'. The first is a probability-based implementation that uses a Bayesian algorithm to fuse the location information of the sensed identity tokens into a value expressing the probability of the user being in a certain location. The second is an implementation based on trust management that calculates the amount of trust the system places on the user standing in a certain location. Here, sensors are seen as independent recommenders that provide an opinion on a user being in a requested position, depending on what they have perceived in the environment. We obtained a very scalable solution by using Subjective Logics to model opinions and combine them into a trust value.
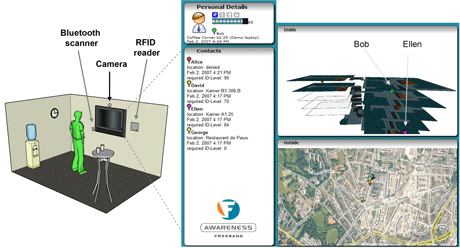
To validate our proposal we used an intelligent coffee corner in our institute (see Figure 1). The positions of a user's colleagues are displayed on a wall screen. These colleagues require that their position be shown only if the authentication level of the user is above a certain threshold. In our simulations so far, with the users tokens moving around, the level changes in accordance with prediction.
Ultimately, the system could learn the user's behaviour, eg based on sensed movement patterns, and use that as a source for identification and subsequent user-friendly access to resources. In order to prevent misuse, any deviation from normal behaviour will trigger an authentication alert and a request for better authentication from the user. We are now entering the demonstration phase, where the solution will be fully integrated into the coffee corner.
This research is part of the Dutch Freeband Project AWARENESS (context AWARE mobile Networks and ServiceS), which focuses on the design of an infrastructure for context-aware and proactive mobile applications. Our research partners are: Alcatel-Lucent, Ericsson Telecommunicatie, Telematica Instituut, TMSI, Univ. of Twente (CTIT), Roessingh R&D, Yucat and WMC.
Links:
http://www.telin.nl/
http://awareness.freeband.nl/
Please contact:
Bob Hulsebosch
Telematica Instituut, The Netherlands
Tel: + 31 53 4850498
E-mail: Bob.Hulsebosch![]() telin.nl
telin.nl
Gabriele Lenzini
Telematica Instituut, The Netherlands
Tel: + 31 53 4850463
E-mail: Gabriele.Lenzini![]() telin.nl
telin.nl









